Why do hackers target SMEs?
Cybercriminals indeed attack them more often than large companies.
Read this article and find out why pirates target small businesses, and, more importantly, how to protect your SME.
3 Main Reasons Hackers Target Small Businesses More
There are several reasons why pirates target small businesses, but for the most part, they can be summarized into 3 major ones:
- Small businesses are often used as a gateway to large businesses
- They have a limited cybersecurity budget and lack IT personnel
- There is not enough, or any, effort made to train and educate employees about cybersecurity
Let’s explore each reason:
Hackers Target a Small Business to Get at a Larger Corporation
With large organizations spending between $20 and $50 million per year on cybersecurity (with some going even beyond that), the opportunities for cyberattackers to do any kind of damage are few and far between.
However, large businesses don’t do everything themselves, and often contract some of their services to smaller companies. That way, they connect their IT systems to the smaller ones.
This creates another, less secure entry point into their system, which hackers can exploit.
Limited Cybersecurity Budget and Lack of Trained IT Personnel
The second reason why pirates target small businesses ties directly into the first. They are all interconnected in one way or another. While large companies can spend tens of millions of dollars on cybersecurity and not feel the effect on their overall budget, smaller companies don’t have that luxury.
In fact, 51% of small businesses participating in the PurpleSec report said they don’t have any cybersecurity budget!
As a matter of fact, many don’t even have a secure and encrypted email for small businesses.
Instead, small businesses, especially those just starting, tend to multitask and have people wear different hats in the organization. As such, it’s not surprising to see the tasks of cybersecurity and IT allocated to “that guy who knows about computers and stuff”.
Lack of Employee Training and Education Concerning Cyber Threats
Finally, the 3rd main reason for which hackers target small businesses more often than large corporations is the lack of employee training and education when it comes to cyber threats. That’s why we’ve created our free email security and privacy course, to spread the word and make people aware of the cyberthreats.
This issue goes from the top to the bottom of the organization.
As such, it becomes easy for threat actors to find the right target. Even easier to manipulate them into giving them access to the system. It’s typically done through phishing attacks, or any other social engineering attack.
Employees are not the only target of cybercriminals. Very often hackers can have a much better return on investment if they target business owners and managers. This social engineering attack is called a whaling attack.
How can a Small Business Protect itself from Cyberattacks? Finding a Secure Email for a Small Business
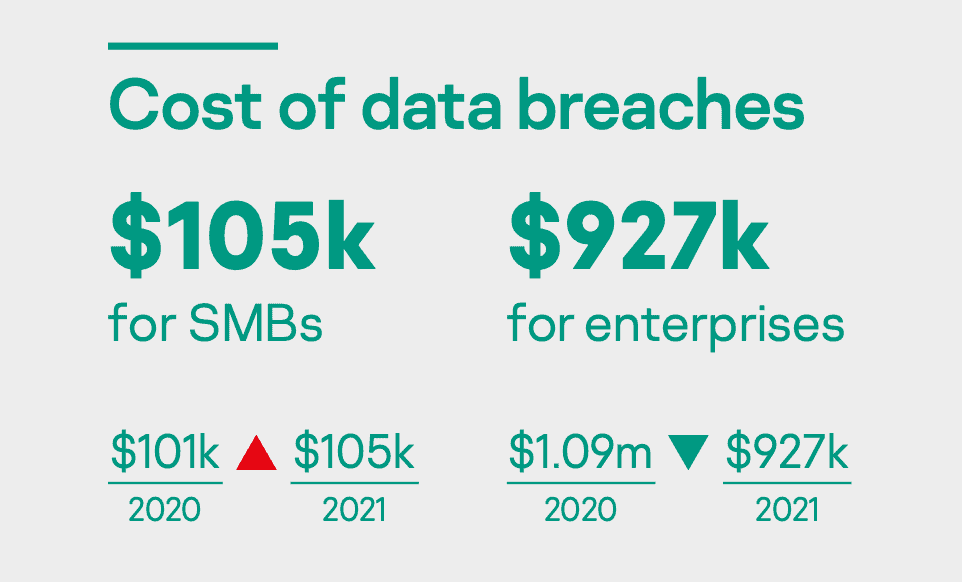
According to Kaspersky’s Managing the Trend of Growing IT Complexity report, the cost of data breaches for small and medium businesses increased from $101K in 2020 to $105K in 2021.
At the same time, SMEs decreased their cybersecurity budget between 2020 and 2021 from $275K to 267K (3 percent).
Simply put, smaller organizations don’t have the resources for a long race against cybercriminals.
However, what small businesses can (and should) focus on is improving their employees’ security and privacy awareness, and using the right tools to deal with the most common cyber threats and hacked accounts.
Keep in mind that email is often the easiest gateway for cybercriminals to access the business and the sensitive data it keeps.
This is why if you want to protect your business from cyber threats, you need to use a secure email service that includes end-to-end encryption and other privacy and security features that will better protect your data.
How can Mailfence Protect Small Businesses?
Mailfence is one of those secure and private email providers and the best alternative to Google Workspace. This is because Mailfence has a complete email suite, just like Gmail, but with privacy and security at heart.
You need a secure and private email right now, and Mailfence is perfect for your business. We offer a collaborative suite including a calendar with polls, contacts and groups management, a chat service, and a document storage platform, all private and secure.
Need help keeping your email account secure or protecting your devices from hackers? Check out these articles and register with us to protect your business from cyberattackers!
Is your cybersecurity budget low at the moment? Investing in a secure and private email provider is the first step to protect your SME from hackers. Joins us and reclaim your privacy!