Phishing is a form of social engineering attack where cybercriminals pose as trusted sources to trick victims into revealing personal data or downloading malware
According to the National Institute of Standards and Technology (NIST), there are more and more phishing attacks each year, with a staggering rise of 61% since 2021.
These statistics show the prevalence of phishing attacks in 2023 and the need to protect yourself against them. Discover how phishing works, how to avoid it, and how to protect yourself and your company.
What is Phishing
Phishing (pronounced “fishing”) is a kind of identity theft. In these kinds of social engineering attacks, individuals or businesses are deceived to steal sensitive information or spread malware. These attacks often occur via email, with cybercriminals pretending to be trusted sources.
Common phishing deception tactics
Deception can be :
- The impersonation of a person or an organization you know, such as your bank or one of your coworkers,
- Fake URLs that mimic legitimate sites to capture credentials that mimics a genuine one you trust. This staged website will have been set up to get user’s credentials.
- Some seemingly useful files you’ll be invited to download, containing a Trojan horse hiding malicious software (malware).
If it’s the latter, the hidden malware can be :
- Spyware designed to collect data and spy on you,
- Malware designed to create a vulnerability, such as creating a backdoor in your IT system or converting your device into a zombie device,
- More frequently these days, ransomware, malicious software designed to freeze the victim’s device. To unlock it, you’ll have to pay a ransom.
Phishing attacks: What Do They Look Like?
There are several types of phishing attacks, depending on the tactic adopted by the hacker to get in touch with his victim :
- Classical phishing : The “phishermen” send massive emails to random people. These messages are all identical and they contain a link pointing towards a spoofed website to induce the reader to leave his credentials. Or they invite the addressee to download an attached file infected by malware.
- Spear Phishing: A phishing attack that targets organizations and specific individuals instead of sending bulk emails
- Smishing: Phishing attack that, instead of emails, uses SMS text. Hence the combination of words SMS+phishing
- Vishing: This phishing attack involves the perpetrator voice (through a phone call) to use social engineering into completing an action.
- Whaling: An attack that targets “whales” such as senior & executive members of an organization. They will usually be induced to execute an action like the transfer of a large amount of money, leading to tremendous rewarding for the attacker.
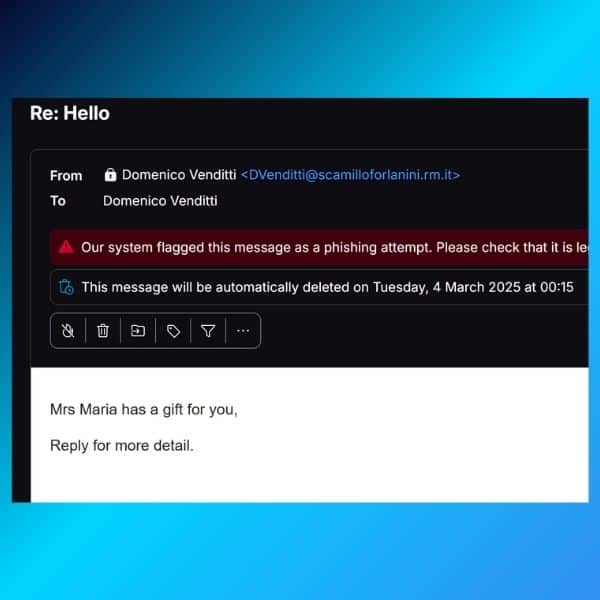
Here below are two examples of phishing emails:
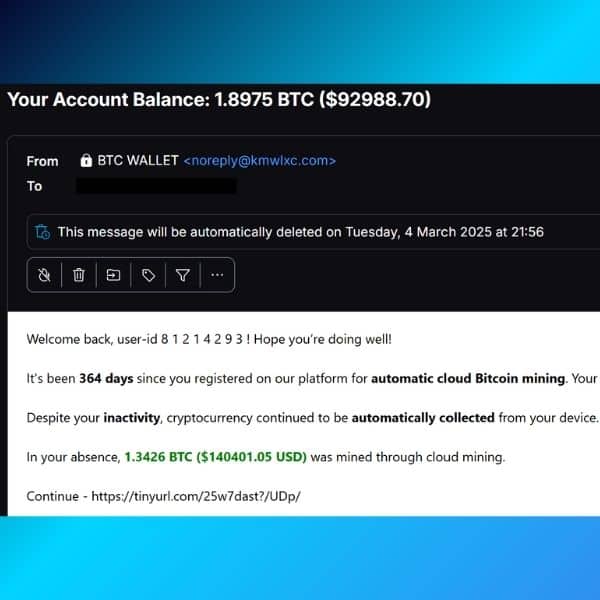
In the first example, the attackers are hoping you click on the provided link. The actual destination of the link is hidden thanks to the URL shortener.
In the second example, they are hoping to engage in a dialogue with you. Pro-tip: the second email has the same From and To fields. This means the real receivers (such as yourself) are all in BCC, meaning this email was probably sent to hundreds of people simultaneously.
Phishing attempts at Mailfence
Here at Mailfence, our users are also sometimes victims of phishing attempts. Attackers will usually use email spoofing to pretend to send a notification email on behalf of Mailfence. Here’s an example:
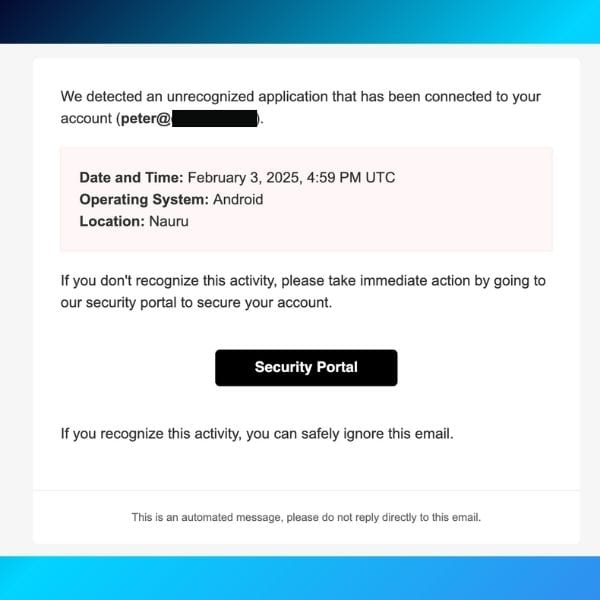
In this phishing attempt, attackers create a fake notification alert. The goal is to make you believe someone has accessed your account. By clicking on the link, you might inadvertently download malware. Or you could be re-directed to a fake Mailfence website that will try to steal your login credentials.
What to do in this case? Follow these steps:
- never click on a link or open an attachment before proceeding with the following checks;
- double-check the sender’s email address. Make sure the domain name is indeed @mailfence.com (in this case, it is not);
- hover over the link to see the full URL. If it is not a Mailfence domain, do not click on it.
How to recognize a phishing message?
Apart from ensuring you install an anti-spam filter and security software, the best way to combat phishing scams is to identify them.
Spelling mistakes and bad grammar in an email used to be a good telltale of a phishing attack. But nowadays, phishing attacks are more and more sophisticated, and phishing emails are often perfectly written.
You’ll have thus to focus on other details revealing an attempt to deceive you:
- Links in email. Take the habit of hovering over any hyperlinks sent in an email or SMS to check that they match the site page it’s meant to lead you to as typed in the message. Mismatched URLs (or misleading domain names) can also lead you to .exe files embedding malware.
- Links included in an email inviting you to connect to a website. Be especially cautious with any “clearance” or “outlet” website seemingly linked to a legitimate renowned retail portal, for instance. It could be a lookalike website created to steal your ID or some money.
- Threats – Have you ever received a threat that your account would be closed if you didn’t respond to an email message? Cybercriminals often use threats. They will send you a fake alert telling you your security has been compromised, a service is about to be terminated due to your inaction, or your banking account is overdraft.
- Messages spoofing popular websites or companies. In case you receive a message from a trusted organization, a coworker, or a friend requesting you to do something, pay attention to:
- Any request for personal information;
- An offer too good to be true, or some money you should receive or send;
- Any action you didn’t initiate.
Anything which doesn’t look right should arouse your suspicion. Even emails seemingly coming from specific types of organizations, such as charities or government agencies, can be dangerous. Attackers often take advantage of current events and certain periods of the year, such as:
- Natural disasters (e.g., earthquakes, hurricanes).
- Health scares (e.g., Covid-19);
- Political events and economic issues(e.g., the war in Ukraine, inflation);
- Holidays and retail sales seasons
Real-World Examples of Phishing Attacks
Now that we’ve covered the theory, let’s look at some real-world examples of phishing attacks.
Google and Facebook (2013-2015)
One of the most infamous phishing attacks targeted Big Tech giants Google and Facebook.
A Lithuanian hacker, Evaldas Rimasauskas, impersonated a hardware vendor and tricked the companies into wiring over $100 million to fraudulent accounts.
By creating fake email addresses and invoices that mimicked those of a legitimate vendor, he successfully deceived the companies’ finance departments. This case highlights the effectiveness of business email compromise (BEC) scams and the importance of rigorous verification processes for financial transactions.
Check out the US Department of Justice’s press release to read more of the matter.
Looking for European alternatives to Big Tech products? Check out our guide here.
Target Data Breach (2013)
A phishing attack on a third-party vendor led to one of the largest retail breaches in history.
Attackers stole login credentials from the vendor, allowing them to access Target’s network and install malware on point-of-sale systems.
A phishing email was initially sent to the vendor’s employees, and one of them fell for the trap. In analysis conducted after the attack, it became apparent that two-factor authentication (2FA) could have mitigated or even prevented the breach.
The breach compromised credit and debit card details of over 40 million customers, leading to substantial financial and reputational damage for the company. This incident demonstrated the risks posed by supply chain vulnerabilities.
“Phishing is the number one entry point for ransomware and data breaches. A single compromised email can cost a company millions, not just in direct financial loss but in regulatory fines, legal fees, and reputational damage.”
— Brian Krebs, Investigative Journalist & Cybercrime Expert who broke the story
Target ended up paying USD 18.5 million to settle the case.
You can read the full analysis of the incident in the US Department of Commerce’s analysis here.
The Impact of Phishing Attacks
Phishing attacks have far-reaching consequences that extend beyond the immediate victim. They can lead to significant financial losses, reputational damage, regulatory penalties, and even national security risks.
Financial loss
According to the FBI’s Internet Crime Complaint Center (IC3), phishing attacks resulted in over $2.7 billion in reported losses in 2022 alone. Organizations often face direct financial losses due to fraudulent wire transfers, unauthorized transactions, and the costs associated with incident response and recovery.
Data breaches and identity theft
Phishing is a common vector for data breaches, such as the one affecting Target which we discussed. When cybercriminals gain access to login credentials, they can exfiltrate sensitive customer and employee data. Another example was the breach at Equifax in 2017, which exposed the personal information of 147 million individuals. You can read more about the case in the Federal Trade Commission’s report here.
Reputational damage
Organizations that fall victim to phishing attacks suffer reputational harm, leading to loss of customer trust and market value.
For example, Yahoo’s disclosure of multiple data breaches between 2013 and 2016 affected its acquisition deal with Verizon, reducing the company’s valuation by $350 million according to Reuters.
Staying Safe from Phishing Attacks
- Be wary of emails asking for confidential information – especially information of a financial nature. Legitimate organizations will never request such information via email, phone calls, or other means. Instead, always pay attention to the sender’s email address. It may imitate a legitimate business with only a few characters altered or omitted.
- Never open a suspicious attachment, as it is a standard delivery mechanism for malware. Phishermen like to use scare tactics and may threaten to disable an account or delay services until you update certain information. Be sure to contact the merchant directly to confirm the authenticity of their request.
- Watch out for generic-looking requests for information. Fraudulent emails are often not personalized, while authentic emails from your bank often reference an account you have with them. Many phishing emails begin with “Dear Sir/Madam” or other generic greetings/signatures, and some come from a bank with which you don’t even have an account.
- Don’t get pressured into providing sensitive information, and never submit them via embedded forms within email messages – a very common phishing practice and widely pushed onto your junk/spam folders on a daily basis.
- Never use links in an email to connect to a website, as they could be spoofed hyperlinks. The links not matching the text that appears when hovering over them should raise a red flag. It also includes the use of UR-shortening services. Instead, open a new browser window and type the URL directly into the address bar (or check where that short link leads to, e.g. see links below). Often a phishing website will look identical to the original, e.g., https://wwwpaypal.com/ is different from https://www.paypal.com/. Similarly, https://www.paypaI.com/ (with a capital letter “i” instead of a lowercase “L”) is different from https://www.paypal.com/ – look at the address bar to make sure that this is the case (and the connection is secure – such as https://).
“The weakest link in cybersecurity isn’t the technology—it’s the human element. Organizations that invest in phishing awareness training significantly reduce their risk of compromise.”
— Theresa Payton, Former White House CIO & Cybersecurity Consultant
More Phishing Protection Tips
- Make sure you maintain an adequate environment to combat phishing. Use anti-viruses and trusted browsers. Keep all your software up-to-date. Use encrypted services such as Mailfence to communicate and further safeguard your privacy.
- Use Password managers that auto-fill passwords to keep track of which sites those passwords belong to. If the password manager refuses to auto-fill a password, you should hesitate and double-check the site you’re on. Read this blog post to avoid bad password habits.
- Always be suspicious – Phishing emails try to freak you out with warnings, then offer you an easy fix if you just “click here!” (or “You’ve won a prize! Click here to claim it!”) When in doubt, don’t click. Instead, open your browser, go to the company’s website, and then sign in as usual to see if there are any signs of strange activity. If you’re concerned, change your password.
- Always use 2FA (two-factor authentication) when a service provides it.
- You can check-test a particular link before opening it on where it leads to: Where Goes, Redirect Detective, Internet Officer Redirect Check, Redirect Check, URL2PNG, Browser Shots, Shrink The Web, Browserling.
- Last but not least, learn about new trends in phishing. You can start by reading our Email security and privacy awareness course. It is simple and accessible for all, yet informative.
What to Do If You Fall Victim to Phishing
If you have fallen for a phishing attack, check out our blog post on hacked emails.
You can also report the phishing attempts at:
- Google – report phishing or badware
- US-Cert.gov – report phishing
- Consumer.ftc.gov – report phishing
In the future, try to always protect your computer by applying these 10 tips.
2025 Phishing Trends: The Rise of AI
Artificial intelligence (AI) has disrupted many industries since the arrival of ChatGPT in 2022. Unfortunately, as history has shown us many times, criminals are among the first to adopt new technologies.
AI is no different. In 2025, we expect a wave of hyper-sophisticated phishing attacks thanks to the rise of generative AI. Here are a few trends you should keep an eye out for.
#1: AI-Powered Hyper-Personalization in Phishing Attacks
Unlike traditional mass phishing emails (“Hello, I have a donation for you…”), these attacks use real-time behavioral data, social media activity, and leaked data breaches to create tailored messages that feel incredibly authentic to the recipient.
For example, attackers can use AI to scan a target’s LinkedIn profile, recent social media posts, or even hacked email patterns to create context-aware phishing emails.
These messages may reference recent meetings, job applications, or even personal interests, making them highly convincing.
AI chatbots can then engage in automated phishing conversations, luring victims into revealing sensitive information over time rather than in a single email. This tactic makes phishing attempts seem more legitimate and increases their success rate.
One example of this in 2025 will be the rise of fake recruitment scams, where AI-powered bots imitated job recruiters, referencing real job openings at well-known companies to trick job seekers into submitting personal information and credentials.
#2: Voice Phishing (Vishing) with AI Voice Cloning
The resurgence of voice phishing, or “vishing,” has been amplified by advancements in AI voice cloning technology.
Attackers can now create realistic voice replicas of executives, colleagues, or other trusted individuals.
By leveraging these cloned voices, cybercriminals leave convincing voicemail messages or conduct live calls, urging employees to perform actions such as transferring funds or disclosing confidential information. This method exploits the inherent trust in familiar voices, making it a potent tool for deception.

It’s also worth noting that attackers only need 2 minutes of your voice to convincingly replicate it. So even a few videos of you on Instagram are enough to replicate your voice (or one of a close relative)!
#3: Phishing-as-a-Service (PhaaS)
The cybercrime ecosystem has seen the rise of Phishing-as-a-Service platforms.
These services provide ready-made phishing kits, complete with templates, hosting, and even customer support, lowering the barrier to entry for aspiring cyber criminals.
Some PhaaS offerings incorporate AI to automate and optimize phishing campaigns, increasing their reach and effectiveness. This commodification of phishing tools has led to a surge in the number and diversity of phishing attacks, as even individuals with minimal technical expertise can launch sophisticated campaigns.
Conclusion
Cybercriminals, often backed by governments or very powerful mafias, are moving very fast, and their creativity is limitless. They are constantly finding new tactics and new vulnerabilities to exploit.
On the other side, we (users) tend to multiply the number of connected devices… which provide new doors for possible attacks. Therefore, it is important to keep up with cybersecurity.
Most of all, you should rely on common sense. You can’t win a contest you didn’t enter. Your bank won’t contact you using an email address you never registered. Know the warning signs, think before you click, and never ever give out your password or financial info unless you’re properly signed in to your account.
By the way, having an encrypted email suite like Mailfence is crucial to secure your communication and help you to avoid all sorts of scams.
In fact, Mailfence has been designed to protect you from cyber threats and privacy breaches, including phishing. In addition to its end-to-end encrypted email, it includes digital signatures and 2FA. Oh, and it’s not only an email solution but also a collaborative office suite.
Sign up for a free Mailfence account today and start protecting your communications.




