Reclaim Your Privacy.
Welcome to the Mailfence blog.
Mailfence News
Introducing Contacts to the Mailfence Mobile App!
We are thrilled to announce that “Mailfence Contacts”, our contacts management solution, is now available inside the Mailfence mobile app! This new release follows the

Addressing your Feedback: An Anti-Spam Update
At Mailfence, safeguarding our users from spam, scams, and malware is a top priority. As a private and secure email solution, we are committed to
Introducing Documents to the Mailfence Mobile App!
We are very happy to announce that “Mailfence Documents”, our cloud storage solution, is now available inside the Mailfence mobile app! Alongside many other new
Email Security

Ransomware Attacks Are Surging – 8 Steps to Stay Safe
Ransomware attacks can lock you out of your own computer in seconds. What’s worse is that even if you pay the ransom, there’s no guarantee

Zombie Computer Takeover: How Hackers Use Your PC Without You Knowing
Zombie computers have become more relevant than ever in 2025. But most people don’t even know they exist. So in this guide, we are going

Whaling Attack: How Scammers Target Top Executives
Imagine receiving an urgent email from your CEO, instructing you to authorize a high-value wire transfer. Everything looks legitimate, but there’s just one problem… it’s
Online Privacy

It’s Time You Find a Google Alternative. Here’s Where to Start.
Finding a Google alternative can seem like a daunting task. If you’re like most people, you probably use several Google products on a daily basis.

Will Big Tech Mark the End of Western Democracies?
You’ve definitely heard of the term Big Tech before. You may even have an idea of what it means. What you may not know is

10 Killer Ways to Protect Your Computer and Smartphone
In today’s world, it’s becoming increasingly important to know how to protect your computer and devices. Phishing attempts, ransomware, trojan horses … Cyber threats are
Productivity

Email Greetings in 2025: The Best and Worst for Every Situation
Email greetings are your first opportunity to make a good impression on somebody. Did you know that making a great first impression when you meet

How to Block Emails on Outlook: 5 Easy Methods You Can Use
Being able to block emails on Outlook is like a superpower. We’ve all been there – the never-ending stream of unwanted emails cluttering your inbox.
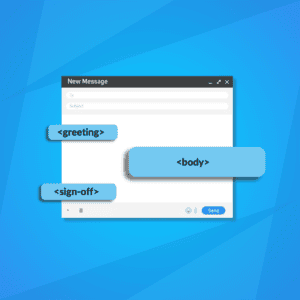
Email Layout: Definition, Types and Components
While you may not have the attention span of a goldfish, you still have to catch the reader’s attention fast with your emails. You can’t
Emails and More.
An integrated suite of tools.
Emails and More.
An integrated suite of tools.