Wenn es Ihnen geht wie den meisten Menschen, wissen Sie wahrscheinlich nicht viel über Social-Engineering-Angriffe. Oder vielleicht glauben Sie, dass sie nur darauf abzielen, ahnungslose Opfer hereinzulegen und ihnen Geld zu stehlen?
Möglicherweise ist Ihnen nicht bewusst, dass Social-Engineering-Techniken viele Formen annehmen können. Und jeder kann ihnen zum Opfer fallen – sogar Sie.
In diesem Leitfaden erfahren Sie alles, was Sie über Social-Engineering-Angriffe wissen müssen. Unter anderem beantworten wir diese Fragen:
- Was ist ein Social-Engineering-Angriff?
- Welche verschiedenen Formen können Social-Engineering-Angriffe annehmen?
- Wie kann ich Social-Engineering-Angriffe schnell erkennen?
- Und vor allem: Wie kann ich vermeiden, einer Social-Engineering-Attacke zum Opfer zu fallen?
Lassen Sie uns direkt loslegen!
Mailfence - Erhalten Sie Ihre kostenlose, sichere E-Mail.

4.1 basierend auf 177 Benutzerbewertungen
Mailfence - Erhalten Sie Ihre kostenlose, sichere E-Mail.

4.1 basierend auf 177 Benutzerbewertungen
Was ist Social Engineering?
Lassen Sie uns mit den Grundlagen beginnen: Was ist Social Engineering?
Social Engineering umfasst viele Techniken, und alle haben eins gemeinsam: Sie nutzen unsere menschliche Natur aus, um Verhaltensweisen und Fehler hervorzurufen, die zu einer Schwächung der Sicherheit führen.
Diese Techniken ermöglichen es Cyberkriminellen, auf Informationen oder Geld zuzugreifen oder zu kontrollieren, wonach sie suchen. Es handelt sich dabei nicht um einen einzelnen Angriff, sondern eher um eine Gruppe verschiedener Betrugsmaschen, die mehrere Gemeinsamkeiten aufweisen:
- Die Betrüger*innen versuchen, an sensible Informationen oder Geld zu gelangen.
- Sie nutzen das Vertrauen und das menschliche Verhalten aus, um ihre Opfer zu manipulieren und ihre Ziele zu erreichen.
- Sie nutzen die Unwissenheit ihrer Opfer und deren Unfähigkeit aus, Sicherheitsmaßnahmen zu ergreifen, um sich zu schützen.
- Oftmals verwenden sie persönliche Informationen (Identitätsdiebstahl), um authentischer zu erscheinen.
Erinnern Sie sich an das „geschenkte“ Pferd der alten Griechen an die Stadt Troja? Ein hervorragendes Beispiel aus der Praxis.
Der Kern eines jeden Social-Engineering-Angriffs ist Manipulation.
Vergessen Sie Brute-Force-Taktiken. Beim Social Engineering bringen Angreifer*innen mithilfe manipulativer Taktiken ihre Opfer dazu, sich selbst oder die Sicherheitsmaßnahmen, auf die sie sich verlassen, zu kompromittieren. Betrüger*innen nehmen Kontakt zu ihren Opfern auf, um Vertrauen zu erwecken und ihre Handlungen zu beeinflussen.
Während die Angreifenden die Beweggründe ihrer Angriffsziele besser kennenlernen, können sie überzeugende Taktiken entwickeln, um sie zu einem potenziell destruktiven Verhalten zu verleiten.
Und es funktioniert: Viele Vorfälle im Bereich der Cybersicherheit sind erfolgreiche und ausgeklügelte Social-Engineering-Methoden, die von externen Angreifer*innen durchgeführt werden. Sie spielen mit menschlicher Schwäche, um ihre Opfer unwissentlich dazu zu bringen, Zugang zu sensiblen Informationen oder Geld zu gewähren.
Wie funktionieren Social-Engineering-Angriffe?
Wie wir bereits erwähnt haben, beruht Social Engineering auf Manipulation. Diese kann verschiedene Formen annehmen (wie wir später noch beleuchten werden).
Doch jeder Social-Engineering-Angriff nutzt eine der folgenden menschlichen Eigenschaften aus.
Vertrauen
Der*Die Hacker*in sendet eine Nachricht, die die Kommunikationscodes eines Unternehmens vortäuscht, zum Beispiel dessen Logo und andere Markenmerkmale (Schriftarten, Schreibstil etc.).
Die Hacker*innen wollen das Opfer durch diese Täuschung dazu verleiten, Dinge zu tun, die es bei der jeweiligen Organisation üblicherweise tun würde (auf einen Link klicken, eine Datei herunterladen etc.), weil es ihr vertraut und die Herkunft der Nachricht einfach nicht hinterfragt.
Einhaltung der Vorschriften von Behörden
Gehorsam gegenüber Autoritäten ist eine weitere menschliche Eigenschaft, die sich Social-Engineering-Taktiken zunutze machen können.
Die Social-Engineering-Pirat*innen geben sich als hochrangige Personen oder Regierungsbehörden aus, um ihr gehorsames Ziel zu einer Handlung zu verleiten.
Gefühl der Dringlichkeit und/oder Angst
Menschen handeln oft, ohne nachzudenken, wenn sie ein plötzliches Gefühl der Panik verspüren.
Sie sind anfällig für Social-Engineering-Betrugsmaschen, die solche Gefühle ausnutzen. Diese Täuschungsmanöver setzen Angst und Dringlichkeit auf verschiedene Weise ein:
- falsche Kreditkartenwarnungen
- Virenwarnungen
- Ausnutzung der FOMO (Angst, etwas zu verpassen)
Das in Panik geratene Opfer wird zum Handeln verleitet, ohne sich die Zeit zu nehmen, die Folgen seines Handelns zu bedenken. Oft vergisst es unter Stress, die Legitimität der Anfrage zu überprüfen.
Gier
Sie würden doch ein Geschenk nicht ablehnen, oder? Betrüger*innen verstehen das.
Deshalb nutzen viele Betrugsmaschen unsere Gier aus, um uns mit Geldprämien, kostenlosen iPhones und anderen Preisen zu locken.
Haben Sie schon einmal von dem Betrug der „unerwarteten Erbschaft“ gehört? Dies ist ein klassischer Phishing-Angriff, bei dem Ihnen eine große Geldsumme von einem*einer entfernten Verwandten oder einem*einer wohlhabenden Wohltäter*in versprochen wird. Das Geld ist angeblich aus irgendeinem unerfindlichen Grund gesperrt … Doch Sie müssen lediglich die Verwaltungsgebühren bezahlen, um das Geld zu erhalten.
Klingt zu schön, um wahr zu sein? Weil es das ist! Dies ist ein perfektes Beispiel für eine Betrugsmasche, die ausnutzt, welche Anziehungskraft Geld, Geschenke oder einfach zu erhaltende Belohnungen auf uns ausüben.
Großzügigkeit
Und schließlich wird auch unsere Großzügigkeit häufig für Social-Engineering-Angriffe ausgenutzt.
Angreifer*innen schlagen Kapital aus Ihrer Großzügigkeit, indem sie in den sozialen Medien recherchieren, was Ihnen wichtig ist, und sich dann als Organisationen ausgeben, die mit Ihrer Sache verbunden sind. Zum Beispiel könnten sie sich als eine von Ihnen unterstützte Wohltätigkeitsorganisation ausgeben, um zu Spenden aufzurufen.
Wie sehen Social-Engineering-Angriffe aus?
Es gibt viele Arten von Social-Engineering-Angriffen, die leichte Abweichungen aufweisen. Nachfolgend haben wir einige der häufigsten für Sie zusammengestellt.
Phishing-Betrugsmaschen sind die häufigsten Arten von Social-Engineering-Angriffen, die heutzutage eingesetzt werden. Bei dieser Variante wird per E-Mail Kontakt mit der Zielperson hergestellt. Es gibt noch weitere spezifische Arten von Phishing-Angriffen, zum Beispiel diese:
- Smishing, Phishing-Angriffe, die per SMS stattfinden
- Vishing über Telefongespräche
- Spear Phishing, bei dem bestimmte Personen mit persönlichen Informationen ins Visier genommen werden, damit es legitimer wirkt
- Whaling-Angriffe, das heißt Phishing-Angriffe, die auf hochrangige Führungskräfte abzielen
Pretexting ist eine weitere Form des Social Engineering, bei der sich die Angreifenden darauf konzentrieren, einen plausiblen Vorwand oder ein erfundenes Szenario zu schaffen, mit dem sie die persönlichen Daten ihrer Opfer stehlen können.
Baiting ist in vielerlei Hinsicht mit Phishing-Angriffen vergleichbar. Was diese Angriffe jedoch von anderen Arten des Social Engineering unterscheidet, ist das Versprechen eines Gegenstands oder einer Ware, mit dem die Hacker*innen ihre Opfer anlocken, genau wie beim Trojanischen Pferd.
In ähnlicher Weise versprechen Quid-pro-quo-Angriffe einen Vorteil im Austausch für Informationen. Dieser Nutzen wird in der Regel in Form einer Dienstleistung erbracht, während Baiting häufig in Form einer Ware angeboten wird.
Scareware will ihren Opfern vorgaukeln, dass ihr Gerät mit einem Virus infiziert ist und sie eine bestimmte Software kaufen oder herunterladen müssen, um das Problem zu beheben.
Watering-Hole-Angriffe finden statt, wenn Angreifer*innen eine Website kompromittieren, die von einer bestimmten Gruppe von Nutzer*innen besucht wird. Wenn diese Nutzer*innen die Website besuchen, werden ihre Geräte mit Malware infiziert.
Bei einer Honey Trap erstellen Angreifer*innen gefälschte Social-Media-Profile, um sich mit den Zielpersonen anzufreunden und durch trügerische Beziehungen an vertrauliche Informationen zu gelangen.
Reverse Social Engineering schließlich schafft eine Situation, in der das Opfer Hilfe sucht, was es Angreifer*innen ermöglicht, sich als Helfer*in auszugeben und sensible Informationen zu erlangen.
Physische Phishing-Angriffe
Phishing-Angriffe können auch in der „echten“, physischen Welt stattfinden.
Die häufigste Form ist das sogenannte „Shoulder Surfing“. Dazu kommt es, wenn Ihnen jemand direkt über die Schulter schaut, um an Informationen wie Passwörter oder PINs zu gelangen (in der Regel, nachdem er Sie zu einer Aktion gelockt hat, für die Anmeldedaten erforderlich sind).
Ein weiterer Social-Engineering-Angriff ist das sogenannte „Tailgating“, bei dem jemand versucht, physisch in einen Bereich einzudringen, in dem er sich nicht aufhalten darf.
Übliche Merkmale von Social-Engineering-Angriffen
Die meisten dieser Social-Engineering-Angriffe haben folgende Merkmale gemein:
- Persönliche Informationen: Angreifende suchen nach Informationen wie Namen, Adressen und Sozialversicherungsnummern.
- Link-Verkürzer oder eingebettete Links: Diese Links leiten die Nutzer*innen auf verdächtige Websites um, wenn sie auf legitim erscheinende URLs klicken.
- Malware: Social Engineering kann auch zur Einrichtung von Malware verwendet werden, sei es zusätzlich zum Diebstahl der Anmeldedaten des Opfers oder mit dem alleinigen Ziel, das Gerät des Opfers zu kompromittieren.
Social-Engineering-Angriffe in der realen Welt
Nachdem wir uns nun mit der Theorie befasst haben, lassen Sie uns jetzt einen Blick auf einige Social-Engineering-Betrugsmaschen aus dem echten Leben werfen.
Der „Fake-CEO“-Betrug
Im Jahr 2016 hat das österreichische Luft- und Raumfahrtunternehmen FACC rund 50 Millionen Euro durch einen Social-Engineering-Betrug verloren, der als „CEO-Betrug“ bekannt ist.
Die Cyberkriminellen gaben sich als CEO des Unternehmens aus und schickten eine E-Mail an die Finanzabteilung mit der Bitte um eine dringende Überweisung.
Die E-Mail erschien legitim und enthielt den typischen Schreibstil des CEOs und sogar eine gefälschte E-Mail-Signatur. Ohne die Anfrage zu überprüfen, überwies ein*e Mitarbeiter*in das Geld auf ein von den Angreifenden kontrolliertes Offshore-Konto.
Dieser Fall verdeutlicht, wie wichtig es ist, Finanztransaktionen über sekundäre Kommunikationskanäle zu überprüfen, bevor sie ausgeführt werden. Er unterstreicht auch den Wert der Verwendung digitaler Signaturen. Mit Mailfence können Sie Ihre E-Mails mit einer Verschlüsselung digital signieren, die unwiderlegbar beweist, dass Sie tatsächlich der*die Verfasser*in dieser E-Mail sind.
Der Twitter-Bitcoin-Betrug
In einem viel beachteten Social-Engineering-Angriff verschafften sich Cyberkriminelle Zugang zu den internen Tools von Twitter, indem sie sich als Mitarbeitende des IT-Supports ausgaben.
Sie manipulierten Angestellte zur Preisgabe ihrer Anmeldedaten und konnten so die Kontrolle über mehrere hochrangige Konten übernehmen, darunter die von Elon Musk, Bill Gates und Barack Obama.
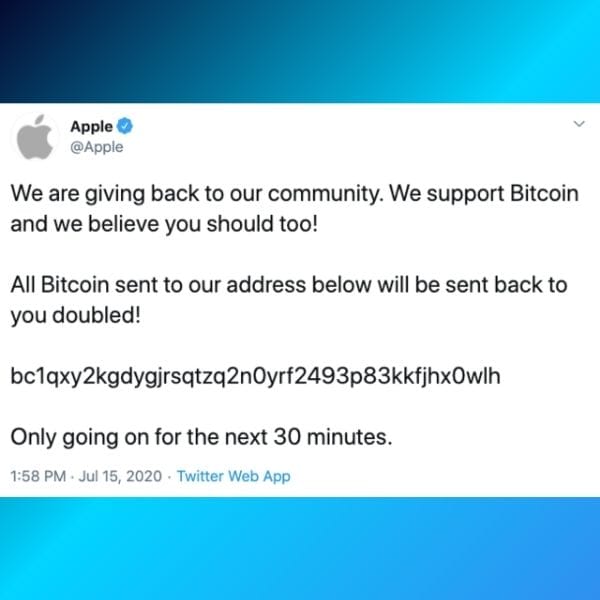
wie dem von Apple verschickt.
Die Angreifenden nutzten diese Konten, um betrügerische Bitcoin-Giveaways zu posten, und täuschten die Follower*innen auf diese Weise, Geld in Form von Kryptowährung zu senden. Dieser Angriff zeigt, wie gefährlich es ist, sich zu sehr auf interne Anmeldedaten zu verlassen, und unterstreicht die Bedeutung von Multi-Faktor-Authentifizierung und einer Schulung der Mitarbeitenden zu Social-Engineering-Taktiken.
Möchten Sie mehr erfahren? Werfen Sie einen Blick in diesen Bericht von Verizon, der auf die Kosten von Datenschutzverletzungen in der Unternehmenswelt eingeht.
Die Rolle von Social Media bei Social-Engineering-Angriffen
Mit dem Aufkommen von Social-Media-Plattformen haben Betrüger*innen einen noch nie dagewesenen Zugang zu Ihren persönlichen Daten. Sie müssen nicht einmal mehr Ihr E-Mail-Konto hacken – auf Instagram, TikTok und X ist alles öffentlich!
Diese Praxis wird als „Social-Media-Reconnaissance“ bezeichnet. Durch die Analyse von öffentlich zugänglichen Beiträgen können Angreifende:
- den Arbeitsplatz, die berufliche Position und die beruflichen Kontakte einer Person identifizieren
- persönliche Daten wie Geburtsdaten, Namen von Haustieren oder Lieblingsorte extrahieren, die zum Erraten von Passwörtern verwendet werden könnten
- von bevorstehenden Reiseplänen erfahren, um einen Angriff zu planen, wenn das Opfer weniger wachsam ist
Mit all diesen Informationen können Angreifende ihre Phishing-Versuche äußerst individuell gestalten. Dies erhöht die Erfolgswahrscheinlichkeit erheblich.
Häufige Angriffe über soziale Medien
Mit einer Fülle von Informationen über Sie können Angreifende leicht einen Spear-Phishing-Angriff durchführen. Über DMs auf Instagram oder X können sie den Anschein erwecken, von einer vertrauenswürdigen Quelle zu stammen, und die Opfer dazu verleiten, auf schädliche Links zu klicken oder Malware herunterzuladen.
Dank LinkedIn wissen Angreifende auch, wo Sie arbeiten, seit wann, wo Sie vorher gearbeitet haben etc.
Mit diesen Informationen können sich die Angreifenden auf LinkedIn als Führungskräfte des Unternehmens ausgeben und versuchen, betrügerische Transaktionen zu initiieren. Sie können sich auch als Personalvermittler*innen ausgeben und gefälschte Stellenangebote versenden, um persönliche Informationen von Arbeitssuchenden zu erhalten.
Um sich zu schützen, sollten Sie sich an diese Schritte halten:
- Legen Sie für private und berufliche Konten strenge Datenschutzeinstellungen fest.
- Vermeiden Sie es, zu viele persönliche und arbeitsbezogene Details preiszugeben. Dazu gehören Orte, die Sie besucht haben oder vorhaben zu besuchen, Namen von Verwandten etc.
- Überprüfen und entfernen Sie regelmäßig Verbindungen mit unbekannten oder verdächtigen Konten.
- Löschen Sie alle Konten in den sozialen Medien, die Sie nicht mehr nutzen. Stellen Sie sicher, dass alle Ihre Informationen gelöscht werden (was Ihr gutes Recht ist).
10 Schritte, wie Sie sich bei einem Social-Engineering-Angriff schützen
Nachdem wir die verschiedenen Formen des Social Engineering und ihre Merkmale erläutert haben, lassen Sie uns einen Blick darauf werfen, wie Sie sie umschiffen können.
Im Folgenden haben wir verschiedene Schritte beschrieben, die Sie unternehmen sollten, um Social-Engineering-Angriffe zu erkennen und sich vor zukünftigen Angriffen zu schützen.
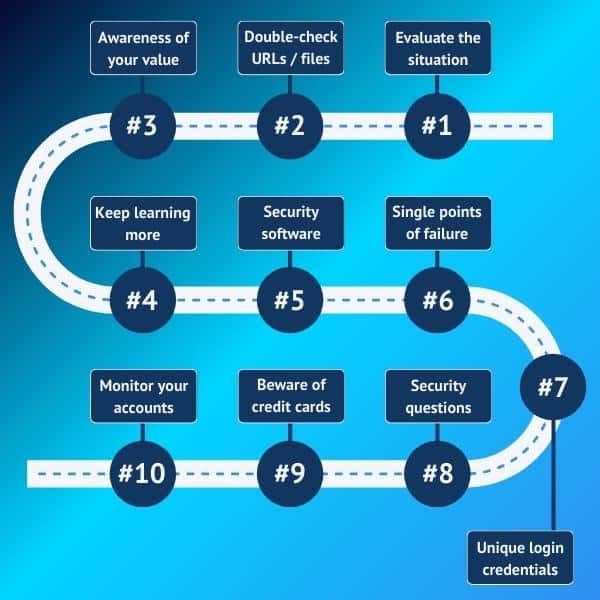
1: Bewerten Sie die Situation in Ruhe
Nehmen Sie sich die Zeit, die ganze Situation zu betrachten und die Nachricht sorgfältig zu prüfen, auch wenn sie recht beunruhigend ist.
- Ist diese Nachricht unerwartet?
- Kommt sie von der Stelle, von der sie kommen sollte?
- Stellen Sie sicher, dass Sie mit vertrauten Kontakten interagieren, indem Sie deren Identität bestätigen. Wenden Sie sich nach Möglichkeit direkt an den*die Absender*in, um sich zu vergewissern, dass er*sie das, was Sie erhalten haben, gesendet hat.
- Achten Sie auch auf Rechtschreibfehler, Sonderbarkeiten im Logo oder andere aufschlussreiche Details. Kommuniziert diese Organisation normalerweise auf diese Weise?
- Auch hier gilt: Nehmen Sie im Zweifelsfall Ihr Telefon in die Hand und rufen Sie die offizielle Nummer – oder die Nummer, die Sie üblicherweise bei diesem Unternehmen anrufen – an (und nicht die angegebene Nummer), um weitere Informationen zu erhalten. Dies ist gerade bei finanziellen Transaktionen ein unerlässlich wichtiger Schritt!
2: Überprüfen Sie die URL oder Datei, bevor Sie draufklicken
Klicken Sie niemals auf einen Anhang oder einen Link in einer E-Mail, ohne ihn sich vorher genau anzuschauen.
In jedem Anhang einer Nachricht kann sich ein Virus oder eine andere Art von Malware, wie zum Beispiel Ransomware, verbergen.
Ein Link in einer Nachricht kann Sie auf eine nachgestellte Website führen, die nur zu dem Zweck eingerichtet wurde, Ihre Daten zu stehlen oder Ihr Gerät mit Malware zu infizieren.
Bevor Sie auf einen Anhang oder einen Link klicken, prüfen Sie ihn sorgfältig:
- Gibt es eine Meldung oder einen Prompt, der anzeigt, dass die angehängte Datei Makros enthält? Wenn ja, dann vergewissern Sie sich, dass Sie keine Makros aktivieren, um die Datei anzuzeigen.
- Haben Sie diese Datei oder diesen Link erwartet?
- Zögern Sie im Zweifelsfall nicht, den*die (vermeintliche*n) Absender*in direkt zu fragen, ob die Nachricht von ihm*ihr stammt (kontaktieren Sie ihn*sie dafür über Ihre üblichen Kontaktmöglichkeiten).
- Wenn Sie Zweifel haben, klicken Sie NICHT! Fragen Sie eine*n Kolleg*in, Freund*in oder eine*n Verwandte*n, wenn Sie unsicher sind. Oder wenden Sie sich an eine*n IT-Expert*in, wenn Sie sich selbst nicht zutrauen, die Situation angemessen einzuschätzen.
3: Achten Sie auf Ihre Kostbarkeiten
Auch wenn Sie kein*e Millionär*in sind, besitzen Sie viele Dinge, die die Gier von Cyberkriminellen wecken könnten:
- Ihre Daten (die im Dark Web verkauft werden können)
- Software-Zugänge, die Sie in dem Unternehmen haben, für das Sie arbeiten
- detaillierte Konten in sozialen Netzwerken mit zahlreichen Bildern und Kommentaren, die zeigen, was Sie mögen, was Sie unterstützen etc. Das bedeutet, dass es einfach sein wird, ein Profil von Ihnen zu erstellen und die passende Strategie für Sie zu bestimmen. Seien Sie daher vorsichtig mit dem, was Sie auf Social Media teilen.
Nehmen Sie sich die Zeit, Ihre Berechtigungen und Ihre Kommunikation im Netz zu überprüfen, und versuchen Sie zu verstehen, welches Potenzial Sie für Betrüger*innen bieten. Wenn Sie sich dessen mehr bewusst sind, können Sie Social-Engineering-Angriffe besser erkennen.
4: Informieren Sie sich über Social-Engineering-Betrugsmaschen
Herzlichen Glückwunsch! Allein durch die Lektüre dieses Leitfadens haben Sie bereits dafür gesorgt, dass Sie weniger anfällig für Social-Engineering-Angriffe sind.
Aufklärung ist der Schlüssel zur Vermeidung von Social-Engineering-Angriffen.
In den meisten Fällen sind wir selbst die Ursache für einen möglichen Angriff, weil uns oftmals das Wissen fehlt und wir uns der Gefahren nicht bewusst sind.
Wenn Sie noch mehr erfahren möchten, werfen Sie einen Blick in diesen Leitfaden über die 7 größten E-Mail-Sicherheitsfehler, die es zu vermeiden gilt. Oder lesen Sie diesen Leitfaden mit Tipps zum Schutz Ihres Computers oder besuchen Sie unseren kostenlosen Kurs zum Thema E-Mail-Sicherheit und Datenschutz.
5: Verwenden Sie Sicherheitssoftware, um Spam- und Phishing-E-Mails zu umschiffen
Um Ihr Gerät und Ihre Daten vor Cyber-Bedrohungen und Einbruchsversuchen zu schützen, müssen Sie ein Antivirenprogramm verwenden und regelmäßige Backups erstellen.
Sie müssen aber auch eine sichere E-Mail-Lösung verwenden, um sicherzustellen, dass Nachrichten, die in Ihrem Posteingang eingehen, keine Malware oder schädlichen Bestandteile enthalten – und um sie zu blockieren, wenn dies doch der Fall ist.
E-Mails gehören zu den häufigsten Einfallstoren für Hacker*innen. Stellen Sie also sicher, dass Sie MFA aktiviert haben, und gewöhnen Sie sich daran, verschlüsselte und digital signierte E-Mails zu senden.
6: Vermeiden Sie Single Points of Failure
Ein „Single Point of Failure“ (zu Deutsch etwa: einzelner Ausfallspunkt) ist ein gängiger Begriff, der bedeutet, dass Sie alles auf eine Karte setzen. Wenn dieser Punkt durchbrochen wird, sind alle Ihre Daten gefährdet. Deswegen sollten Sie es vermeiden, alle Ihre Konten mit Facebook oder Gmail zu verknüpfen.
Je stärker Ihre Konten miteinander verflochten und voneinander abhängig sind, desto mehr Schaden kann Ihnen eine Sicherheitsverletzung zufügen.
7: Eindeutige, einmalige Logins und sichere Passwörter
Verwenden Sie in Verbindung mit Punkt 6 verschiedene Logins für jeden Dienst und starke, eindeutige Passwörter. Erwägen Sie die Verwendung von E-Mail-Aliasnamen und Passwort-Managern zur Verwaltung Ihrer Anmeldedaten.
8: Werden Sie bei Sicherheitsfragen kreativ
Dieser Punkt mag trivial klingen. Aber die zusätzlichen Sicherheitsfragen, die Websites Ihnen stellen, dienen in der Regel dazu, eine 2-Schritte-Verifizierung (2SV) einzurichten.
Seien Sie also kreativ und vermeiden Sie leicht zu erratende Antworten wie Ihr Geburtsdatum oder Ihren Geburtsort. Ein*e Hacker*in wird diese in wenigen Minuten herausfinden. Verwechseln Sie 2SV auch nicht mit der Multi-Faktor-Authentifizierung (MFA) oder 2FA, deren Einrichtung wir Ihnen ohnehin dringend ans Herz legen.
9: Verwenden Sie Debitkarten mit Bedacht
Wenn Sie eine Debitkarte verwenden und ein*e Hacker*in die Nummer in die Finger bekommt, könnte Ihr gesamtes Bankkonto leer geräumt werden. Sie können Ihre Debitkarte zusätzlich schützen, indem Sie keine Kartennummern auf Websites speichern, oder indem Sie Einmal- oder virtuelle Kartennummern verwenden (was mittlerweile von vielen Banken angeboten wird).
10: Behalten Sie Ihre Konten im Auge
Seien Sie auf der Hut vor Identitätsdiebstahl und Kreditkartenbetrug. Überprüfen Sie regelmäßig Ihre Kontostände und Ihre Kreditwürdigkeit.
Abschließende Worte zum Thema Social-Engineering-Angriffe
Hiermit sind wir am Ende unseres Leitfadens angelangt. Wir hoffen, dass Sie jetzt ein besseres Verständnis davon haben, was Social-Engineering-Angriffe sind und wie Sie sie erkennen können.
Teilen Sie diesen Leitfaden auch mit Ihren Freund*innen und Verwandten! Je mehr Menschen sich der Social-Engineering-Taktiken bewusst sind, desto weniger Opfer wird es geben. Und wenn Sie noch Fragen haben, schreiben Sie uns gerne eine Nachricht: support@mailfence.com.
Möchten Sie tiefer eintauchen? Lesen Sie diesen Bericht von IBM, der zeigt, wie Cyberkriminelle die Identität von Menschen für ihre Angriffe ausnutzen.



