In today’s world, it’s becoming increasingly important to know how to protect your computer and devices.
Phishing attempts, ransomware, trojan horses … Cyber threats are becoming more present and more sophisticated.
And without the right protection, you risk data theft, reputational damage, extortion, espionage… So in this guide, we have gathered the 10 best ways to protect your computer and smartphone. And don’t worry: you don’t need to be a cybersecurity expert to put these recommendations into practice 😉
Before We Get Started…
First, we’d like to stress the importance of the physical security of your devices.
Needless to say that the first step to protecting your device is to never leave them unattended.
Most of us think of antivirus and strong passwords to protect our computer. But these will be useless if simply leave it unlocked at a coworking space. So lock your computer or smartphone when you’re not using them. To be extra secure, you can set a short “auto-lock” period, for example after 1 minute of inactivity.
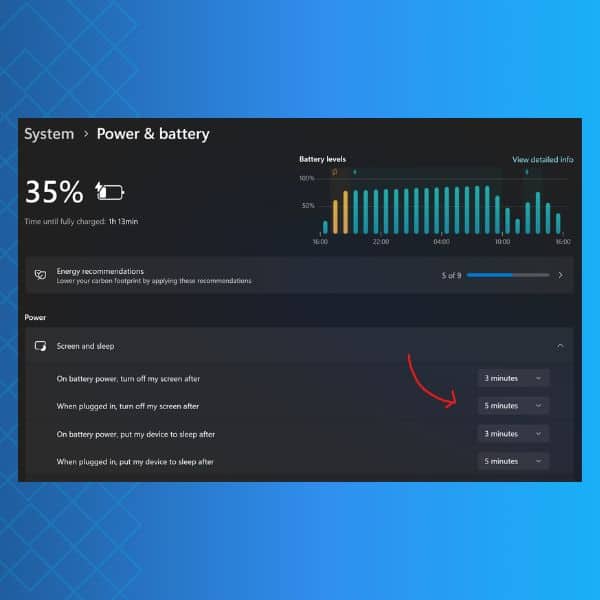
To do this on a Windows device, follow these step:
- go to Settings;
- navigate to System > Power and Battery;
- under Screen and Sleep, select after how long your screen should lock.
On a Mac device:
- go to the Apple Menu;
- navigate to System Settings;
- click the Lock Screen;
- enable “Start Screen Saver when inactive”;
- enable “Require password after screen saver begins or display is turned off” and set the desired time.
Make also sure to disable lock-screen notifications and Bluetooth. Thieves could use them to intrude into your device’s system. Once that’s done, you’re ready to move on to some more technical tips.
Tip #1: Connect to a Secure Network to Protect Your Computer
Being connected to the Internet is the easiest way for an attacker to gain access to your computer.
Make sure to connect to all the websites using SSL/TLS. You can also “harden” the devices that come with overly permissive factory-default configurations e.g., IoT devices, routers, etc.
Each device should privacy settings – go through when using your device for the first time.
Tip #2: Enable and Configure a Firewall
A firewall is a device that controls the flow of information between your computer and the Internet.
It prevents the disclosure of your personal data by creating a gateway. It will also warn you in case malicious individuals try to break into your computer system.
Most operating systems include a built-in firewall (Windows and macOS have theirs), as do the majority of home routers. This means you shouldn’t have to worry about setting up one, as your device is already protected.

However, you can strengthen your computer security by creating a strong password that will lock your firewall against any attempt to disable it (check your Wi-Fi operator guidelines for more information).
Tip #3: Use a Reputable Antivirus
Installing antivirus and keeping it up to date is a critical step in protecting your computer. Likewise, install an antivirus app on your phone. Be sure to keep them updated.
But antivirus is not a magic tool capable of erasing all threats. In fact, this software is based on a database of already known malware, listed in an internal registry.
Most often, antivirus updates aim to add new entries – i.e. newly discovered viruses – to this registry.
This means that they are unable to recognize a brand-new malware. So bear in mind, using an antivirus is not a silver bullet. It will not exempt you from applying other preventive measures.
Tip #4: Remove Unnecessary Software
Intruders can attack your computer by exploiting software vulnerabilities.
Consequently, the less software you have, the less vulnerable you will be.
This is especially true for smartphones. We have grown accustomed to downloading an app every time we need something. But we rarely think of removing them. This is a good habit to get into, as it will not only save space on your smartphone, but also protect you from software vulnerabilities.

Likewise, you can also disable and/or remove non-essential services that were installed by default.
Tip #5: Follow the PoLP (Principle of Least Privilege) to Protect Your Computer
In most instances of a malware infection, the malware can operate only under the rights of the logged-in user.
To protect your computer and minimize the impact the malware can have, consider having two kinds of user accounts :
- a standard account with the minimum of features for day-to-day activities;
- an admin one with full operating privileges on the system you’ll log in to when you need to install or remove software or change system settings on your computer.
If you accidently fall victime to a malware attack when logged into your standard account, the malware will be limited in what it can do and change to your system.
Tip #6: Use a Secure Web Browser to Protect Your Computer
Web browsers installed on new computers usually don’t have secure default settings.
Therefore, securing your browser is a critical step to protect your computer and smartphone.
An increasing number of attacks take advantage of web browsers. We recommend using either DuckDuckGo or Brave. Also, avoid unnecessary plugins and add-ons. Similarly to unused apps, they can represent software vulnerabilities.
Tip #7: Update Often
Most software vendors release updates to fix software vulnerabilities and bugs. Very often, the hacking of the software exposes these flaws.
To prevent hacking, it is therefore crucial to download updates as soon as possible.
Vulnerabilities can also be present in the firmware. A firmware is a utility software designed to provide secondary functionalities to your devices (such as allowing your device to connect to any type of printer, or to support a microphone or headphones).
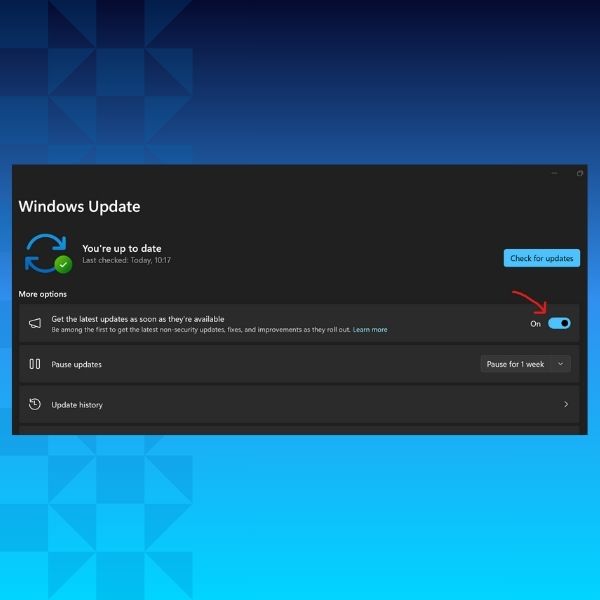
Most apps and programs should let you enable automatic updates. Make sure this feature is activated whenever possible.
Tip #8: Only Create Strong and Unique Passwords
Your password is the first line of defence against intrusions. It is also the least expensive tool to protect your device and the easiest to set up.
There are a few simple principles you should follow, which we detail in this article on password best practices.
In addition, password managers are extremely handy to avoid weak and re-used passwords. They help generate, store, and autofill complex passwords. If you opt for one, choose an “offline” option such as KeePass.
Tip #9: Use Two-Factor Authentication
Two-factor authentication (or 2FA) works as a second layer of protection after your password.
Most websites will offer to use it to secure your account. If a service doesn’t offer 2FA, you should probably avoid it.
And while entering a code every time you log in might sound cumbersome, it is one of your best line of defences against hackers.
Tip #10: Have a Backup
A hack is a lot less scary when you know all your data is securely backed-up.
Use backup software to schedule many backups a week, depending on your volume of computing activities.
Include all devices and software you use in your backup perimeter, and make at least two copies :
- The first one on an external hard drive (hard disk, USB key, NAS…) ;
- A second one on a cloud storage platform such as Mailfence documents.
Bonus Tips to Protect Your Computer!
I know we said we would share 10 tips to protect your computer, but we’re feeling generous 😊
So here are a few more tips you can implement today to protect your computer and laptop.
Tip #11: Elaborate your Disaster Recovery Plan
What would you do if your company was hit by a disaster tomorrow morning (consider a fire or ransomware intrusion)? Are you ready for this kind of scenario? Do you accurately know what you would have to do to prevent more damage and restart your business despite the loss of data or destruction of equipment?
If you’re unsure about the answer to this serious question, consider elaborating your own disaster recovery plan.
In the middle of the chaos, you’ll be grateful to have a to-do list to contain the risks, remedy the damage, and reactivate what can be restored.
Designing this type of program is not something that can be improvised, and you may need the help of an IT specialist to set it up and test its validity.
Tip #12: Encrypt your data
Encryption scrambles data and messages, usually using a mathematical key. To get back a readable data or message, the user will need to know this key to decipher it.
Encryption can not only be used to keep your communications private and secure. You can also use it to encrypt your various files and documents.
You can also encrypt your web traffic using a Virtual private networks (VPN).
It will encrypt your data before its transmission so that nobody can read it during its transit. The relevant data will only be deciphered at its destination (the website/software you’re communicating with).
Tip #13: Get a professional secure email
We’ve kept the best for last 😊
Your email is the favourite gateway for hackers to infect your devices with malware. This is why it’s crucial to pick and private and secure email provider such as Mailfence.
We are committed to providing the most private and secure email solution to our users. No tracking, no advertising. No third-party advertising or marketing trackers. We don’t even track your activity in the application. We are based in Belgium with strict privacy laws, and don’t rely on VC funding.
And you know what? The starter plan is free!
Email encryption, digital signatures, secure calendar and online storage… You can try out all these features in our free plan. In case of any questions, feel free to reach out to us at support@mailfence.com
FAQs: Protecting Your Computer and Smartphone in 2026
Before using digital protection tools like firewalls or antivirus software, ensuring your device’s physical security is essential. Always lock your computer or smartphone when unattended, set short auto-lock times, and disable lock-screen notifications to prevent unauthorized access.
A firewall acts as a gatekeeper between your computer and the Internet, filtering out unauthorized connections and preventing potential intrusions. Most devices come with built-in firewalls (e.g., Windows and macOS), but ensure they’re enabled and protected with strong passwords for maximum security.
Two-factor authentication (2FA) adds an extra layer of protection beyond your password. Even if a hacker guesses your password, they cannot access your account without the second code, which is usually sent to your phone or generated via an authenticator app
Email is a common entry point for phishing attacks and malware infections. A secure email provider like Mailfence uses encryption to keep your communications private and secure. Mailfence also offers additional tools like secure calendars, file storage, and digital signatures, ensuring your data stays protected.




