What Does Bcc Mean in Email?

Email etiquette includes a variety of important rules that one should master in order to communicate efficiently via email. One such rule involves communicating appropriately with a group of individuals while also ensuring their privacy is respected. This is where the Bcc field, which you can find next to the “To” field, comes into play: […]
What Does Cc Mean in Email?

While email is already decades old, its roots are even more profound and go back to when all communication was done using paper. The best example of this is the Cc email feature. In this article, we’ll explain what Cc means in email, how to add someone to Cc, and how to use Cc properly. […]
The Ultimate Email Etiquette Guide to Make Your Emails Professional
Writing an email is an important communication skill nowadays. That’s why we want to follow the appropriate email etiquette. So what is email etiquette, why is it important, and how to follow it when you want your emails to look professional? We’ll cover all of that in this article, so let’s dive in right away. […]
How to Write an Out of Office message?
Are you going on a vacation, taking a sick leave, or just need a day for yourself without anyone bothering you? Then it’s important to let people know that you won’t be in your office for awhile. The best way to do that is via an out of office email message. In this article you’ll […]
Mailfence News : Plans, Short Domain & More

We are happy to share with you the latest Mailfence news and would like to thank you all for your support and contribution to the fight for a better internet. Mailfence would simply not exist without our powerful community of users, ambassadors, volunteers and partners. 2022 was a year of growth and security improvements New […]
End-to-End Encryption. What Is It and How Does It Work?
What is end-to-end encryption? End-to-end encryption is a method of securely transmitting data in a way that only the sender and recipient can read the actual message by encrypting it on the sender’s end and decrypting it on the recipient’s. Any third party, like a malicious actor, that tries to access or tamper with the data as […]
Symmetric vs Asymmetric Encryption: What’s the difference?
In this blog post, we explain the major differences between symmetric vs asymmetric encryption. This article will also explain which encryption method you should use. Some words about different encryption methods In today’s world, scammers and other cybercriminals are becoming increasingly present, affecting millions of users. To prevent these individuals from stealing our data, we […]
POP3 vs IMAP vs Exchange ActiveSync. What’s the difference?
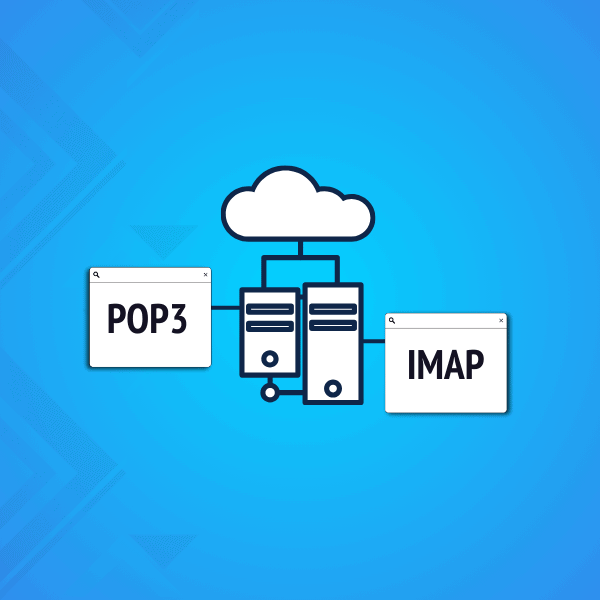
In this blog post, we compare POP3 vs IMAP vs Exchange ActiveSync. How do these protocols work? What are their pros and cons? We will conclude by giving tips on how to use them with your Mailfence account. Post Office Protocol (POP3) In POP3, the mail server receives all the emails sent and stores them […]
Social Engineering: What is Phishing?
Phishing is the most well-known social engineering attack, where a cyberattacker pretends to be a reliable source to make their victims reveal their personal information or download malware. According to the National Institute of Standards and Technology (NIST), there are more and more phishing attacks each year, with a staggering rise of 61% since 2021. […]
Social Engineering: What is Shoulder Surfing?
Shoulder surfing is the practice of stealing sensitive information by looking over another person’s shoulder while they are keying that information into the device. What is Shoulder Surfing? You’re on a bus, reading the newspaper or something on your screen, when you feel a sensation at the back of your brain. You turn around to […]