If you’re like most people, you probably don’t know much about social engineering attacks. Or do you believe it only aims to dupe unsuspecting victims to steal some money?
You may not realize that social engineering techniques can take many forms. And anyone can fall victim to one – even you.
In this guide, we will cover everything you need to know about social engineering attacks, including:
- what a social engineering attack is;
- the different forms a social engineering attack can take;
- how to quickly detect a social engineering attack;
- and most importantly, how to avoid falling victim to one!
So without further ado, let’s explore!
What is Social Engineering?
First things first. What is social engineering?
Social engineering gathers many techniques to exploit our human nature to induce behaviors and mistakes that will lead to weakened security.
It will allow cybercriminals to access information, money or control what they’re looking for. It’s not a unique kind of attack but rather a group of different scams that share several similarities:
- Scammers attempt to obtain sensitive information or money;
- They exploit trust and human behavior to manipulate their victims and achieve their goals;
- They exploit their victims’ lack of knowledge and their inability to implement security measures to protect themselves;
- Their schemes often involve using personal information (identity theft) to appear more authentic.
Remember the ancient Greeks’ “gift” horse to the city of Troy? An excellent real-world example.
At the heart of every social engineering attack lies manipulation.
Forget about brute force tactics. With social engineering, attackers use manipulative tactics to lead their victims into compromising themselves or the security measures they rely on. Scammers connect with their victims to infuse confidence and influence their actions.
As attackers become more familiar with their targets’ motivations, they can craft persuasive tactics to lure them into potentially destructive behavior.
And it works: many cybersecurity incidents are successful social engineering schemes carried out by external attackers. They play with human weakness to make their victims unwittingly provide access to sensitive information or money.
How Do Social Engineering Attacks Work?
As we already mentioned, social engineering relies on manipulation. It can take on various forms (as we’ll explore later).
However, every social engineering attack will exploit one of the following human traits.
Trust
The hacker will send a message spoofing an organization’s communication codes, such as its logo and other brand features (fonts, writing style, etc.).
They want to trick the victim into doing things they would routinely do with this specific organization (click on a link, download a file, etc.) because they trust it and just don’t challenge the message’s origin.
Compliance with the authority
Obedience to authority is another human trait social engineering tactics can exploit.
Pirates will impersonate a high-ranking individual or a government agency to induce their obedient target to do something.
Sense of urgency and/or fear
People often act without thinking when faced with a sudden sense of panic.
They are vulnerable to social engineering scams that prey on such emotions. These deceptive tactics leverage fear and urgency in various ways:
- false credit card alerts;
- virus warnings;
- exploiting one’s FOMO (fear of missing out).
The panicking victim is lured into taking action without taking the time to consider the implications of their actions. Often, under stress, they will forget to double-check the request’s legitimacy.
Greed
You wouldn’t refuse a gift, would you? Scammers understand this.
This is why many scams leverage our greed to attract us with money rewards, free iPhones and other prizes.
Ever heard of the “unexpected inheritance” scam? This is a classic phishing attack promising you a large sum of money from a distant relative or a wealthy benefactor. The money is supposedly blocked for some obscure reason… All you need to do is pay the administrative fees to get the money.
Sound too good to be true? That’s because it is! This is a perfect example of a scam using our attraction to money, gifts, or easy rewards.
Generosity
Finally, our generosity is often exploited in social engineering attacks.
Attackers exploit generosity by researching social media to find out what matters to you and impersonating organizations linked to your causes. For example, they might pose as a charity you support to solicit donations.
Social Engineering Attacks: What Do They Look Like?
There are many kinds of social engineering attacks with subtle varieties. Here are some of the most common ones.
Phishing scams are the most common types of social engineering attacks used today. Phishing scams rely on emails to make a connection with the target. Other specific types of phishing attacks exist such as:
- smishing, a phishing attack that relies on SMS;
- vishing which relies on actual phone conversations;
- spear phishing which targets specific individuals with personal information to make it appear legitimate;
- whaling attacks which are phishing attacks that target high-ranking executives.
Pretexting is another form of social engineering where attackers focus on creating a plausible pretext, or a fabricated scenario, that they can use to steal their victims’ personal information.
Baiting is, in many ways, similar to phishing attacks. However, what distinguishes them from other types of social engineering is the promise of an item or good that hackers use to entice victims, just like the Trojan horse.
Similarly, quid pro quo attacks promise a benefit in exchange for information. This benefit usually assumes the form of a service, whereas baiting frequently takes the form of a good.
Scareware aims to make its victims believe a virus infected their device, and they need to buy or download specific software to fix it.
Watering Hole Attacks happen when attackers compromise a website frequented by a specific group of users. When these users visit the site, their devices are infected with malware.
A Honey Trap is when attackers create fake social media profiles to befriend targets and extract confidential information through deceptive relationships.
Finally, Reverse Social Engineering creates a situation where the victim seeks help, allowing the attacker to pose as a helper and extract sensitive information.
Physical phishing attacks
Phishing attacks can also happen in the “real”, physical world.
The most common form is called “shoulder surfing“. This is when someone observes directly over your shoulder to gain information such as passwords or PINs after luring them into doing an action necessitating credentials.
Another social engineering attack type is tailgating, where someone seeks physical entry to a restricted area where they are not allowed to be.
Common characteristics of social engineering attacks
Most of these social engineering attacks share the following characteristics:
- Personal information: attackers seek information such as names, addresses, and social security numbers.
- Link shorteners or embedded links: these links actually redirect users to suspicious websites in URLs that appear legitimate.
- Malware: social engineering can also be used to set up malware either on top of stealing the victim’s credentials or with the sole purpose of compromising the victim’s device.
Social Engineering Attacks in the Real World
Now that we’ve covered the theory, let’s look at a few real-world examples of social engineering scams.
The “Fake CEO” Fraud
In 2016, the Austrian aerospace firm FACC lost approximately €50 million due to a social engineering scam known as “CEO fraud.”
Cybercriminals posed as the company’s CEO and sent an email to the finance department requesting an urgent wire transfer.
The email appeared legitimate, containing the CEO’s typical writing style and even a forged email signature. Without verifying the request, an employee transferred the funds to an offshore account controlled by the attackers.
This case highlights the importance of verifying financial transactions through secondary communication channels before proceeding. It also highlights the value of using digital signatures. With Mailfence, you can digitally sign your emails using encryption, which proves irrefutably that you are indeed the author of that email.
The Twitter Bitcoin Scam
In a high-profile social engineering attack, cybercriminals gained access to Twitter’s internal tools by impersonating IT support staff.
They manipulated employees into providing login credentials, allowing them to take control of several high-profile accounts, including those of Elon Musk, Bill Gates, and Barack Obama.
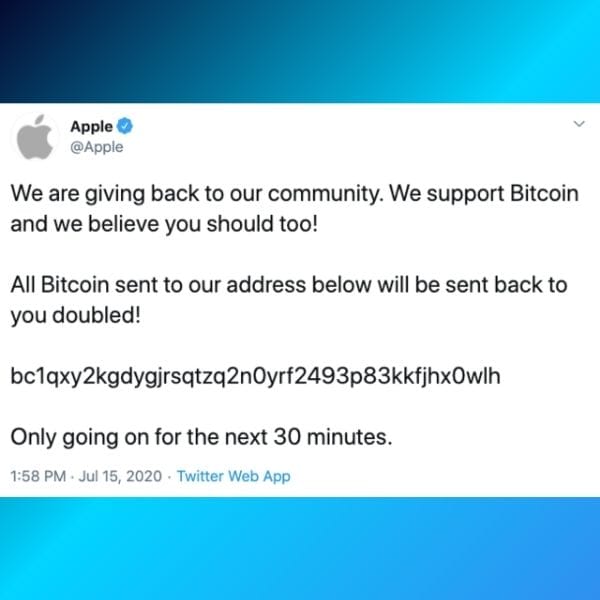
The attackers used these accounts to post fraudulent Bitcoin giveaways, deceiving followers into sending cryptocurrency. This attack demonstrates the dangers of over-reliance on internal credentials and highlights the importance of multi-factor authentication and employee training on social engineering tactics.
Want to learn more? Check out this report by Verizon, which explores the cost of data breaches in the business world.
The Role of Social Media is Social Engineering Attacks
With the emergence of social media platforms, scammers have unprecedented access to your personal information. They no longer need to hack your email account – everything is public on Instagram, TikTok and X!
This practice is known as “social media reconnaissance.” By analyzing publicly available posts, attackers can:
- Identify an individual’s workplace, job role, and professional contacts.
- Extract personal details such as birthdates, pet names, or favorite locations, which could be used for password guessing.
- Learn about upcoming travel plans to time an attack when the victim is less vigilant.
With all this information at hand, attackers can hyper-customize their phishing attempts. This increases considerably the likelihood of success.
Common Social Media-Based Attacks
With a wealth of information on you, attackers can easily engineer a spear phishing attack. Through DMs on Instagram or X, they can appear to come from a trusted source, enticing victims to click malicious links or download malware.
Attackers also know where you work, since when, where you worked previously etc. thanks to LinkedIn.
With this information, attackers can impersonate company executives on LinkedIn and attempt to initiate fraudulent transactions. They can also pose a recruiters, sending fake job opportunities to extract personal information from job seekers.
To protect yourself, here are a few steps you should follow:
- Set strict privacy settings on personal and professional accounts.
- Avoid oversharing personal and work-related details. This includes places you’ve visited or plan to visit, names of relatives etc.
- Regularly review and remove connections with unknown or suspicious accounts.
- Delete any social media account you no longer use. Make sure that all your information is deleted (which is your right).
Social Engineering Attacks: How to Stay Safe?
Now that we’ve identified the different forms of social engineering and their characteristics, let’s talk about how to avoid them!
What follows are various steps you should take to identify social engineering attacks, and protect yourself from future ones.
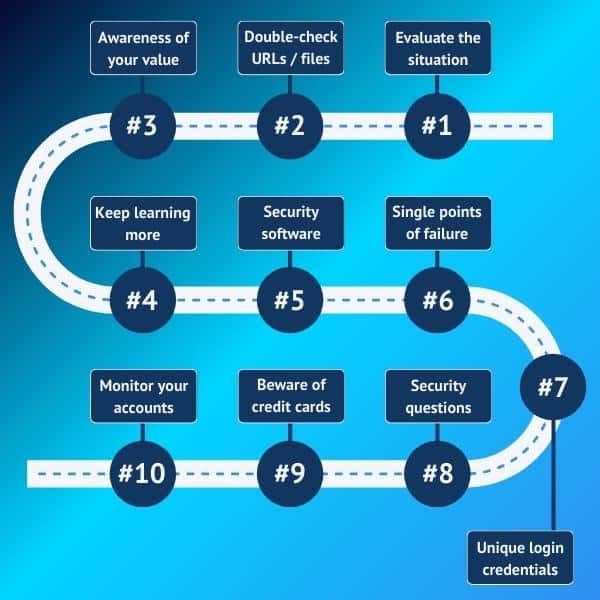
#1: Take your time to evaluate the situation
Take the time to consider the whole situation and examine the message carefully, even if it is quite worrying.
- Is this message unexpected?
- Does it originate from where it’s supposed to?
- Ensure you are interacting with trusted contacts by confirming their identity. Whenever possible, contact your sender directly to make sure they sent what was received.
- Also, check for spelling mistakes, oddities in the logo, or other revealing details. Does this organization usually communicate in this manner?
- Again, in case of any doubt, take your phone and call the official number or the number you’re used to call (and not the provided number) to get more information. This is a vital step with regards to financial transactions!
#2: Check the URL or file before clicking
Never, ever click on an attachment or link in email without double-checking.
Any attachment in a message can hide a virus or some other kind of malware, such as ransomware.
A link in a message can lead you to a staged website set up to steal your data or infect your device with malware.
Before clicking on them, inspect them carefully:
- Is there any message or a prompt indicating the attached file contains macros? If yes, make sure you don’t enable macros to view the file.
- Were you expecting this file or link?
- In doubt, don’t hesitate to check and ask the sender directly if it’s coming from them (contact them with your usual means of contact).
- If in doubt, DO NOT click! Ask a colleague, friend, or family member if you are unsure. Or refer to an IT expert if you don’t feel comfortable assessing the situation.
#3: Be aware of your valuables
Even if you’re not a millionaire, you own many things that could arouse the greed of cybercriminals:
- your data (which can be sold on the dark web);
- software access you have in the company you work for;
- detailed social network accounts, with numerous pictures, and comments revealing what you like, what you support, etc.. This means it will be straightforward to profile you and determine the appropriate strategy to target you. Therefore, be careful with what you share on social media.
Take the time to look at your privileges, communications on the net, and try to understand the potential you offer for any scammer. Being more aware of this can improve your ability to detect social engineering attacks.
#4: Learn about social engineering scams
Congratulations! Just by reading this guide, you’ve already made yourself less vulnerable to social engineering attacks.
Education is key to avoiding social engineering attacks.
As individuals, we are in most cases at the origin of a potential attack due to our lack of awareness and knowledge.
If you want to learn even more, you can check out this guide on the 7 biggest email security mistakes to avoid. Or you can check this guide on tips to protect your computer, or follow our free email security and privacy awareness course.
#5: Use security software to avoid spam and phishing emails
To protect your device and your data from cyberthreats and intrusion attempts, you must use an antivirus and make periodic backups.
But you must also use a secure email solution to ensure messages coming into your inbox don’t include any malware or any malicious part, and to block them if that’s the case.
Emails are one of the most common gateways for hackers. So make sure you have MFA activated, and get accustomed to sending encrypted emails that are digitally signed.
#6: Avoid single points of failure
A single point of failure is a common term used to describe having all your eggs in one basket. If that point gets breached, all your data is compromised. This is why you should avoid connecting all your accounts with Facebook or Gmail.
The more intertwined and dependent your accounts are, the more damage a security breach can cause you.
#7: Unique logins and secure passwords
Linked to #6, use different logins for each service and strong, unique passwords. Consider using email aliases and password managers to manage your credentials.
#8: Get creative with security questions
This one might sound trivial. But the additional security questions websites ask you are to, usually, set up a 2-step verification (2SV) security measure.
So be creative and avoid easily guessed answers such as your date or place of birth. A hacker will find those in a few minutes. Also, do not confuse 2SV with Multi-Factor Authentication (MFA) or TFA which we strongly suggest you set up anyway.
#9: Use debit cards wisely
If you use a debit card and a hacker gets access to the number, your entire bank account could be drained. You can further secure your debit card by not storing card numbers on websites or using disposable or virtual card numbers (offered by Citibank, Bank of America, and Discover).
#10: Frequently monitor your accounts
Be on the lookout for both identity theft and credit card fraud. Regularly check in with your account balances and credit score.
Last Word on Social Engineering Attacks
This wraps up our guide on social engineering attacks. Hopefully, you now have a better understanding of what social engineering is and how to detect them.
Make sure to send this guide to your friends and family too! To more people are aware of social engineering tactics, the less victims there will be. Finally, if you’ve got any questions, feel free to reach out to us at support@mailfence.com
Want to dive deeper? Check out this report by IBM, which highlights how cybercriminals exploit people’s identity for their attacks.
Social Engineering: FAQs
A social engineering attack manipulates human behavior to trick individuals into revealing sensitive information, granting access, or taking actions that compromise security. It often exploits trust, urgency, fear, or greed.
Some common types include phishing (email scams), vishing (voice-based scams), pretexting, baiting, scareware, and physical attacks like shoulder surfing or tailgating. These attacks can appear legitimate but aim to deceive.
To spot an attack, evaluate unexpected requests carefully. Check the sender’s identity, inspect links or files for suspicious elements, and watch for urgent or emotionally manipulative language. When in doubt, verify directly with the sender.
Stay cautious with personal information, use strong passwords, enable multi-factor authentication (MFA), and regularly monitor your accounts. Always double-check suspicious messages and avoid sharing passwords or data over insecure channels.