How well do you remember your passwords? If you’re like most people, you probably keep forgetting passwords. You might be guilty of reusing the same password on different accounts, or creating weak passwords.
In this article, we’ll go over 11 password best practices that you should start implementing now to not only be able to create stronger passwords, but also remember them more easily and keep them secure.
Lose the Bad Habits First
Humans are, for the most part, creatures of habit. Unfortunately, those habits are often bad and when it comes to bad password habits, these can drastically compromise your online security.
A lot of us are guilty of at least one, if not all of these top 5 bad password habits:
- Reusing passwords
- Not updating their passwords
- Using short passwords
- Storing their passwords in the browser
- Sharing passwords
You seriously need to ditch these today. Instead, here are 11 password best practices that you should be doing:
11 Password Best Practices You Need to Use Today
1. Use longer passwords
While using a 5-character password may be easier to remember, it’s also much easier to crack than a password that has 10+ characters.
According to the National Institute of Standards and Technology (NIST) guidelines, the minimum length for user-generated passwords should be 8 characters, though even this can be too short, depending on what they are protecting and who is trying to breach it.
For example, penetration testers at LMG Security were able to crack any 8-character Microsoft NT LAN Manager password hash in under 8 hours, while it would take them around 8 years for 10 characters, 77,000 for 12, 710,5 million years for 14, and 6.5 trillion years for a 16 character password hash.
2. Make your passwords more complex
Of course, if your password only contains one type of character, like lowercase letters, it will still be vulnerable to a simple dictionary attack.
The solution here is to not rely on just letters, but also to make your passwords more complex using a combination of lowercase and uppercase letters, numbers and special characters.
For instance, you can take a word, like “password”, which has 8 characters, so it fits the NIST guidelines and replace some of the letters with other symbols like this: “P@55w0rd”. Now you have uppercase letters (P), special symbols (@), numbers (55 and 0) and lowercase letters (r and d), which should make the password a little harder to crack.
3. Update your passwords
Given enough time and resources, any password can be cracked eventually.
As such, password security often becomes a game in which you constantly need to be one step ahead of the hacker and that means changing your passwords from time to time.
For a long time, the recommended frequency for password changes was 1-3 months. This, however, creates an additional problem. The more often the user is prompted to change their password or update it, the more likely they will simply use the same password, only slightly changed. This, ultimately, solves nothing.
NordPass, for example, recommends that you change passwords every year, saying:
Finally, there actually is a good period of time after which you should change your password: one year or so. It’s a good amount of time that lies neatly between being just short enough that you aren’t feeling forced to make a new password (and therefore a bad one) and just enough that you might start considering it a risk to your account security, especially to things like ransomware or a pharming attack.
4. Don’t reuse passwords
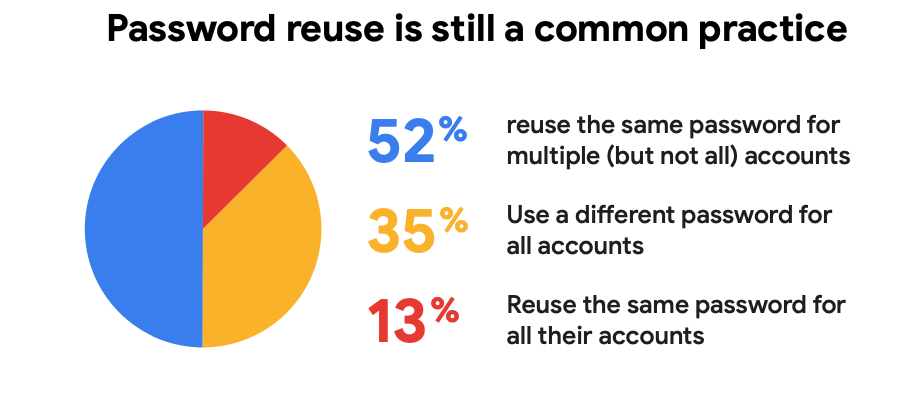
A 2019 joint study by Google and Harris Poll fully revealed just how common practice is password reuse.
According to the study, 52% of 3,000 U.S. respondents (16 to 50+ years) said they reuse the password on several (but not all) their accounts, 35% use a different password each time and 13% reuse the same password on all of their accounts.
Even if you are reusing the password on just two accounts, that’s pretty much doubling the chance of either ending up under the hacker’s control should any of the two accounts become compromised following a data breach.
Every account that you own should have a unique password to mitigate the threat of a data breach on one account affecting your other accounts.
5. Use Two-factor Authentication (2FA)
Relying on passwords as the sole account security is not enough as even the best one can be compromised, cracked, or leaked.
This is where Two-factor authentication or 2FA comes in.
2FA creates an additional verification method on top of the password. This can be a token, SMS message, fingerprint scan or something else that the user receives on another device they own. This way, the logic is that, even if someone manages to get your password, they wouldn’t be able to do anything without knowing the second verification method.
6. Don’t let the browser save your passwords
If you’re visiting a website for the first time and creating a password, your Internet browser will ask you to allow it to store your password.
While this sounds like a good idea on paper, it really isn’t. For companies that develop browsers, like Google or Mozilla, the primary focus isn’t on the security of their customers, but on usability and getting more customers. That’s why your passwords won’t be safe with them.
Don’t worry about needing to remember all your passwords. The next best practice is the solution.
Looking to password-protect a Google Drive folder? Check out our guide here.
7. Use a password manager to keep track and store your passwords
A study by NordPass from 2020 revealed that the average person has 100 passwords.
Naturally, remembering all these passwords would be incredibly difficult, which means forgetting passwords way too often and resorting to resetting passwords.
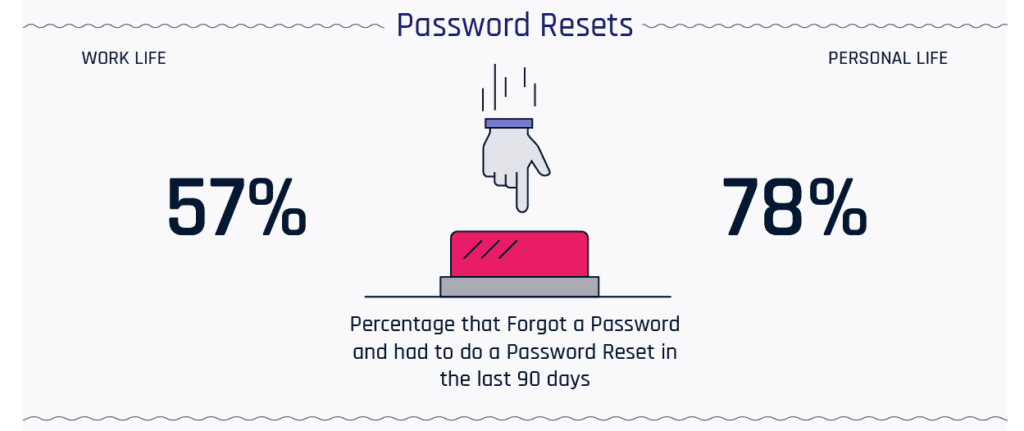
A study by HYPR from 2019, found that 78% of people had to reset a password they couldn’t remember in the last three months.
Luckily, there is an easy solution for storing passwords safely and making sure you never forget them – password managers, like NordPass, which we already mentioned.
However, don’t rely too much on password managers, as they can still be vulnerable to data breaches. This happened with LastPass in 2015, for example.
8. Randomize your passwords
Taking a common word and then replacing the letters with other symbols will make your password harder to figure out, but there’s an even better password best practice.
Using a password generator.
Every password manager also includes a generator that you can use to create secure and random passwords.
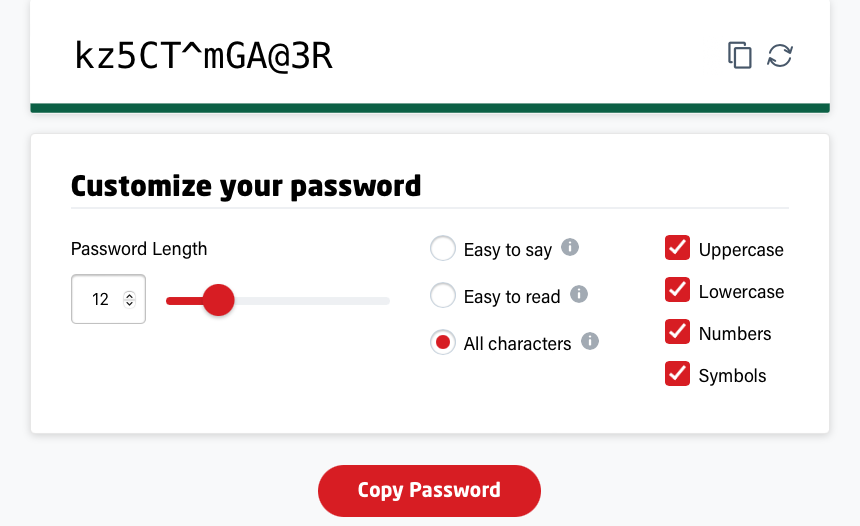
For example, with the LastPass Password Generator, you can set the password length up to 50 characters, use uppercase, lowercase, numbers and symbols, or choose a password that’s easy to say (avoids numbers and special characters, easy to read (avoids characters that can be mistaken for one another like 0 and O) or use all characters.
9. Check the security of your credentials
Often, what seems to us like a strong password, turns out not to be that strong at all and is easy to crack.
This is why you need to check your password strength from time to time. One tool that you can use for this is Kaspersky Password Checker.
All you need to do here is enter your password in the field and the checker will tell you how secure (or not secure) your password really is.
Another tool that you can use to check your account security is Have I been Pwned. This page lets you enter your email address to see if it has been found in any data breaches.
10. Salt & hash passwords
Another password best practice that NIST recommends is to use salt and hashing on your passwords.
In this case, first a random string of characters is added to the password (salt), before hashing the password. This adds another layer of security to the password and it becomes impossible for a hacker to break the password by reversing the hash.
11. Limit failed password attempts
People will often mistype passwords, but it makes no sense for a website to lock them out of their account after the first failed attempt.
Still, they also shouldn’t give a potential hacker too many opportunities to figure out the password.
The number of failed login attempts that you should allow is, of course, difficult to set, as it largely depends on your organization’s security risk level. For example, Microsoft recommends 10 as a good starting point before a lock.
Conclusion
Passwords were first presented as an idea by Fernando Corbato in 1960 at MIT and didn’t have much application beyond the academic world. However, with personal computers becoming more accessible and common in the 1980s, the necessity to protect private files became evident and that is where passwords found their use.
Here we are, around forty years later and we are still relying on passwords to secure our private files and accounts.
Today, the limitations of passwords are very clear. However, with these 11 password best practices, you can keep hackers at bay for a while longer at least.
In addition to these password best practices, we strongly advice you to learn how to protect your computer.
In the unfortunate case where hackers managed to enter your account, follow our tips to control the damage.
Besides following our password best practices, another way to ensure your data security is to use a secure and private suite like Mailfence. By getting a secure mailbox, you prevent hackers from getting access to your other accounts using the lost password function. Harden all your accounts with your encrypted mailbox!