OpenPGP is one of the standard protocols for encryption/signature of data. It is the most widely used email encryption standard. It’s also one of the ways Mailfence provides security and privacy for its users across the globe.
OpenPGP and Privacy Concerns
If you ask folks today are they concerned over the use of their data by the Government or companies, most people would say that they are. According to a study by the European Union Agency For Fundamental Rights (2020), more than half of people using the Internet fear criminals could use the information they share online.
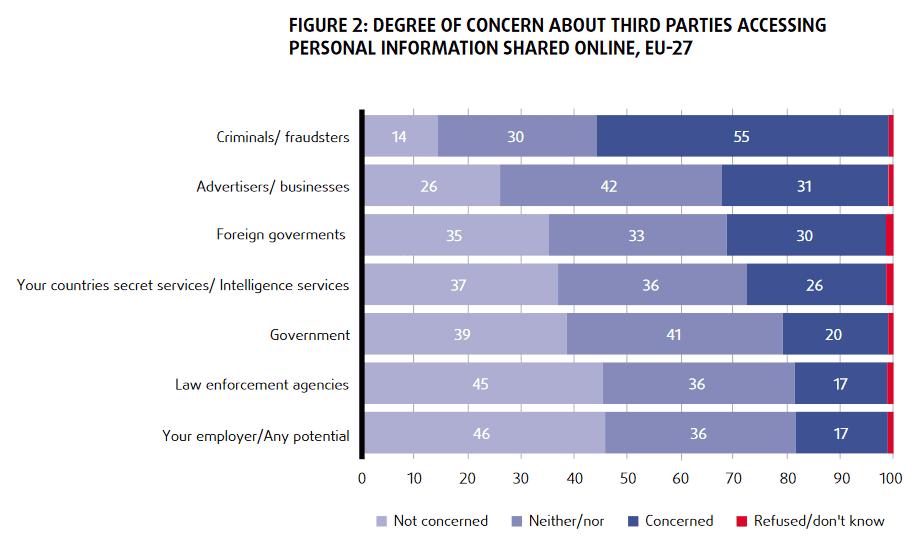
At the same time, across the ocean, Americans are concerned as well, and yet feel it’s impossible to go through life without having their data collected by companies (62%) or the government (63%), according to research by Pew Research (2019).
But here’s the thing. You’re right to be bothered by data collection. You do have control over your privacy, and one thing that can help you with this is OpenPGP.
What is OpenPGP and How Does it Work?
Encryption, cryptography, digital signatures, private and public keys… These are all ideas and tools that an average person has probably heard of but doesn’t really understand. And what people don’t understand usually scares them.
This is why we believe it would be incredibly useful to talk about one of those tools, namely OpenPGP, how it works and how it can help with your email privacy.
Okay, What is OpenPGP?
PGP stands for Pretty Good Privacy and is an encryption system for sending encrypted emails and files. It was created and released in 1991 to protect files on bulletin board systems (these were servers used to allow users to connect before the Internet).
Originally, PGP was free to use by anyone, but after Symantec bought it, it became a proprietary solution.
This is why Phill Zimmerman, the original author of PGP standard, submitted an open-source proposal to the Internet Engineering Task Force (IETF) in 1997 and thus OpenPGP was born.
OpenPGP is an encryption standard that uses both symmetric and asymmetric cryptographic algorithms. With this, OpenPGP takes the best from both – the efficiency of symmetric encryption and the security of asymmetric.
How Does it Work?
Pretty Good Privacy isn’t all that complicated in fact. Let’s take a look at an example.
- Person A (sender) wants to send their friend, person B (recipient), an email, but they want to keep it private.
- Now, person B (the recipient) needs to generate a public and private key. Check how to generate your personal key with Mailfence.
- Next, person B sends their public key to person A.
- Using the public key they just received, person A can encrypt their email.
- Now they can send the encrypted email to person B.
- Finally, to read the message, person B needs to decrypt it using their private key. Anyone else intercepting the email wouldn’t be able to read it, as it would be incomprehensible to them.
What is the Difference Between PGP, OpenPGP and GnuPG?
We’ve already touched on how OpenPGP was submitted as a proposal to the IETF in 1997 by PGP’s creator Phil Zimmerman to avoid its patent issues.
There is also a third player in this story, and that is GnuPG or Gnu Privacy Guard (GPG).
Gnu Privacy Guard was developed two years after OpenPGP in 1999 and is based on the OpenPGP standard that Zimmerman submitted to the IETF. It is a free alternative to PGP that users can download, modify, distribute and use to encrypt/decrypt PGP and OpenPGP files.
Recap: Original PGP was developed in 1991 and later bought by Symantec, then OpenPGP was submitted and approved by the IETF in 1997 as a free alternative, and then GPG was released in 1999, based on OpenPGP standard.
What is PGP/OpenPGP Used For?
So, what can you actually do with PGP or OpenPGP?
- Encrypt/Decrypt emails (or files)
- Sign/verify emails (or files)
- Sign/verify actions
The example above (see “How Does PGP Work?”) already explains how OpenPGP is used to encrypt an email between two parties who want to keep their correspondence private.
OpenPGP can also be used to verify the identity of the person sending the email. Or, in short, perform email signature verification.
This is done by using OpenPGP Digital Signature – which is essentially a hash of the email encrypted using the sender’s OpenPGP private key. This email digital signature is then sent with actual email.
Once the recipient gets the email, they can decrypt the digital signature using the sender’s public key. This way, the recipient will know if just one character was changed, indicating that either the message was tampered with in transit, or the Digital Signature is fake, and the sender is not who they claim they are.
Finally, besides encrypting and signing email or other files, OpenPGP can also be used to sign actions e.g., establish identity trust, revision to a Github/Gitlab repository, publish Debian upstream package.
Pros and Cons
OpenPGP definitely has its advantages, but it’s not perfect. Next, we’ll take a look at the pros and cons of OpenPGP encryption:
Pros
- It’s free to use, download and modify
Unlike PGP, which is now owned by Symantec, OpenPGP is completely free to use by anyone.
- It is practically unbreakable and highly secure
OpenPGP encryption keys are usually up to 4096 (asymmetric cipher) and 256 (symmetric) bits length. This is, currently, regarded as secure by various standardization bodies like NIST.
- It improves cloud security
OpenPGP can be extremely useful for encrypting files at rest (on servers) and adding extra security on the cloud in case of a username and password breach.
Cons
- It’s not anonymous
OpenPGP is a privacy and security tool, not an anonymity one. Remember, privacy keeps your actions unknown to others, while anonymity keeps your identity unknown. This means that both the sender’s and recipient’s identities can be traced back to them. That is, unless they use an email alias, VPN, or proxy server.
- It can be intimidating
Although you get used to it after a while, for first-time users, PGP can be pretty complicated to set up and use. This especially goes for generating and managing key keypairs. This is why a lot of people will avoid it and hope for the best.
Mailfence managed to make it much easier for anyone to use it:
- Generate or Import a Private and Public key.
- Share public key by email or check this blogpost to share Public key in three easy steps.
- Discover and import recipient Public keys using latest standards.
- Send signed and/or encrypted emails.
- Both the sender and recipient need to have it
OpenPGP won’t work if only one side has it installed. Both the sender and recipient must have OpenPGP compliant program to be able to use it successfully. Again, Mailfence found a solution for this con: using only symmetrical encryption when one side doesn’t support OpenPGP.
Do I Need OpenPGP?
The answer to this shouldn’t be based on how complicated it is to use it or how much it costs.
Rather, it should depend on the necessity to protect your sensitive data over email or your files. Despite some media claiming that OpenPGP is dead, this is far from the truth. More and more people realize that the Internet is not secure and that they need to protect their data.
Mailfence uses OpenPGP encryption to protect your emails without hassle. Every account has an integrated OpenPGP keystore to give you full control over your keys!
Furthermore, Mailfence offers a private and secure email suite that includes a calendar with polls and groups management, a chat service and a document storage and management tool, all secured by end-to-end encryption, digital signatures and 2FA.




