The coronavirus pandemic has turned the world upside down. We all had to change our routines and adapt to different ways of working in a matter of weeks. These changes have accelerated the rollout of some new technologies, and they have also spurred innovation and the development of new tools. Unfortunately, they have also created a breeding ground for cyber crime. In the last two years, cyber criminality has exploded. Now, it is affecting everyone, and many of you are probably worrying about it. But in order to understand your level of exposure and the measures you need to take to protect yourself, you first need to know what these cyber threats actually are and why the pandemic has fostered them. Let’s have a look!
What were the most common cyber threats in 2021?
“Cyber security threats” is a worrisome word that refers to several categories of crimes perpetrated on the Internet by malevolent individuals or risks incurred by IT systems. Often, greed motivates cyber crime. Hackers look to extort or steal money, or they steal sensitive information in order to resell it.
But in other cases, their goal may be to harm the victim by undermining their good name or publicly humiliating them. Political considerations or espionage often motivate cyber threats as well.
The perpetrators can be isolated individuals, but more often than not, they act in more or less organized gangs. Some state-sponsored actors, mainly regarded as Advanced Persistent Threats (APTs) also exist.
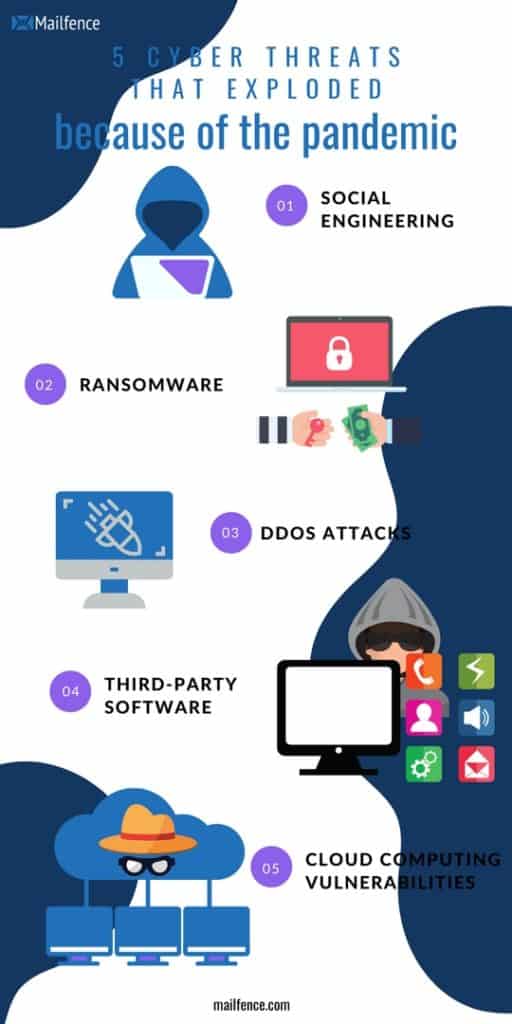
But what were the most frequent cyber security threats since the beginning of the pandemic? We have classified them in 5 categories:
1. Social engineering
Social engineering techniques use human psychology and manipulation for malicious purposes. For example, hackers can leverage an employee’s obligation to obey his superiors’ orders by sending him a message allegedly written by his manager. They can then extort sensitive information such as login credentials, or obtain specific actions, such as transferring money to a specific account.
There are several social engineering techniques. The most common is phishing. It most often consists in sending a fraudulent email inviting the recipient to click on a link to go to a fake site. Hackers would specifically design a deceptive site to collect the recipient’s login credentials. In other cases, the email contains an attachment with malicious software (virus, or ransomware) hidden inside.
In March 2020, the number of phishing attacks increased by 667%.
Phishing is popular with hackers because it is very effective. It also comes in several variants, including:
- spear phishing : in general, phishing seeks to reach several people at once. But in this technique, the hacker targets a particular victim after collecting much information on the target. The goal is to write the most credible message possible to gain victim’s trust;
- whaling : this type of phishing attack is launched against high-level executives in order to increase its impact if successful.
According to studies, spear phishing initiates 91% of cyber attacks.
2. Ransomware
Ransomware is a malicious software that aims to make all or part of an IT system inaccessible, often by encrypting (scrambling) its data. The hacker can then force the owner of the infected system to pay a ransom to get his data back.
In 2020 alone, ransomware attacks grew by 435%.
Similarly, the overall value of cryptocurrency payments related to ransomware has increased 4-fold. Attackers are getting greedier, and the average value of ransoms demanded has risen from $31,200 in 2020 to $570,000 at the end of the first half of 2021.
The reason for this spike is, mainly, the increasing number of vulnerabilities that have been uncovered. The adoption of ever more complex digital technologies facilitates these vulnerabilities. Plus, the pandemic revealed many of them.
But we must also point to the relative immunity of malicious individuals who engage in cyber crime. Cryptocurrency payments that ensure the anonymity of the perpetrators make it difficult to identify the perpetrators, which is why hackers favour it.
Even worst is the fact that there are now “ransomware as a service”, i.e. platforms where apprentice hackers use sophisticated ransomware made available by gangs. They are paid a commission on the attacks organized thanks to their service. This expands the profitability of their activities.
What is worse, companies should not rule out the possibility of new attacks being launched in the aftermath. For example, DarkSide, a group of malicious individuals, was not only encrypting its victims’ files. They were also using their access to the data to leak them and launch distributed denial of service (DDoS) attacks.
And this trend will doubtless continue to grow, as Cybersecurity Ventures calculated that the costs of ransomware attacks will more than probably reach $265 billion by 2031.
By then, there will be an attack every two seconds.
3. Distributed Denial of Service (DDoS) attacks
A DDoS attack aims to launch a large number of requests to a website at the same time. The Web site targeted by this attack is then overwhelmed and cannot cope anymore. It crashes and Internet users can no longer access it.
Botnets, i. e., networks of “bots”, most often launch these attacks. These are code or software designed to launch a request to a website server repeatedly.
Computers, servers, smartphones or other connected devices can be hacked and hijacked to become bots used in a DDoS attack without the owner’s knowledge.
However, unlike the majority of threats listed in this article, distributed denial of service attacks are not about exploiting a vulnerability. They simply exploit the normal way things work.
The increasing use of cloud hosting also facilitates these attacks, as they are launched against networks connected to the Internet.
Nowadays, hackers also use artificial intelligence to search for vulnerabilities in targeted websites.
Unfortunately, these types of attacks are relatively cheap to carry out, making them easy to perform and cost-effective. Often, the hacker combines it with a ransom demand and requests money to stop the attack.
But in a number of cases, entities hostile to the owner of the website in question sponsor the attack. This can be a competitor, an ideologically or politically motivated group, and sometimes even a government.
For the attacked sites, the losses sometimes run into millions of dollars. Worse, the disruption of service can cause lasting damage to a site’s reputation.
In 2021, ZDNet calculated that the number of DDoS attacks had increased by at least 154% over the previous two years.
4. Third-party software
These are vulnerabilities that come from third-party software. Very often, companies use multiple applications and tools to conduct their business. But these offer the possibility of vulnerabilities and loopholes that can lead to data leaks and breaches.
According to statistics provided by Verizon, in 2020, 80% of organizations experienced a security breach from a vulnerability in one of their applications that originated externally. In 43% of cases, these breaches were related to web-based applications.
These breaches have cost an average of $4.29 million to the companies that experienced them.
5. Cloud computing vulnerabilities
The pandemic has boosted the implementation of the cloud in companies, because it facilitates teleworking. An employee can connect from home to their company’s applications and software when these are hosted in the cloud. This is more difficult to do when the applications are hosted on a local server.
Unfortunately, this rapid adoption has had a downside: it has not always been matched with adequate security safeguards. Indeed, the cloud architecture, which is very different from traditional network architecture, has presented new cyber security challenges for IT managers. They did not always have the ability to address them immediately.
As a result, breaches in corporate IT systems have sometimes occurred, and hackers have capitalized on them.
In the second half of 2020 alone, hackers launched 7.5 million attacks on clouds.
In some cases, they exploited loopholes such as a lack of passwords, or an un-updated system. But there were also brute force attacks, ransomware attacks and data theft.
Why are cyber threats expanding so much since the pandemic ?
2020 has been an exceptional year for businesses around the world. Faced with a global pandemic for the first time, they had only a few weeks to adapt to the various challenges they faced.
In particular, those who were not yet teleworking had to implement it very quickly. They had to acquire new computer equipment, and establish new procedures to allow their employees to work from home.
Many have adopted virtual private networks (VPNs) to enable their employees to access the corporate network. Some employees were working with their own computer equipment. This allowed them to bypass the security measures in place within the company’s IT perimeter.
And since employees do not always update their devices thoroughly, their devices could present security flaws.
These initiatives created new opportunities for malicious individuals. Cyber criminals were able to exploit vulnerabilities in these systems and weak passwords. But they have also taken advantage of other factors:
1. The large number of official announcements sent to the public
The numerous messages from the government and other trusted organizations informing the public about what to do during the pandemic inspired some malicious individuals. They have used this opportunity to send phishing emails and other social engineering techniques that mimic these types of official announcements.
For example, they sent emails containing links to pages purportedly to provide the latest data about “coronavirus cases near your place”. While these pages may appear legitimate, hackers actually designed them to steal email credentials.
In other cases, a comment such as “Check out the steps you can take to avoid Coronavirus infection” provided a link that pointed to malware.
The hackers also capitalized on the fear of the disease. They sent emails containing links to what was presented as a miracle cure.
Finally, some fraudulent emails imitated donation campaigns, with the aim of extorting money from the most generous people.
2. Disruption of supply chains
The pandemic has also disrupted supply chains in some industries. Here again, these disruptions have resulted in specific messages to warn customers, creating new cyber threats. Malicious individuals have taken advantage of this to send out fake emails, fake invoices and even fake job applications in an attempt to dupe employees in companies.
Very often, these fraudulent emails contained attachments infected with malware. The aim is to steal sensitive data or to block the company’s computer system to allow the hackers to demand a ransom in exchange for unlocking it.
3. The Internet of Things (IoT)
The trend to connect more and more everyday devices to the Internet also opens new opportunities for hackers.
Our favorite connected gadget, the smartphone, has become one of their prime targets. Hackers focus not only on individuals, but also on companies that apply the “Bring your own device” (BYOD) policy. These policies have thus expanded the scope of the classical cyber threats.
Remote work and increasing mobility also favor the use of mobile devices. However, companies do not always provide the same level of security on their mobile devices as they do on their traditional computers.
And when employees use their own devices, the security loopholes are often even more critical.
As a result, Symantec has determined that in 2021, there was a monthly average of 5,200 cyber attacks against IoT devices.
4. The novelty of the technologies used
The growth of teleworking has led many companies to use innovative video conferencing software such as Zoom, or collaborative software such as Slack.
But many employees are unaware that hackers can also launch phishing attempts on these platforms, and that some malicious intruders can interfere in the video conferences they attend.
As a result, they are less suspicious than with email, and may tend to share sensitive information or open infected files these individuals transmitted.
5. The release delay of security patches
This point is not directly related to the pandemic, but remote working sure didn’t help.
Every year, nearly 23,000 vulnerabilities are discovered in software or hardware. This number is huge, and most of the time, it’s simply not possible for companies or individuals to be informed of all the vulnerabilities that are revealed and to fix them.
As a result, most of them escape their vigilance. These represent new cyber threats as well as new opportunities for malicious individuals or organizations.
Worse, very often, professionals publish updates to solve the vulnerabilities few weeks later, and companies or individuals affected by these vulnerabilities do not always install these patches as soon as they are released (companies take an average of 102 days to apply them).
However, most hackers need only one week to come up with a scheme to exploit these vulnerabilities and launch attacks against companies exposed to them. As a result, the number of “zero day” attacks (attacks that exploit security flaws before the availability of the corresponding patch) increased very rapidly last year, and this trend will probably grow further this year.
Many traditional antivirus programs rely on signature-based detection, which involves identifying specific details in the malware code. This signature is then added to the antivirus database. In the event of a new attack by a similar virus, the security tool compares the code of the suspicious program with those signatures it has stored in its virus database. If they match, it’s classified as malware.
However, nowadays, hackers often at least partially encrypt malware, which means that traditional antivirus software fails to identify it.
6. Vulnerabilities in IT security architectures
Companies often acquired cyber security tools over time, and they are often quite disparate. This is even more true since the beginning of the pandemic and the increase in people working from home.
For example, software designed to protect against cyber threats that are several years old coexist with newer tools. As a result, it is sometimes difficult to make them work together effectively, creating a vulnerability.
As a result, this creates gray areas, where security is no longer as strong as it should. The most astute hackers can exploit these weaknesses.
Protect yourself or your business from cyber threats
Stay informed and learn how to secure your environment and communications. Read all available information about emerging threats and what you can do to protect yourself from them. Follow our unique course and protect yourself against cyber criminals. More generally, have a look at our 10 best practices to ensure a secure Internet experience.
Feel free to spread the word with your colleagues, family, friends, … As you could actually suffer from it as well.
Conclusion
The COVID-19 pandemic is causing an explosion of cyber threats around the world. The most common of these include:
- social engineering
- ransomware
- distributed denial of service attacks
- vulnerabilities in external software
- cloud vulnerabilities
Hackers have largely exploited the opportunities offered by the sanitary crisis itself:
- the numerous official communications
- the disruption of supply chains
- the massive and sudden surge of remote working
For many companies, teleworking was new and they had to adapt too quickly. As a result, they had to rely on technologies they were not familiar with, creating new vulnerabilities in their IT systems.
Finally, the abundance of these new technologies is also linked to a host of security gaps. Hackers often have time to exploit these vulnerabilities before someone resolved them.
It is therefore vital for you to take security steps to protect yourself against these cyber threats. Also, don’t hesitate to adopt secure tools such as VPN and secure email. These technologies may seem daunting at first, but they are actually very easy to use.
Do not underestimate what you can do to protect your personal data. By using Mailfence, you are taking a step forward and supporting a private and secure service.
Stay up to date with our latest articles by following us on Twitter and Reddit. For more information on Mailfence’s secure email suite, please do not hesitate to contact us at support@mailfence.com.