Reclaim Your Privacy.
Welcome to the Mailfence blog.
Mailfence News

Mailfence Launches its Privacy and Cybersecurity Newsletter!
We are thrilled to announce the launch of the Mailfence Privacy and Cybersecurity Newsletter! Here at Mailfence, we strongly believe that knowledge is power. That
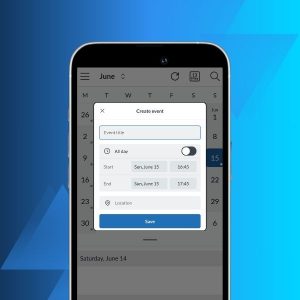
Introducing our Calendar to the Mailfence Mobile App!
We are very happy to announce that “Mailfence Calendar”, is now available inside the Mailfence mobile app! Alongside many other new features and improvements, this

Mailfence: The Perfect Email Solution for Attorneys in 2025
In this Customer Success Story, we share the story of AVOCATS.BE, the organization responsible for defending the interests of all the bar associations in the
Email Security

Gmail vs Mailfence: A Full Comparison Guide (2025)
In 2025, choosing between Gmail vs Mailfence goes beyond just emailing. It’s about control, privacy, and trust. Gmail, from Google, dominates with advanced features, powerful

Proton Mail vs Mailfence: A Full Comparison Guide (2025)
Concerns around digital privacy and security have never been higher. And if you’re still using Gmail and Google products in general, it’s time for you

Hide My Email: The Ultimate Privacy Hack in 2025
In 2025, sharing your email address online is like handing out your home address to strangers. It’s how companies track you, spammers find you, and
Online Privacy

Can You Password-Protect a Google Drive Folder in 2025?
Google Drive is great for storing and sharing files, but can you password-protect a Google Drive folder in 2025? The short answer is: not directly.
Escape US Surveillance: 8 Top European Alternatives to Big Tech
Concerns about data collection, surveillance, and lack of transparency have triggered a growing backlash against Big Tech. Companies like Google, Amazon, Meta, and Microsoft dominate

What is the Dark Web? Everything You Need to Know
The dark web remains one of the most misunderstood parts of the internet. Often associated with cybercrime and secrecy, it also serves as a critical
Productivity

What is an Email Trail? Everything You Need to Know
Email remains one of the most widely used professional and personal communication tools. Yet, as inboxes grow and conversations evolve, the term “email trail” becomes

WhatsApp Alternative: The 3 Best Options to Switch To in 2025
With 2 billion monthly active users as of February 2025, WhatsApp remains the king of messaging apps. However, if you’re like me, you might be

Email Filtering: 7 Tips When Using Email Filters in 2025
Ah, “inbox zero”—that elusive dream we all chase. It’s almost like reaching the top of Mount Everest, except Everest doesn’t get more emails every 10
Emails and More.
An integrated suite of tools.
Emails and More.
An integrated suite of tools.