Zombie computers have become more relevant than ever in 2026. But most people don’t even know they exist.
So in this guide, we are going to uncover everything you need to know about zombie computers, including:
- what zombie computers and botnets are;
- how does a computer become a zombie computer;
- what do to if you realize you have a zombie computer;
- 7 steps to prevent zombie computers from happening.
Let’s explore.
Get the latest privacy news in your inbox
Sign up to the Mailfence Newsletter.
What is a Zombie Computer?
A zombie computer is a computer that can be controlled remotely.
A zombie computer is the result of a cyber-attack. Thanks to a piece of malware (often unwittingly installed through a phishing attack), the hackers can now control your computer remotely. Very often, they will make it “work” with other zombie computers, forming what is called a botnet.
Why would a hacker want to control your computer remotely? Here are a few nefarious use cases of zombie computers:
- DDoS attacks: hackers use zombie computers as part of a botnet to flood a target website or server with excessive traffic, overwhelming it and causing downtime.
- Phishing and spam attacks: a zombie computer can be used to send spam emails or phishing messages without tracing back to the hacker. This helps them distribute malware, ransomware, or steal login credentials from unsuspecting users. Not sure what the difference between phishing and spam is? Check out this guide.
- Cryptocurrency mining: with the rise of Bitcoin and cryptocurrencies, hackers use zombie computers to mine various cryptocurrencies without the owner’s consent. Since mining requires substantial processing power, spreading the workload across multiple zombie computers allows hackers to profit while draining victims’ CPU power and slowing down their devices.
The worst part? You might often not even realize that your computer has become a zombie computer.
That is why, in the rest of this guide, we will cover “tell tale” signs of zombie computers, and how to prevent yours from becoming one.
How Do Computers Become Zombie Computers?
There are many ways in which a computer can become a zombie computer. Many of these will be similar to phishing and ransomware attacks, which is why we recommend you check out those guides too.
Phishing emails
Phishing emails are one of the most common attack vectors for hackers. Thanks to social engineering tactics, we can all be manipulated into revealing sensitive data or installing malware.
Hackers often use phishing emails containing malicious attachments or links to infect computers. Once the user interacts with these elements, malware is installed, converting the computer into a zombie computer.
One such example is Jeanson James Ancheta, known as the “Zombie King”. In 2004, he managed to highjack thousands of computers thanks to malware distributed through phishing emails. Once the botnet was established, he “rented out” those computers to other cybercriminals so they could pursue their own attacks (DDoS, spam campaigns etc.).
He was eventually sentenced to 5 years in prison, the first prosecution relating to a botnet attack.
You can read more about this case on the US Department of Justice website.
Exploitation of Software Vulnerabilities
Cybercriminals exploit unpatched software vulnerabilities to install malware on computers. By targeting these security gaps, they can remotely execute code, turning the compromised systems into zombie computers.
One such example was the Conficker botnet, which led to an estimated 10 miilion zombie computers.
Thanks to a Windows vulnerability, attackers were able to infect machines through regular software updates the users would do.
You can read more about this attack on the dedicated Conficker wiki page.
AI-enhanced USB drives attacks
A hacked USB flash drive can autonomously infect a PC the moment it’s plugged in. AI makes these attacks even more advanced by detecting the type of device it’s connected to and adjusting its behavior accordingly.
For example:
- AI determines whether it’s plugged into a personal laptop, work PC, or server.
- AI waits for the perfect moment (e.g., when the system is idle) to execute the attack.
- AI spoofs legitimate software behavior to avoid detection.
For example, a hacker could leave a USB stick with the words “Confidential Salary Data” in an office parking lot. A curious employee plugs it into their work computer, activating AI-driven malware that turns his computer into a zombie computer.
Drive-by downloads
Visiting compromised or malicious websites can result in drive-by downloads.
A drive-by download is a download which was authorized by a user without understanding what is being downloaded.
This usually leads to malware being automatically installed without the user’s consent when visiting a malicious website, turning their computer into a zombie computer
In 2024, the FBI dismantled a botnet that had infected millions of computers across nearly 200 countries.Many of these infections occurred through drive-by downloads from compromised websites, highlighting the risks associated with untrusted online sources.
You can read more about this case of the World Economic Forum (WEF) website.
Common Signs of a Zombie Computer
Now that you know how your computer can become infected, here are some red flags to look out for if you think your computer has become a zombie computer:
- A part of your hard disk or flash storage seems to have disappeared.
- Your browser often closes for no apparent reason.
- Inexplicable error messages pop out randomly.
- Your computer takes a long time to start up and shut down.
- Your fan is going into overdrive even though your PC is supposed to be idle.
- There are emails in your “Sent” folder you don’t remember writing.
- Some security websites block you from accessing them.
- You can’t download or install antivirus programs or updates.
- Windows Task manager shows suspicious programs you can’t account for.
If you can relate to one or more of these assumptions, there’s a slight possibility that your computer has become a zombie.
What To Do If You Have a Zombie Computer?
The first thing to do to try to recover your computer from a zombie attack is to run a scan of your antivirus. You’ll have to install an antivirus if you don’t have one. You can then run a scan of your entire system to detect any potential malware.
Very often, if your antivirus finds some virus or malware, it will suggest to you some steps to get rid of it. We advise you to follow them carefully. In many cases, it’ll manage to get rid of the problem, and you’ll recover your computer.
But sometimes, it won’t work and your antivirus will prove unable to remove the malware. In this case, you can only erase your computer’s hard drive(s) and reinstall your operating system and software.
In this scenario, you will lose all the data that has not been backed up. This highlights the importance of regular and comprehensive backups.
7 Steps to Prevent Zombie Computers
At Mailfence, we prioritize your privacy and security, offering a suite of features designed to protect your communications. Here’s how you can improve your email security and avoid your computer becoming a zombie.
SSL/TLS protocols
Mailfence ensures that all communications between your device and our servers are encrypted using SSL/TLS protocols, safeguarding your data from interception.
However, we do recommend you monitor your active sessions within the Mailfence interface to detect any unauthorized access:
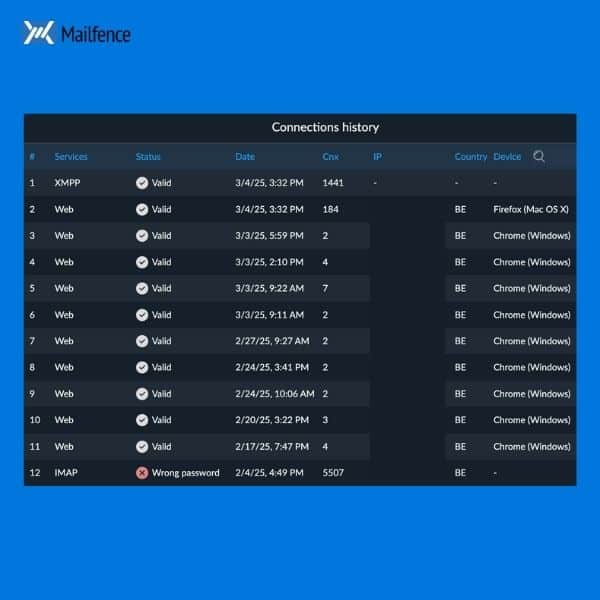
Recognize and avoid phishing attempts
Phishing attacks deceive users into divulging personal information through fraudulent emails. Recognizing these threats is crucial.
Here’s how you can identify suspicious emails:
- Sender address: be wary of emails from unfamiliar sources or those mimicking legitimate organizations.
- Urgent/threatening language: emails pressuring immediate action, such as “Your account will be suspended,” are red flags.
- Generic greetings: authentic communications typically address you by name rather than generic terms like “Dear User” or “Dear Sir”
- Unexpected attachments or links: never click on unknown links or download attachments from unsolicited emails.
If you think you’ve received a phishing email:
- Do not engage and refrain from clicking links or downloading attachments.
- Verify the sender by contacting the organization directly using official channels to confirm the email’s legitimacy.
- Report the email: alert your IT team or your email provider (you can reach us at support@mailfence.com)
- Delete the email from your inbox to prevent accidental interaction in the future.
It’s important not to confuse phishing with spam – check this blog post to learn the difference.
Keep your software and security patches up-to-date
Outdated software can be a gateway for cyber threats. Regular updates are essential to maintain security.
This is why you should configure your operating system and applications to update automatically, ensuring you receive the latest security patches.
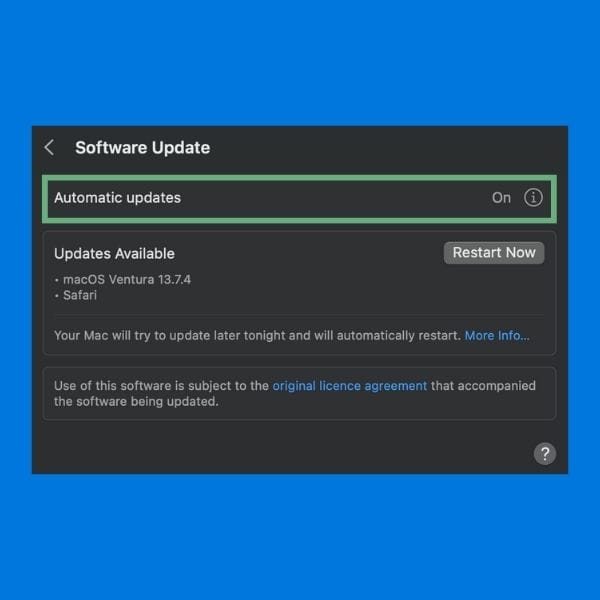
Likewise, regularly check that all software, including Mailfence, is up to date.
Enable 2FA everywhere
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification during login.
Make sure 2FA is enabled on every account you use (emails, social media, financial accounts…) where it is supported.
In your Mailfence account, you can navigate to your Settings > Account > Security, and set up 2FA there.
Plugins/Add-ons
Beware of browser plugins/add-ons and non-trusted apps and avoid giving them unnecessary permissions.
Always download browser plugins from the official browser store (Firefox/Chrome/Brave etc.) and never from a random email or website.
Don’t use pirated software
It goes without saying, but don’t use pirated, cracked, or otherwise illegal copies of programs. Only download them from trusted sources.
Beyond the ethical and legal concerns (pirating software is theft), there is a high likelihood that you will end up with some kind of malware on your computer.
Encrypt your emails
For maximum privacy and security, encrypt all your emails. You can do this with either end-to-end encryption or symmetric encryption.
Encryption ensures that only the intended recipient can read your emails, protecting your content from unauthorized access.
You can check out this guide to learn how to use encryption easily with Mailfence.
Zombie Computers: Last Words
That’s it for this guide on zombie computers. Hopefully you now have all the keys to understand this cyberthreat, and how to protect yourself.
If you want to take your cybersecurity further, then your first step should be to get a private and secure email provider. Here at Mailfence, we pride ourselves on providing:
- advanced security tools: end-to-end encryption, symmetric encryption, digital signatures, and a lot more.
- no tracking or advertising. We do not use any third-party advertising or marketing trackers. We do not track your activity in the application. Mailfence is completely free from ads.
- strict privacy laws. Mailfence’s servers are based in Belgium, with strong laws protecting privacy. Only a valid Belgian court order can force us to release data.
Interested in reducing your digital footprint and taking your cybersecurity to the next level? Create your free account today!