Imagine receiving an urgent email from your CEO, instructing you to authorize a high-value wire transfer. Everything looks legitimate, but there’s just one problem… it’s a scam. More specifically, you are the target of a whaling attack!
And while whaling attacks are not new, their sophistication has grown exponentially with the rise of AI.
In this guide, we’ll break down:
- what a whaling attack is;
- how whaling attacks work;
- real-life cases of businesses losing millions;
- our best advice to detect and prevent whaling attacks.
What Does a Whaling Attack Look Like?
So, what is a whaling attack?
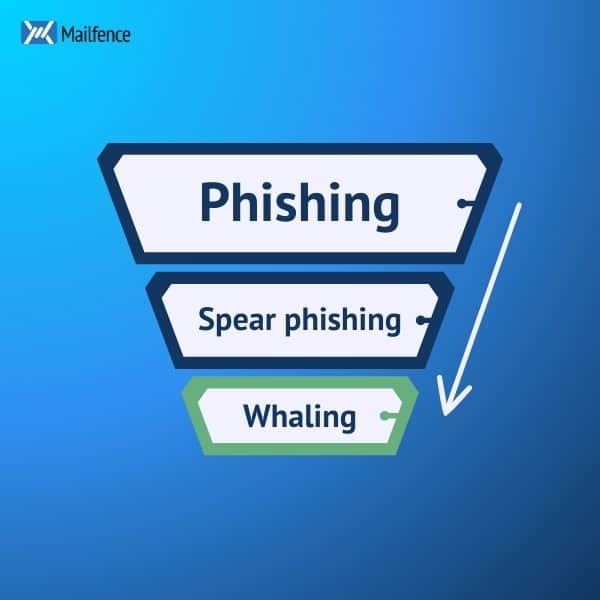
A whaling attack is a form of phishing attack usually using fraudulent emails which emanate and/or target executives or managers.
More specifically, it is a form of spear phishing, i.e. a phishing attack that targets a specific individual. Only in this case, the target is a “whale”, a term derived from the gambling industry where big betters are referred to as “whales”:
Here’s a scenario:
- Jane Doe, CFO of a fast-growing tech company, is checking her inbox on Monday morning. She notices an email from her CEO marked as “Urgent”, with the subject line “Confidential Wire Transfer Required”.
- In the email, her (supposed) CEO informs her that they are “finalizing a critical acquisition, and need her to wire $500,000 to the legal team immediately”. She is also informed that “the deal is highly confidential—do not discuss it with anyone. Transfer the funds to the account below and send me confirmation ASAP”.
- Jane hesitates, but everything looks legitimate: the email signature, company logo, tone of voice. Even the email sender address is correct! She initiates the transfer…
- She later calls her CEO to confirm the transaction is done. This is when she learns she has just made a terrible mistake… By the time IT can investigate, the funds have already been moved to an untraceable offshore acount. The company has just fallen victim to a whaling attack.
Whaling attacks rely on many of the same social engineering tactics as phishing attacks:
- trust: the attackers will imitate the company’s communication codes, including logos, fonts, writing style etc;
- compliance with authority: as humans, we are naturally inclined to obey authority figures;
- sense of urgency/danger: people often lose all rational thinking when faced with a sudden sense of panic or urgency. Attackers use this to their advantage to achieve their goals.
By impersonating a CEO or a top-level executive, cybercriminals use all three of these tactics to trick their victims. They usually try to get large wire transfers, and sensitive information, or insert malware with fraudulent links.
Real-World Cases of Whaling Attacks
Now that we’ve looked at a theoretical example, let’s examine some real-life cases of whaling attacks, and what we can learn from them.
The FACC CEO fraud
In 2016, FACC, an Austrian aerospace manufacturer, fell victim to a whaling attack that cost the company $40 million.
In this large-scale attack, cybercriminals impersonated the CEO, Walter Stephan, and sent an email to the company’s finance department requesting an urgent transfer for a “secret business project.”
Believing the request was legitimate, the finance team authorized the transaction. By the time the fraud was uncovered, the funds had been transferred to foreign bank accounts and vanished. Luckily, around US$10 million were recovered. But another US$40 million disappeared forever.
This whaling attacks was a classic application of several social engineering tactics:
- email spoofing: attackers used a fake email domain closely resembling the company’s. They then researched the CEO’s writing style and tone of voice to make the email seem authentic;
- urgency: the email stressed the urgent nature of the transaction and that the employee needed to act quickly;
- authority: the email impersonated the CEO directly, adding a leyer of credibility to the attack.
To learn more about this case, check out this press article here.
Google & Facebook lose $100 million
In 2019, a hacker named Evaldas Rimasauskas was sentenced to 5 years in prison for one of the biggest whaling attacks in history.
Between 2013 and 2015, he executed one of the most sophisticated whaling scams in history—stealing a combined $100 million from Google and Facebook.
In the scam, Rimasauskas created convincing emails using fake email accounts, pretending to be a supplier of Facebook and Google. These phishing emails included fake invoices for multi-million dollar amounts, which employees were in the habit of processing.
Ultimately, the employees were tricked into transferring more tham US$100 million before noticing something was wrong. This whaling attack highlights two specific techniques used by scammers:
- fake vendor scheme: attackers research a company’s supply chain so that they can impersonate a real business, adding a layer of authenticity to their attack;
- sophisticated forgery: the fake documents were highly convincing and included fake invoices, fake contracts, official-looking corporate seals and signatures and more.
You can learn more about this case in the US Department of Justice press release here.
The deepfake CEO scam
In 2019, the world witnessed one of the first AI-assisted whaling attacks. A UK-based energy company lost €220,000 ($243,000) after cybercriminals used AI-generated deepfake audio to impersonate the company’s CEO.
An employee received a call that sounded exactly like their CEO, instructing them to wire money to a “supplier.”
The employee followed the instructions—only to later realize the voice was artificially generated using deepfake technology. By that time, the funds has already disappeared into a Hungarian account, never to be seen again.
The call seemed to come from a known company number, adding legitimacy to this whaling attack. Attackers even followed up with fake emails confirming the transactions. You can learn more about this case here.
This case marked a turn for whaling attacks: the integration of AI. More on that in the next section…
The Rise of AI in Whaling Attacks
The emergence of AI has revolutionized social engineering attacks, and this includes whaling attacks.
In particular, thanks to AI, whaling attacks have become more convincing, scalable, and harder to detect than ever before.
Let’s explore more in detail the different ways in which AI is helping scammers craft more sophisticated whaling attacks.
AI-powered voice cloning
One of the most alarming AI applications in whaling is deepfake voice cloning, where attackers use AI to replicate the voice of a CEO or senior executive.
Thanks to AI, attackers can generate realistic voice clones with samples of a target’s voice.
These samples can be taken from public interviews, leaked phone calls, or even just social media. Most importantly, thanks to AI-powered software such as VALL-E or ElevenLabs, scammers only need a few minutes of audio to replicate a voice realistically!
The voice clones can then be used in real-time to impersonate a CEO or CFO and instruct an employee to make a wire transfer.
Deepfake videos
The next step after voice cloning? Face cloning!
In what is commonly known now as “deepfakes,” scammers can replicate the physical appearance through highly realistic, AI-generated footage of executives speaking on video calls.
When done properly, these deepfakes have becone almost indistinguishable from authentic videos. And the technology is only getting started… Attackers can now insert a fake CEO into a Zoom or Microsoft Teams call, where the “CEO” personally instructs employees to make payments or share sensitive data. Employees, seeing a trusted face, comply without suspicion.
In 2024, this type of whaling attack gained prominence with the deepfake of a Hong Kong-based CFO, leading to the loss of US$25 million.
AI-powered website spoofing
Traditional phishing sites often had telltale signs—typos, bad formatting, or suspicious URLs.
AI has changed that. Machine learning algorithms can now generate near-perfect clones of corporate websites to trick employees into entering credentials or approving transactions.
Attackers now use AI web crawlers to scrape real websites and recreate them pixel-for-pixel. Domain spoofing techniques create lookalike URLs (e.g., maifence.com instead of mailfence.com). AI chatbots can even simulate real customer service agents to build credibility.
AI-powered email scams
In the past, whaling attack emails often contained grammatical errors, making them easier to spot.
Today, AI-powered text generation tools (like ChatGPT, Jasper AI, and WormGPT) allow attackers to craft flawless, highly personalized emails that mimic an executive’s writing style and tone.
All the attackers need is access to past emails to train their AI models. The AI can then write in the CEO’s style, making the email highly convincing.
How to Identify Whaling Attacks?
Thanks (or rather because) of AI, whaling attacks have become harder to spot than ever before.
However, here are the signs you should look for if you are suspicious:
- Personalisation: The email sent to initiate the whaling attack will most likely include personalised information about the impersonated CEO or senior executive, the victim (a manager or another executive), or the organisation to create a sense of familiarity.
- Urgency: Whaling scams emails conveying urgency can get the victim to act before thinking of security practices. Attackers often try to frighten victims using powerful personas (CEO, top level executives). Those persons are difficult to disobey.
- Language: Business language and tone are often used to convince the victim that the email has been sent from a high-ranked individual. The attackers often use a scenario in which they ask the victim to do a low-effort action (such as a quick money transfer to a supply partner) based on a fake threat. They may also emphasize confidentiality, so that the victim avoids speaking about the email they have received. No one can thus tell them that this email is a whaling attack.
- Legitimate signature: The attackers may use a believable email address, signature, and a link leading to a fraudulent website. We will show you how to recognize these further down the article.
- Files & Links: Cybercriminals may use attachments or links to insert malware or to request sensitive information. Even if nothing happens when the targetted manager clicks a link or submits information on its website, it could trigger a hidden malware download.
How to Prevent Whaling Attacks?
Don’t want to become another statistic in a whaling attack report? Then follow these steps:
- double-check the sender’s email if it’s sent from a colleague, especially if it’s a high-ranking executive in your organization. When the email comes from a third party, search for the authentic email address of this company and compare the two of them;
- hover over any embedded link with your mouse to check the authenticity of the website. Is there a typo in the website domain, or is redirecting you to some other website? Then you should avoid clicking on the link;
- question the validity of any request for money or sensitive information, even if it’s coming from one of your managers. In case of any doubt, contact them directly by phone to get their confirmation;
- know the power of social media. Anything you post online can be used against you, whether for voice cloning or deepfakes. Attackers can also use names, dates, and places you’ve talked about online to make their attacks more credible. As a rule of thumb, set your social media accounts to private.
Final Thoughts on Whaling Attacks
AI is redefining the scale and sophistication of whaling attacks. Soon, we should expect voice cloning and deepfakes to be indistiguishable for reality.
So, what do you do if you cannot spot fake from reality? You double-check before taking action.
Does an email feel suspicious? Or does a phone call sound a it… off? Ask probing questions, something only the real person could answer. And if in doubt, don’t answer the email or hang up the phone. Check with your IT department, and double-check by calling the person in question directly. These are your best lines of defense against whaling attacks.
If you want to take your cybersecurity further, then your first step should be to get a private and secure email provider. Here at Mailfence, we pride ourselves on:
- Advanced security tools: end-to-end encryption, symmetric encryption, digital signatures, and a lot more.
- No tracking or advertising. We do not use any third-party advertising or marketing trackers. We do not track your activity in the application. Mailfence is completely free from ads.
- Strict privacy laws. Mailfence’s servers are based in Belgium, with strong laws protecting privacy. Only a valid Belgian court order can force us to release data.
Interested in reducing your digital footprint and taking your cybersecurity to the next level? Create your free account today!




