“Zombie” is the term used when an attacker takes control of your computer without your knowledge.
A zombie attack aimed either to steal your sensitive information or to make your computer do things that it normally shouldn’t.
For example, a hacker could use your device to send out spam or, even worse, to attack other computers or IT systems. Worry it might happen to you? Follow our advice on how to prevent your computer from becoming a zombie.
What is a zombie computer?
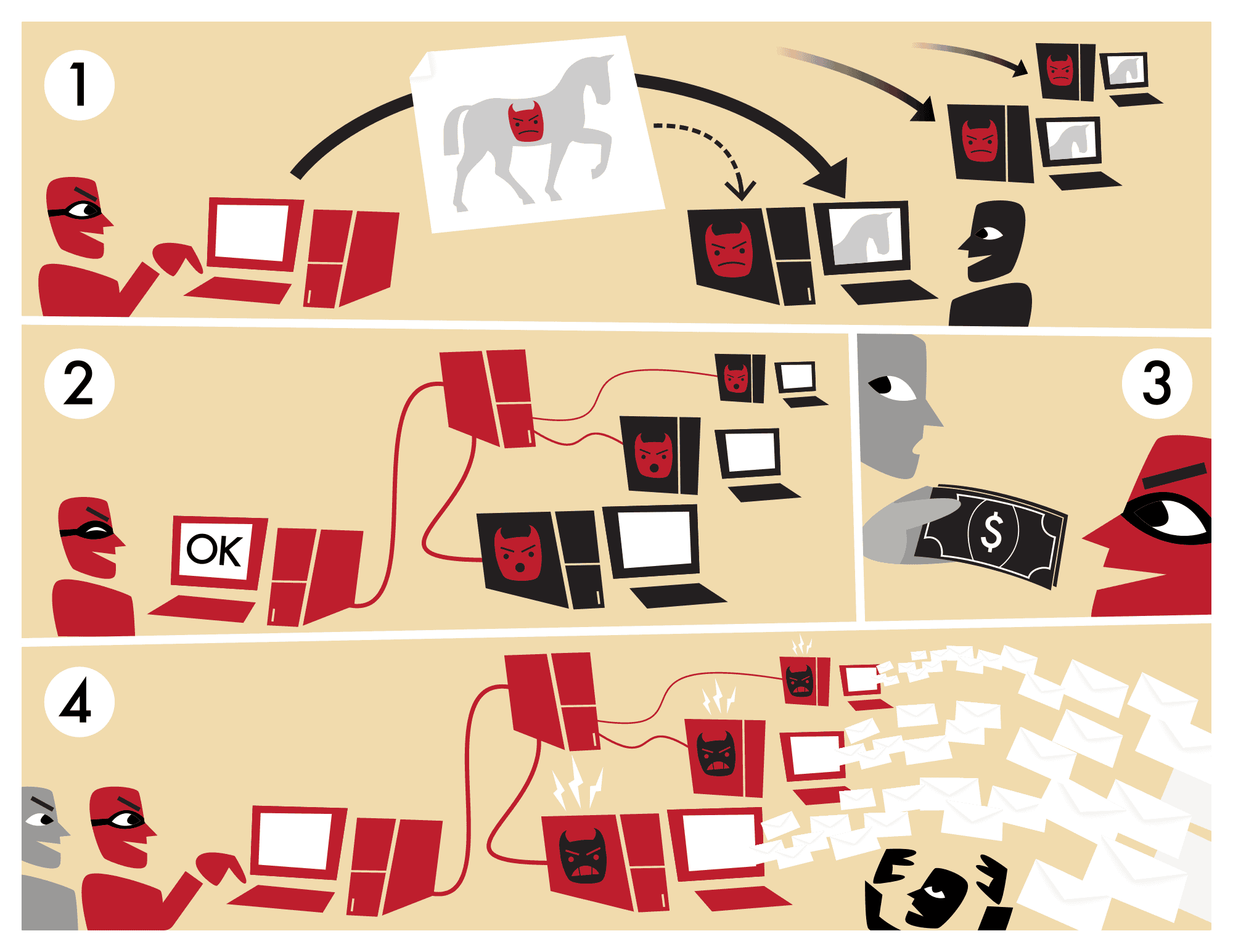
A zombie computer is the result of a cyber-attack similar to a traditional Trojan horse attack (a malicious code wrapped inside a regular behaving code). But instead of aiming only to install a keylogger and steal your personal data, the malicious software will transform your computer into a zombie: thanks to this infection, the hackers can control it remotely. Very often, they will make it “work” with other zombies. Together, all these infected computers will form a botnet (or a zombie army).
Botnets
The term botnet is a portmanteau word made with the terms ‘robot‘ and ‘network’. Botnets are entire networks of computers controlled and instructed to do many kinds of hostile things, such as:
- Attack other computers (DDoS attacks, for example)
- Send spam or phishing emails
- Infect other computers or IT systems with malware (ransomware, spyware, …)
- Commit advertising frauds
- Other similar malicious acts…
The worst part is that it all can happen without you having the slightest idea about it.
How can my computer turn into a zombie?
It only takes malware to turn your computer into a zombie. Malware is a virus or malicious software insidiously installed on your computer. Once your computer is infected, this program runs to perform unwanted actions that are often harmful to you.
Hackers have several options for infecting a computer with malware. They can use a loophole in software or firmware that has not been updated to introduce it into an organization’s computer system or an individual’s computer or embed it in a misleading email. All it takes is a browser plugin update you just keep postponing or a click on a link in an email that seemed to come from a trusted institution.
The bad news is that smart cybercriminals are now using encryption to bypass the conventional virus scanning and spamming checks – making malware (almost) undetectable.
What are the signs my computer is now a zombie?
Here are some clues your device may have been infected by malware and consequently turned into a zombie :
- A part of your hard disk or flash storage seems to have disappeared.
- Your browser often closes for no apparent reason.
- Inexplicable error messages pop out randomly.
- Your computer takes a long time to start up and shut down.
- Your fan is going into overdrive even though your PC is supposed to be idle.
- There are emails in your “Sent” folder you don’t remember writing.
- Some security websites block you from accessing them.
- You can’t download or install antivirus programs or updates.
- Windows Task manager shows suspicious programs you can’t account for.
If you can relate to one or more of these assumptions, there’s a slight possibility that your computer has become a zombie.
What can I do if my computer has become a zombie?
The first thing to do to try to recover your computer from a zombie attack is to run a scan of your antivirus. You’ll have to install an antivirus if you don’t have one. You can then run a scan of your entire system to detect any potential malware.
Very often, if your antivirus finds some virus or malware, it will suggest to you some steps to get rid of it. We advise you to follow them carefully. In many cases, it’ll manage to get rid of the problem, and you’ll recover your computer.
But sometimes, it won’t work and your antivirus will prove unable to remove the malware. In this case, you can only erase your computer’s hard drive(s) and reinstall your operating system and software.
In this scenario, you will lose all the data that has not been backed up. This highlights the importance of regular and comprehensive backups.
How can I prevent my computer from becoming a zombie?
Most cyberattacks (91%) are initiated with a phishing email. It means following secure email practices is essential to help you prevent your device from becoming a zombie. These are the following :
- Don’t click on any suspicious link you’re not sure of / or don’t know where it leads – not even the ones you received from friends, family, or social network buddies. Their accounts might have been compromised. It’s safer to be patient and ask them what it’s all about before rushing to click on the link.
- Do not download any attachments that you never requested.
- Avoid opening spam messages. Especially, don’t click on links that say ‘click here to unsubscribe/etc.’ as they will mostly do the opposite (run a malicious program, …)
- Beware of browser plugins/add-ons and non-trusted apps and avoid giving them unnecessary permissions.
- Install mobile apps with extreme caution– and avoid clicking on fancy ads that normally lead you to watering holes using malvertising.
- Don’t use pirated, cracked, or otherwise illegal copies of programs. Only download them from trusted sources.
- Pay much attention when opening content from encrypted emails, as encryption could hide malicious content.
Going further to prevent zombie attack
Fortunately, you can take action to protect yourself against these threats. You can also apply these easy steps to protect your computer and all your other devices from hackers.
Did you know you can quickly learn to prevent this kind of cyber-attacks and many other ones by reading our course dedicated to Email security and privacy awareness course? You’ll also learn cybersecurity is not always boring nor complicated: we’ve made it straightforward to ensure you take the most of it, whatever your initial knowledge level.
And as the first incursion into this cybersecurity territory, we suggest you sign up now for a free account of our private and secure Mailfence email suite. Get an account and enjoy end-to-encryption to secure your emails. Benefit from a cluster of essential office tools such as a calendar with polls, contacts and groups management, a chat service, and a document storage and management tool, all secured.