Symmetric encryption is a core concept in cryptography.
In a nutshell, symmetric encryption uses a single key for both encrypting and decrypting data.
While that may sound complex, it’s actually really simple! You don’t need any knowledge of encryption algorithms or advanced computer science. This method is valued for its straightforwardness and speed, making it widely used for securing information.
In this guide, we will cover:
- what symmetric encryption actually is;
- the pros and cons of using symmetric encryption;
- how to send a password-encrypted email with Mailfence;
… and a lot more! So let’s get started.
What is Symmetric Encryption?
First things first, let’s define what symmetric encryption actually is.
Symmetric encryption is an encryption method that uses the same key for both encrypting and decrypting data between parties.
Sending a password-protected PDF or an email that requires a password to read it can involve symmetric encryption.
Practically speaking, this means both parties use the same “secret” (in most cases a password) to decrypt the email or file. This is also why this encryption method is called “symmetric”. Check out this guide to learn what sets it apart from asymmetric encryption.
Believe it or not, symmetric encryption is actually one of the oldest forms of encryption.

For example, the Spartans used the Scytale cipher around 500 BCE. This cipher involved wrapping a strip of parchment around a rod to encode messages.
In the 20th century, symmetric encryption advanced. The Enigma machine is a notable example. Used by the Germans in World War II, it created complex ciphers with rotors and plugboards.
These methods might seem completely different from protecting a file with a password. However, the core mechanism is the same. Both sender and receiver agree on an encryption method and use the same “key” to encrypt and decrypt the information.
Today, symmetric encryption is a cornerstone of cryptographic practices. It supports many security protocols and systems.
How Does Symmetric Encryption Actually Work?
The keys, in practice, represent a shared secret between two or more parties.
As long as both the sender and the recipient know the shared secret, they can encrypt and decrypt all messages that use this shared secret.
In practice, this is how a symmetric encryption might look like:
- The message is encrypted using a symmetric key derived from the user password (via a S2K function) on the front-end. The back-end stores the encrypted message.
- The recipient receives the access URL of the encrypted message.
- The recipient clicks on the access URL and provides the right password (the password chosen by the sender). It will be used to derive the symmetric key, which in turn decrypts the message.
This means symmetric encryption is mostly abstracted from the user experience. The only requirement is to use a program that supports it.
The other requirement is that both the sender and receiver know the secret key. This means you need to share your password by some other means (using an end-to-end encrypted messaging service like Signal for example).
Pros and Cons of Using Symmetric Encryption
Advantages of symmetric encryption
Ease of use
The main advantage of symmetric key encrypted emails is the ease of use. You can send encrypted emails to any person without having to make sure that this person has a (asymmetrical) public key or a special program/add-on/plugin to decrypt the message.
You can send secure password-encrypted messages to anyone, without any need for technical know-how about encryption. The only thing you will need to do is communicate a shared secret/password to the recipient of your message.
Sender control
The messages remain hosted on servers of the sender service. It does not transit via the open internet. They are stored encrypted on our servers and are kept there until they are retrieved by the recipient or deleted by the sender.
Accessibility
After receiving the secure link, the recipient can access the message from any device (with a modern browser). The sender can set an expiration date for the secure link, which means the recipient can only use that link to decrypt and read the secure message before it has expired.
Disadvantages of symmetric encryption
Losing the shared secret/passphrase
The main issue with shared secret/passphrase is that you need to exchange it with the receiver of the encrypted message. You can do this over the internet or via an alternative channel such as SMS, phone, …
The danger is that if the shared passphrase falls into the wrong hands, anyone who knows it will be able to decrypt the message.
One solution to this problem is asymmetric encryption (OpenPGP-based), which uses a key pair. A public key is freely available for anyone to send you a message, while a private key is kept secret by its owner.
Platform-specific
Password-encrypted emails require trust in the service which manages and provides this feature. The recipient must view the message on the sender’s portal.
In case of an unreliable or breached sender service, there could be a significant security issue.
Also, there are no digital signatures (except the traditional DKIM header for anti-spoofing reasons) on these encrypted messages. For that, you should use an asymmetric signature (OpenPGP-based).
Restricted capabilities
Using symmetric might also include some restrictions in functionalities, such as:
- Attachments can only be sent with the original (or first) email in a conversation. Recipient(s) cannot add attachments in response email.
- You cannot forward password-encrypted emails.
- Neither party (sender or recipient) can change the sender address and the recipient address for a given email conversation thread.
Does Mailfence Support Symmetric Encryption?
Of course! In line with our design philosophy of offering control and freedom, the use of this feature is not restricted. Therefore:
- All Mailfence users can use password-encrypted messages with other Mailfence users.
- All Mailfence users can use password-encrypted messages with non-Mailfence users.
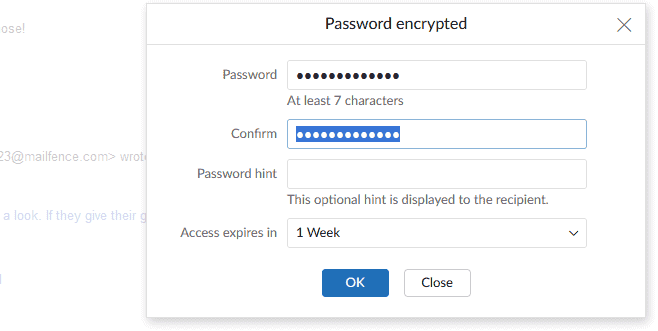
To send a password-encrypted email, follow these simple steps:
- simply select “Encryption” next to the “Send” button;
- type in your password and confirm it;
- include a hint that the receiver will be able to read (optional)
- set an expiration date for your email (optional)
Best of all, you can also use symmetric encryption on our mobile app!
If you haven’t yet, make sure to download our free mobile app for iOS and Android!
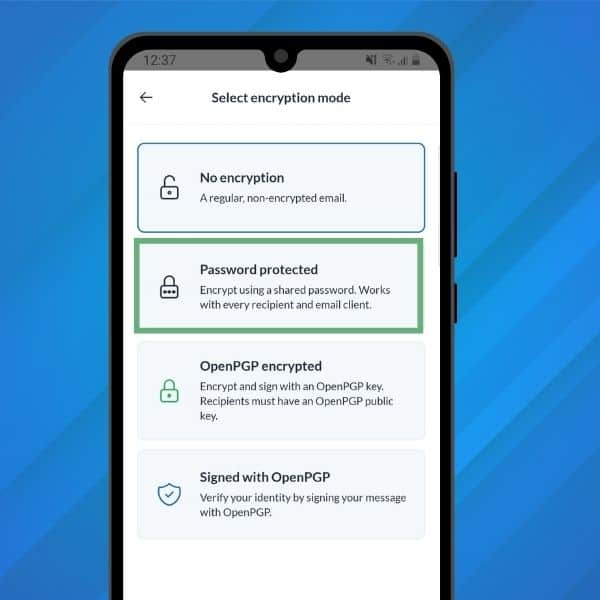
All of the encryption/decryption process happens on the front-end (in your browser) using an open-source and security-audited library. The symmetric key is encrypted with the password provided by the user and is never exposed to the backend in cleartext.
Check out this guide for more info on how to send a password-encrypted message.
Note: please do not use your account password, or your OpenPGP keypair passphrase, as the password for symmetrically encrypted messages.
Email Password Encryption Best Practices
Feeling ready to send your first password-encrypted messages? Then here are some best practices you should always follow.
Key management
Symmetric encryption is only as safe as the password you select. That is why you should always generate strong keys (i.e. strong passwords) and avoid predictable patterns or weak keys.
It is also vital to store your keys securely. Keep keys in a protected environment, such as hardware security modules or secure key management services. Never store keys in plain text files.
Finally, regularly change encryption keys. This reduces the risk of key compromise. Implement a rotation policy that minimizes disruption.
Sharing secret
Make sure to always share passwords through secure channels. Use encrypted messaging services or secure key exchange protocols. Avoid sharing keys over insecure methods. Also, as much as possible, limit the access. Only authorized individuals should have access to encryption keys. Use role-based access control to enforce this in your organization.
User training
Educate users on the importance of encryption and provide training on creating strong, unique passwords and safeguarding them. For more information, check out our full email security and privacy course.
Symmetric Encryption: Final Words
That’s it for this guide on symmetric encryption. Hopefully, you found it useful, and now feel confident to start sending your first password-encrypted emails!
Got any questions? Anything unclear? Feel free to drop us a line at support@mailfence.com
Symmetric Encryption: FAQs
A digital signature is a secure electronic signature that uses cryptographic methods to verify the sender’s identity and ensure a document or message has not been altered. It works by encrypting a cryptographic hash of the message with the sender’s private key, which the recipient can verify using the sender’s public key.
An electronic signature is any electronic form of agreement, such as a PIN code or an image of a signature. In contrast, a digital signature uses cryptographic algorithms to ensure identity verification, message integrity, and non-repudiation, making it far more secure.
Yes, digital signatures and E2EE can work together. Digital signatures verify the sender’s identity and message integrity, while E2EE encrypts the message content to keep it confidential. Mailfence combines both features to ensure maximum email security.
Digital signatures authenticate the sender, protect the content from tampering, and provide legal value to the communication. They are particularly useful for secure, professional, or legally significant communications.




