Smishing is a social engineering attack based on SMS messages – and it’s exploding in 2026.
So in this guide, we are going to explore:
- what a smishing attack is and what it looks like;
- what you can do to protect yourself from smishing attacks;
- what to do if you fall victim.
Let’s explore!
Smishing Scams: What Do They Look Like?
First things first, let’s define what smishing is.
The word “smishing” is the contraction of “SMS” and “phishing.” It is a phishing technique using a text message instead of email.
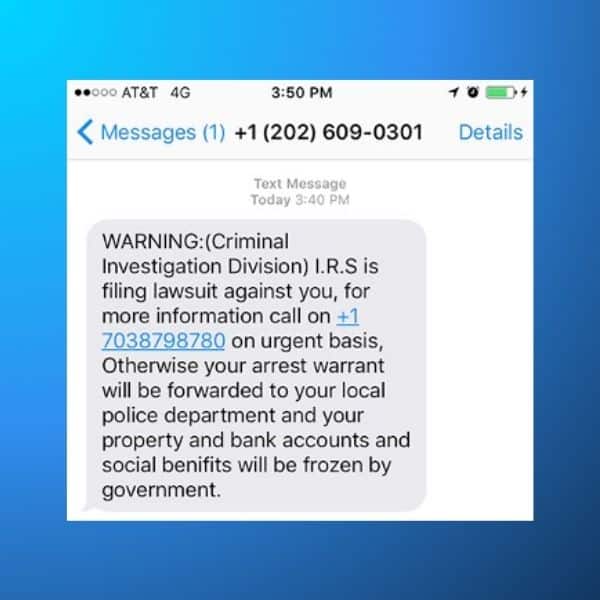
In other words, smishing is a cyber threat aiming to send you a virus or to make you do something harmful to yourself through a text message.
According to Proofpoint’s 2024 State of the Phish report, 3 out of 4 organizations experienced smishing attacks in 2023. And this number is only going to increase as the years go on.
Mobile phones are now an integral part of both our personal and professional lives. Think about the last time you didn’t have your phone within arm’s reach. According to recent studies, Americans check their phones 144 times per day.
Scammers know this and have now developed and deployed tactics to exploit our addiction to smartphones. Many smishing attacks use a “false sense of urgency” to leverage this trend more effectively. The malicious SMS sent conveys a sense of emergency to lure victims to take action even quicker.
What’s more, people are well aware that they should be careful with links in emails. “Never click on a link without double-checking” is usually the first thing you learn in a new job. However, people are much less aware that should be careful with text messages.
Attackers particularly like smishing since it’s a low-cost attack. Free burner phone numbers are cheap to purchase, and the cost of an SMS is trending toward zero. In addition, there is an increasing amount of phone numbers that have been leaked on the net – which is perfect if you are looking to launch a smishing attack.
Examples of Smishing Attacks
So, what does a smishing attack look like in practice?
A smishing SMS will always incite you to take action: either call a number or tap on a link.
It goes without saying that you should never call back a number mentioned in a text message or click on a link without double-checking. But we will get back to prevention methods later in this blog post. For now, let’s look at a few examples of smishing attacks.
1. The “fake delivery”
This type of smishing attack takes the form of a message “letting you know that there is a problem with your delivery”. You are then instructed to follow a link to resolve the issue.
In another scenario, you receive a link “to track the delivery of your parcel.
In both cases, scammers are using the increasing trend of online shopping to disguise their attack, hoping that you indeed have a delivery in progress.
If you did not request a tracking number, then do not click the link! It is likely a phishing attack. Likewise, do not call back the requested number if you are not expecting a delivery: you will likely fall on a scammer call center.
To learn more about this type of smishing attack, check out this announcement by the US Postal Inspection Service.
2. The fake “account suspension”
Another scenario is where you receive a text message alerting you that “your account is facing immediate suspension”, and that you need to follow a link or call a number to resolve it.
These smishing attacks often impersonate financial institutions of payment providers such as Mastercard or Paypal.
If you receive such a message, connect to your account through the usual means (mobile app, official website…). If you don’t see any notification there, then you can safely discrad the text message as a smishing attempt.
3. The fake “security alert”
We are accustomed to receiving emails from Google or Facebook alerting us to “suspicious connection activity”:
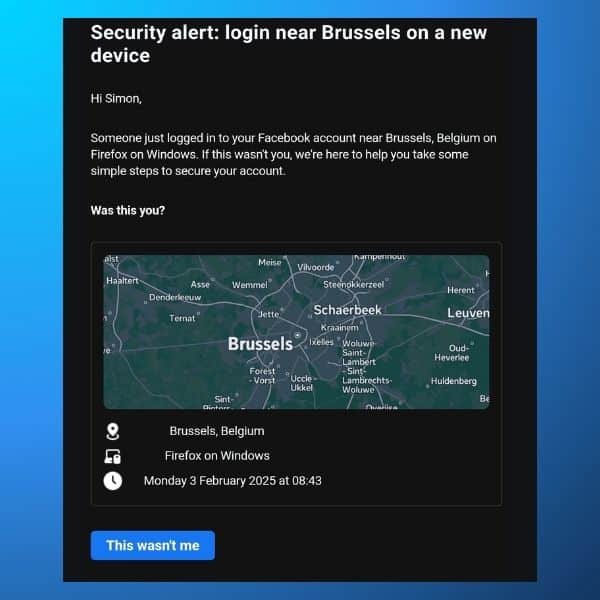
Scammers know this, and leverage this habit to send similar messages through SMS. However, keep in mind that these platforms will never send you a text message for this kind of alert, but always contact you via email or directly through their app.
Risks of Smishing Attacks
Like many cyber threats, a smishing attack aims to steal your personal data: bank account details, passwords, social security number etc.
Sometimes, smishing attacks also try to trick you into doing something: transferring money, downloading malware, giving access to your computer…
Smishing can lead you to visit a malicious website aimed at stealing your credentials or personal data. Alternatively, you could be led to call a fraudulent phone number. From then, cybercriminals on the phone could also launch a Quid Pro Quo attack or a Pretexting attack against you to get some sensitive information. For this, they would impersonate a manager of your company, a police officer, a security guard to ask you to give them your credentials.
But the most common risk is downloading a virus through the text message, or any other kind of malware, such as a Trojan horse.
This could turn your phone into a zombie, allowing hackers to control it. As a zombie device, it could become part of a botnet, and used to launch a Distributed Denial-of-Service (DDoS) attack, or to send some spam, …etc.
How to Recognize a Smishing Attack?
Here are some of the common signs of text messages that are actually smishing.
Suspicious phone numbers
Any SMS coming from a phone number that doesn’t look like a phone number, such as ‘0420’ – could be a sign that this text message is actually an email sent to a phone. This could also mean it’s a smishing attack, and that the text sent could contain a virus.
In fact, some hackers will use an email-to-text service to send their text message virus or any other kind of malicious SMS to hide their actual phone numbers.
Spelling mistakes
Informal language, grammar errors, typos… All these are signs of a smishing attack. Not only will an official institution rarely contact you by SMS, but they are unlikely to make spelling mistakes.
Suspicious link
Is the text message redirecting you with a shortened URL? Are they voluntarily hiding the end destination of the link? Then there is a high likelihood that this is a smishing attack.
Urgency
Urgency is a common technique used in social engineering scams. Attackers want to make you believe that you need to act very quickly.
The goal is to prevent the victim from using critical thinking about the consequences of their actions. Therefore, beware of any text message that requires you to take urgent action.
How to Protect Yourself from Smishing Attempts
Do you think you’ve received a smishing attempt? Then here are the steps you should follow:
- Never click on a link you get through an SMS. The only exception is if you know the sender personally (and are expecting this link). Even then, you should confirm that the link is safe with the sender directly.
- Is the SMS asking you to take immediate action? Then you should take extra precautions. Legitimate organizations will never pressure you to take “immediate” action, even if something is urgent.
- Be cautious with unusually short phone numbers. They can be issued by email-to-text services, used by hackers to hide their actual phone numbers.
- Never install any app by clicking on a text message. Always use official app store for installing apps.
- Never give away any personal or financial information by SMS or phone call.
- Don’t reply to text messages coming from people you don’t know.
- Avoid recording any banking information or card number on your phone. Even if your phone falls prey to a virus set up through a smishing attack, the hackers won’t be able to steal them.
- If you’re an organization, train your staff to follow our advice and to recognize all cyber threats and apply cybersecurity rules. They must refrain from sending confidential data via phone or email.
- Learn these 10 tips to protect your computer to minimize any impact an attack could have on you or your business.
- If you’ve been a victim of smishing or know that someone used your name for a smishing attack, you can also report identity theft at: https://www.identitytheft.gov/
- If you’re still unsure, simply ignore the text messages. If the matter is truly urgent, the bank or organization will find a way to contact you.
Famous Case Studies of Smishing
Now that we’ve covered the theory, let’s take a look at some real-world examples of smishing, and what we can learn from them.
The Fake Bank Alert Scam
In 2022, a smishing campaign targeted a woman in New Zealand. The scammers purported to be her bank (BNZ – Bank of New Zealand), redirecting her to a perfectly cloned but fake website.
There, she provided her login details, thinking she was connecting to her account. Instead, she then saw money being transferred out of her account.
In total, she was scammed out of US$ 42,000. Another man who fell for the same smishing attack lost US$ 37,300.
The Fake FedEx Delivery Notification
In late 2022, a smishing attack disguised as a fake FedEx delivery notification spread across Europe. This scam tricked users into clicking a link to “track their package,” but instead, it downloaded the FluBot malware onto their devices.

The FluBot malware has first spotted in 2020, and then spread across Europe in 2021 and 2022.
Once installed (under the disguise of a “tracking app”), the malware would ask for accessibility permissions, before stealing banking app credentials or related financial account details.
To learn more about this kind of smishing attack, check out this announcement by the Federal Trade Commission as well as this breakdown of the FluBot malware by EuroPol.
OCBC Bank Smishing Scam
In 2022, the OCBC Bank in Singapore reported that approximately US$ 10 million was stolen from a total of 790 customers due to an advanced smishing attack.
Attackers used advanced social engineering techniques to trick customers into handing over sensitive data. In particular, the messages appeared extremely genuine, using official-looking branding and urgent language.
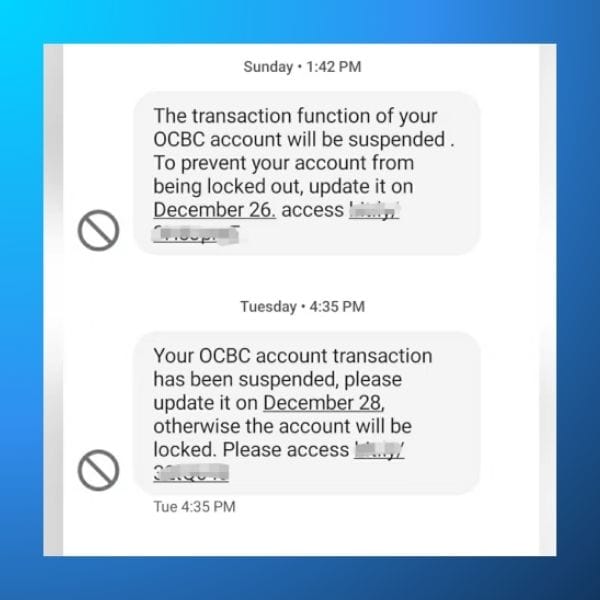
Once redirected to a phishing site, victims provided their online banking credentials and PINs. This enabled the scammers to take over their bank accounts and make fraudulent transactions.
Because of the difficulty of recovering lost funds, OCBC agreed to refund personally the affected customers.
What can we learn from these attacks?
- Never click on links in unexpected SMS messages from banks or financial institutions such as PayPal.
- Never install any app that is provided to you in an unsolicited SMS.
- If in doubt, connect to your bank through the usual means (official app, official website).
- Additionally, call your bank directly to verify and report any suspicious activity.
- Finally, enable 2FA to prevent unauthorized access to your accounts.
Conclusion
This wraps up this guide on smishing attacks! We hope you found it useful and will be able to spot smishing attacks in the future.
As a final reminder, you should never trust unsolicited text messages coming from your bank, your employer, or even a friend which include links to an app or website.
If you want to take your cybersecurity further, then your first step should be to get a private and secure email provider. Here at Mailfence, we pride ourselves on:
- Advanced security tools: end-to-end encryption, symmetric encryption, digital signatures, and a lot more.
- No tracking or advertising. We do not use any third-party advertising or marketing trackers. We do not track your activity in the application. Mailfence is completely free from ads.
- Strict privacy laws. Mailfence’s servers are based in Belgium, with strong laws protecting privacy. Only a valid Belgian court order can force us to release data.
Interested in taking your privacy and cybersecurity to the next level? Create your free account today!




