Ransomware attacks can lock you out of your own computer in seconds. What’s worse is that even if you pay the ransom, there’s no guarantee of recovering your data.
And thanks to AI, cybercriminals are refining their attacks, and no one is immune.
Whether you’re an individual or a business, we will guide you through everything you need to know about ransomware attacks, including:
- what ransomware attacks look like;
- how to spot a ransomware attack
- 8 steps you can follow today to protect your files from hackers.
Let’s get right into it.
What is a Ransomware Attack?
Ransomware is a contraction of the words “ransom” and “software”. Basically, it’s a piece of software that will “lock your computer” until you pay an ransom.
More precisely, a ransomware attack will “scramble”, or encrypt your content (documents, videos, photos, app stored data etc.). Got a financial document you need to edit? Can’t access it. Got a video of your children on vacation? Can’t watch it.
Hackers will then contact you and demand a ransom. In exchange, they’ll promise to give you the key to decrypt your data, and regain access to all your files. But there are several issues here:
- firstly, the ransom isn’t cheap. The average ransomware payment was estimated at US$2 million in 2024 according to Sophos’s State of Ransomware 2024 Report;
- however, in recent years, attackers have started adapting their ransom demands to their victims. For example, they might “only” ask you a few thousand dollars ransom to increase the chances that you pay;
- finally, what’s to say the hackers will actually hand you access to your data? Why not demand even more money?

This makes ransomware attacks an extremely stressful attack to deal with. If you are a victim, there might not always be a way to recuperate your data (but more on that later).
Ransomware, just like other types of viruses, often make their way to your computer through phishing emails. They may also use various social engineering techniques to trick their victim into installing the nefarious software.
Ransomware attacks can be of 2 natures:
- Encrypting ransomware: incorporates advanced encryption algorithms designed to make files unreadable. The victims are requested to pay to obtain the key that can decrypt the blocked content.
- Locker ransomware: locker ransomware locks the victim out of the operating system, making it impossible to access the desktop and any apps or files. The victims have to pay to unlock their data.
3 Real-World Examples of Ransomware Attacks
It’s important to understand that ransomware attacks can target both corporations and individuals. In these next examples, we will look at several high-profile cases of such attacks, how they happened and the vulnerabilities they exploited.
The Colonial Pipeline Attack
In May 2021, the Colonial Pipeline ransomware attack became front-page news across the entire U.S.
Colonial Pipeline—one of the largest fuel suppliers in the U.S.—fell victim to DarkSide ransomware, a sophisticated malware developed by a presumed Russian cybercriminal group.
Thanks to a single compromised password leaked on the dark web, the attackers gained access to Colonial Pipeline’s IT network. In addition, some of the vulnerabilities that enabled the attack included:
- lack of multi-factor authentication (MFA or 2FA): the breached account had only a password for protection, making it easy for attackers to gain entry.
- flat network architecture: the IT systems were interconnected, allowing the ransomware attack to spread deeper into critical infrastructure.
- delayed incident response: the company discovered the breach on May 7 2021 but took time to respond, allowing the malware to spread and encrypt critical data.

This ransomware attack had major consequences on the American public, forcing a shutdown of the entire fuel distribution network, causing gas shortages across the U.S. East Coast.
In coordination with the FBI, Colonial Pipeline ended up paying a USD4.4 million in Bitcoin. Roughly half of the value of the bitcoins were later recovered.
You can learn more about the details of this ransomware attack on the US Department of Justice’s website.
The WannaCry Ransomware Epidemic
The WannaCry ransomware outbreak in May 2017 (also known as WannaCrypt) was one of the most widespread cyberattacks in history, infecting over 300,000 computers across 150+ countries within a single day.
The attack was powered by a Windows vulnerability called EternalBlue, which was stolen from the U.S. National Security Agency (NSA) and leaked by a hacking group called The Shadow Brokers.
WannaCry is what is called a “ransomware cryptoworm”:
- after infecting a computer, it would demand a ransom to be paid in Bitcoin (“crypto-“;
- it was also able to spread autonomously (“-worm”).
Some of the vulnerabilities exploited during this attack included:
- unpatched Windows systems: WannaCry targeted computers running outdated Windows versions (Windows 7, XP, Server 2003) that lacked critical security updates.
- self-replicating malware: unlike typical ransomware attacks, WannaCry spread autonomously, allowing it to infect entire networks without user interaction.
- slow response from organizations: Microsoft had released a security patch (MS17-010) two months before the attack, but many organizations failed to update their systems in time.
In the UK, the WannaCry ransomware attack brought the National Health Service (NHS) to a standstill, with dozens of hospital shutdowns.
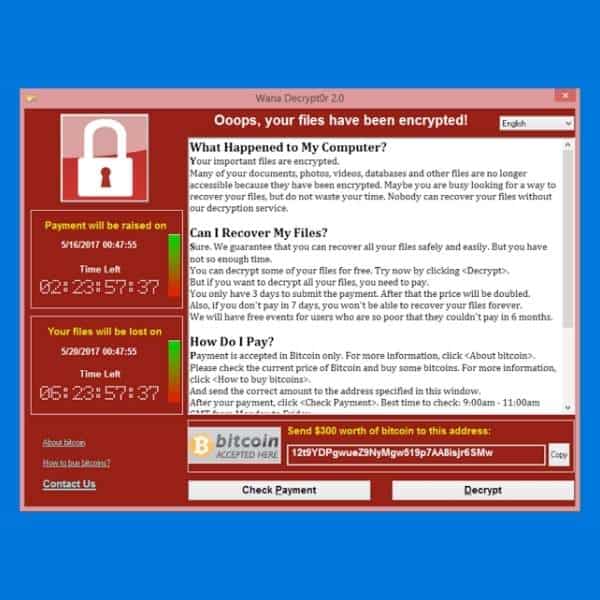
Many multinational corporations such as FedEx and Nissan were also forced to halt operations. The attack was later attributed to North Korea’s Lazarus Group, which used the ransom payments to fund further cyber warfare operations.
You can learn more about this attack in Microsoft’s dedicated blog post.
The Kaseya VSA Attack
In July 2021, ransomware developed by the REvil group was used to exploit a zero-day vulnerability in Kaseya VSA, a remote IT management software used by thousands of businesses worldwide.
By hacking Kaseya’s centralized software distribution system, REvil was able to push ransomware updates to Kaseya’s clients, infecting over 1,500 companies in one stroke.
The ransomware attack relied on several key vulnerabilities:
- the attackers discovered and exploited an unpatched flaw in Kaseya’s software before the company could address it;
- supply chain attack: Kaseya VSA was a trusted remote management tool, it therefore had direct access to client systems, making it easy to distribute malware without triggering security alerts.
- no segmentation in IT networks: many affected businesses had no separation between IT management tools and critical systems, allowing the attack to spread rapidly across networks.
What made this attack different from the others we covered is how ransomware-as-a-service (RaaS) is used to scale cybercrime.
In a RaaS model, ransomware developers create the malware but rely on affiliates to deploy it. In this case, REvil basically operates like a criminal SaaS company, selling access to its ransomware tools in exchange for a percentage of the ransom payments. REvil’s affiliates were responsible for targeting and breaching Kaseya’s systems. In return, affiliates kept a cut (often 60-80%) of any ransom paid, while REvil took the rest.
In total, more than 1,500 businesses worldwide were infected, including supermarkets, IT firms, and financial institutions.
The Impact of AI on Ransomware Attacks
The advent of ChatGPT and mass popularization of generative AI in 2022 has revolutionized many industries. Cybercriminals are not exempt from this trend, and have massively adopted the use of AI to refine the attacks.
Here are 5 ways in which AI is helping attackers make their ransomware attacks more sophisticated.
Highly personalized phishing emails
As explained previously, phishing emails remain one of the major attack vectors for ransomware attacks.
AI can now effectively scrape social media, emails, and leaked databases to craft tailored phishing messages that appear highly convincing. Instead of generic spam, victims receive emails mimicking real conversations, invoices, or urgent security alerts.
Polymorphic ransomware
Traditional ransomware is easier to detect because it follows known patterns. AI-driven polymorphic ransomware constantly mutates its code, making it invisible to signature-based antivirus programs. Every infection is slightly different, making it nearly impossible to blacklist.
Automated target selection and deployment
AI scans massive datasets in real time, identifying vulnerable businesses with weak cybersecurity and prioritizing high-value targets. Cybercriminals can then launch attacks on multiple companies simultaneously, maximizing profit with minimal effort.
In addition, AI-powered bots can automatically infiltrate corporate networks, search for vulnerabilities, and deploy ransomware without human intervention.
The use of AI-powered hacking tools has led to an increase in fully automated ransomware attacks, requiring less human expertise to execute.
AI-powered evasion
Modern cybersecurity tools rely on machine learning to detect ransomware patterns—but attackers are using AI against AI to evade detection.
For example, cybercriminals can train their ransomware against AI-powered security tools, testing different attack methods until they bypass detection.
Some AI-driven ransomware fakes encryption at first, fooling security tools into believing the attack has stopped, while it continues encrypting files in stealth mode.
Ransom negotiation
AI is even changing the way cybercriminals negotiate ransoms, making it more effective and psychologically manipulative.
Instead of human hackers handling negotiations, bots are now being used to communicate with victims.
These bots analyze victim responses, adjust ransom demands, and pressure companies into paying faster.
Ai is also used to scan financial records, insurance policies, and public earnings reports to calculate the highest ransom a company is likely to afford.
Victim of a Ransomware Attack: What Can You Do?
Have you been the victim of a ransomware attack? Then you should immediately follow these 3 steps:
- Stop the spread. The first move is to cut off the attack. Ransomware can quickly infect entire networks, so every second counts. Immediately disconnect your device from Wi-Fi, Ethernet, and external storage (USBs, backup drives). If you’re on a corporate network, alert IT security immediately so they can contain the threat before it cripples the entire system.
- Know your enemy. Not all ransomware attacks are the same. Some have known decryption tools, while others may delete your files permanently even if you pay. Take a screenshot of the ransom note—this often contains clues about the attack. Then, use online tools like ID Ransomware (https://id-ransomware.malwarehunterteam.com/) to identify the ransomware variant. You can also check the No More Ransom Project (https://www.nomoreransom.org/) to check if a free decryption tool exists.
- Report the attack. Before paying any ransom, involve cybersecurity professionals and law enforcement. Paying will not guarantee file recovery. Report the attack to the FBI’s Internet Crime Complaint Center (IC3) (https://www.ic3.gov/), as well as your country’s cybersecurity agency (CISA in the U.S., Europol, etc.). Finally, engage your IT team or cybersecurity provider.
However, be aware that not all ransomware can be decrypted back. In many ransomware attacks, the data is unfortunately lost. That is why prevention remains your best line of protection against future attacks.
8 Tips to Prevent Ransomware Attacks
By now, you will have understood the very real threat that ransomware attacks pose. So let’s go over 8 easy-to-follow tips you can put in place to prevent such attacks.
#1: Regular backups
Backups are by far the best way to protect yourself against ransomware attacks … as long as you do them efficiently.
For each backup, it is crucial to make several copies of your files and to keep them on different media. You should ideally store each one separately and in different locations. Ideally, one should be kept offline (on a secure external disk), and another one could be left on a secure and private cloud service.
Also, avoid leaving the backup media (e.g., external hard drive) connected to the computer system after a backup. In case of infection of your system, the external drive would be at risk of infection too, rendering your backup useless.
Read our tips to back up your data securely to be sure to make efficient backups!
#2: Use up-to-date software
Software updates often contain “security patches” intended to address vulnerabilities that hackers could exploit to launch cyberattacks (including ransomware attacks).
That’s why it’s essential to download updates for these software, devices, and peripherals immediately upon receiving notification of their existence. Because if you have received this notification, you’re not the only one… Now, hackers know there is a flaw in the device or software in question.
Another good idea is to restrict the programs installed on your computer or system to the bare minimum. Uninstall any unused software. Don’t forget to remove as well outdated plugins from your browser. This also applies to your smartphone: uninstall any apps you no longer use.
#3: Use the Principle of Least Privilege (PoLP)
To prevent ransomware attacks, you can also follow the PoLP. This means splitting your device/computer system usage into two separate accounts:
- a standard account you’ll use on a daily basis, including the bare minimum functionalities;
- an admin account allowing you to access to the core of your device/IT system (to change settings, install or remove software, for instance). It’ll give you full operating privileges on the system, and you’ll log in to it only when you need to perform such tasks.
In the event of a ransomware attack, the damage will be limited to your standard account. The ransomware will not be able to access core components of your computer because those accesses are controlled by the admin account.
#4: Detect and avoid phishing attempts
Many ransomware attacks are initiated by phishing, spear-phishing or whaling emails, or smishing. And it is often by downloading an attachment contained in these messages that victims allow the ransomware to break into their computer, phone, or computer system.
That’s why you should only open attachments and links issued from truly trusted sources. To make sure you follow this advice, avoid clicking on a link in an email. Even a seemingly innocent mention such as “click here to unsubscribe/unfollow” can hide dreaded ransomware. Instead, log on to the relevant website using the URL you usually use.
#5: Say no to macros
Never open a Microsoft Office file containing macros without having obtained beforehand confirmation from the sender of the message that the file really comes from them and that these macros are not harmful.
#6: Install a reputable antivirus to detect ransomware attacks
It goes without saying that you should protect your device against malware with an antivirus. Unfortunately, the protection offered will be limited since an antivirus can only recognize malware already detected elsewhere. But at least you can avoid already known ransomware attacks, which is already a good thing.
#7: Use a VPN
It is useful to use a VPN when surfing on public Wi-Fi networks. Indeed, these networks offer no protection against hacking and are very popular with hackers for this reason. Using a VPN will prevent potential data interception that could be used to infiltrate your devices or computer system.
#8: Use a virtual machine
Virtual machines are mainly used to duplicate an IT system to test new software, or run two separate operating systems within the same computer.
But they can also be used to prevent any attack from malicious software. In this respect, they can therefore help you avoid ransomware attacks. However, you should know that they are not always effective. Powerful ransomware can be particularly dangerous.
Preventing Ransomware Attacks: How Mailfence Can Help
That’s it for this guide on ransomware attacks! Hopefully you now have a better understanding of how these attacks operate, and what you can do to protect yourself.
Are you ready to take your personal cybersecurity to the next level?
Then your first step should be to get a private and secure email provider. Unlike Gmail or Yahoo, Mailfence puts your privacy and security above profits. In particular, we are proud to offer:
- Advanced security tools: end-to-end encryption, symmetric encryption, digital signatures, encryption at rest and a lot more.
- No tracking or advertising. We do not use any third-party advertising or marketing trackers. We do not track your activity in the application. Mailfence is completely free from ads.
- Strict privacy laws. Mailfence’s servers are based in Belgium, with strong laws protecting privacy. Only a valid Belgian court order can force us to release data.
Interested in reducing your digital footprint and taking your cybersecurity to the next level? Create your free account today!