Scareware is a social engineering technique that aims to scare the victim into believing they have a virus on their device.
The ultimate aim of scareware attacks is to make the victim download a nefarious piece of software (malware).
Once installed, this malware can give attackers access to sensitive data, or even remote access to the computer. In this guide, we will look in detail at:
- what scareware attacks look like;
- how to protect yourself from scareware;
- and the impact of AI on scareware tactics.
Let’s explore.
What is Scareware?
First things first: what is scareware?
Scareware comes from the contraction of “scare” and “software”; i.e. scaring you into downloading a software.
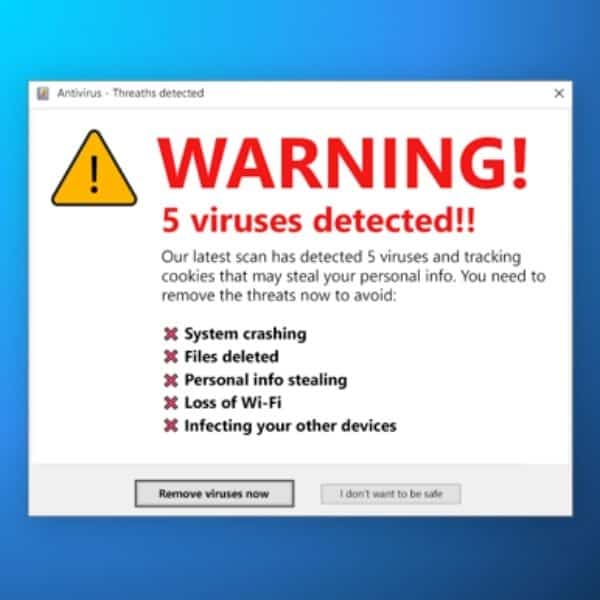
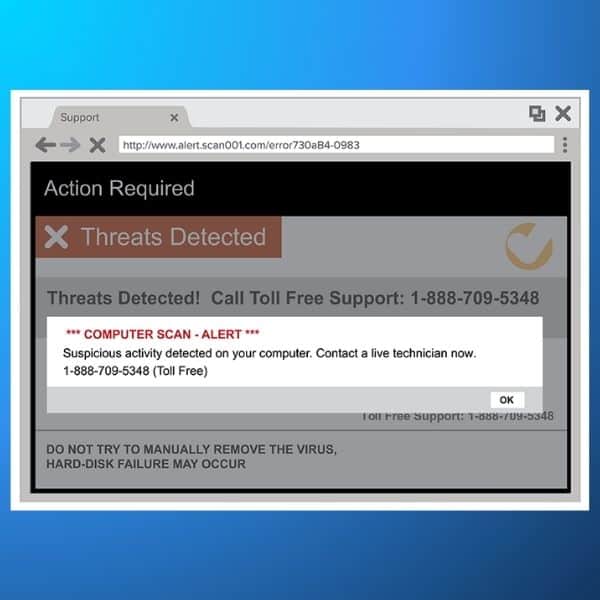
Have you ever seen a pop-up on your screen saying something like:
- “Warning! Virus Alert!”;
- or “Warning! 5 Virus Detected!” ?
That is exactly scareware in action. Attackers want to convince you (through fear) that your device is infected with a virus and that you should download (or sometimes purchase) a malicious software:
Like other social engineering techniques, scareware plays on human emotions and reactions:
- sense of urgency: people often act without thinking when they believe there is an immediate and urgent threat;
- fear: faced with a sudden sense of panic, people often forget to double-check for warning flags. They are lured into taking action without taking the time to consider the implications of their actions.
It’s important to note that scareware is usually the first step in a more intricate cyberattack, and not an attack in and of itself. Scareware usually presents itself as a pop-up, redirecting you to a bogus website. There, you might be asked to download some malware or enter some credentials.
More broadly speaking, scareware belongs to a class of attacks called “tech support scams”. These scams, which can also occur through messages (smishing) or phone calls (vishing), take the appearance of “helping you protect your computer”.
Real-World Case Studies of Scareware
Let’s now look at some real-world examples of scareware, and the impact they had.
The MAC Defender scareware attack (2009)
In 2011, Mac users cames across “MAC Defender” for the first time.
When users would search terms like “mac removal virus”, they would land on fake antivirus websites. These websites would alarm them even more, saying that their computer was infected with multiple viruses.
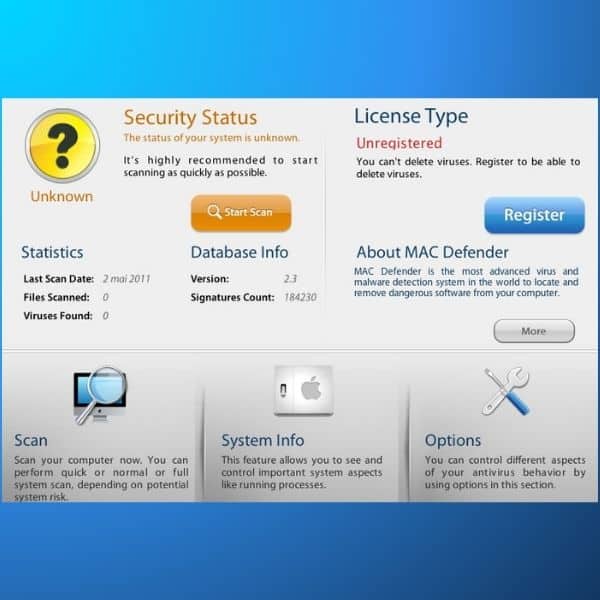
Once installed, it bombarded users with fake virus warnings. It then demanded payment for a “premium” version to remove the supposed threats (between USD 60 and USD 80).
Very quickly, tens of thousands of calls were being made to Apple support, all relating to MAC Defender. In May 2011, Apple eventually issued instructions to remove the software, and issue a security update that would automatically remove MAC Defender.
The Minneapolis Star Tribune attack (2010)
In 2010, visitors to the Minneapolis Star Tribune website were targeted by popups saying their computer was infected.
To achieve this, the attacker created a legitimate advertising agency displaying legitimate ads on the website.
However, those ads were later replaced with fraudulent ones, prompting users to buy antivirus software for $49.95. When they realized the scam, the Start Tribune disabled all online advertising on their site. An investigation was launched, leading to an arrest in 2016.
In 2018, the man behind the scam, Peteris Sahurovs, was sentenced to 33 months in prison. It is estimated he made between US$ 150k and 250k from his scheme.

You can read more about this case on the Department of Justice’s website.
How to Spot Scareware?
Scareware typically comes in the form of a pop-up that is made to look like it comes from a software company. Here are 5 common red flags:
- it comes from a software company you’ve never heard of;
- somehow, the software has already scanned your device and detected all these viruses;
- you find it hard (or almost impossible” to close the pop-up;
- there is a sense of urgency (“you must act fast”, “download now!”);
- the pop-up headline will always be something scary like like “Warning!” or “Virus Detected!”
How to Avoid Scareware?
Knowing how to spot scareware is the first step in avoiding it. Here are some additional tips:
1. Never react immediately
The attackers are trying to play on your emotions and are using scare tactics to manipulate you into making a hasty decision. Take a deep breath, slow down and assess the situation.
2. Think rationally
Read between the lines and think rationaly:
- Have you ever heard of this particular software security before? Know that legitimate companies, like Norton, Kaspersky, and others will never do something like this.
- how is it possible that they already scanned your device and detected those viruses if you never interacted with them or their software in the first place? In general, you need to download the antivirus software first before it can scan your computer and detect any viruses. A full scan can then take up to several hours.
3. Don’t blindly click on links
Don’t click on a button or a link just because it says “click me!”. If you are unfamiliar with this company or the URL looks suspicious, it will likely lead you to a malicious website or download infected software on your device.
4. Directly close your browser
Lots of scareware pop-ups use a fake Close or X button that clicking on will actually download malware on your device instead of closing it. This is called clickjacking.
To avoid this, close the browser entirely.
5. Use Firewalls, Pop-Up Blockers and URL Filters
Use these three to stop pop-ups from appearing on your screen and facilitate this social engineering attack.
6. Use Only Legitimate Security Software
Again, legitimate security software companies will never send you pop-ups like these, even more so if you are not their user.
Use trusted antivirus software to regularly scan and remove viruses from your device instead of believing that a random pop-up magically detected a virus (or 50) on it.
Learn more on how to protect your computer effectively.
How to Remove Scareware?
If you skipped all of the above and still downloaded the scareware, don’t worry, you can remove it.
First of all, how can you tell if you have scareware on your computer?
- Your device starts to run much slower than normal
- Unwanted pop-ups and ads start appearing on your screen
- You can’t install a legitimate security software
Having a legitimate third-party antivirus tool is crucial to remove scareware from your device. Indeed, it can detect and clean up the infection that the scareware caused in the first place.
Once your device is free of actual viruses and malware (and not the fake ones that the scareware told you about), you can eradicate the offending program from your device.
On Windows PC:
- Open the Control Panel.
- Select Programs.
- Find the scareware application and right-click on it. Common ones include PC Clean Pro. Sometimes they’ll even use knock-off names of legitimate tools like MS Antivirus (copies the name of Microsoft Antivirus).
- Select Uninstall.
On Mac:
- Go to the Finder window.
- Open Applications.
- Find the scareware program and either right-click on the icon and select Move to Bin or drag and drop the icon to the bin.
- Right-click on the bin icon and select Empty Bin.
Final Thoughts
Like many other social engineering attacks, scareware is also trying to manipulate you into making a panicked and urgent action. We’ve gathered the most efficient tips to avoid social engineering. Educating yourself is the key to recognize those techniques. That’s why we’ve created a security and privacy awareness course.
Always trust only legitimate security programs and companies, like Mailfence, which supports end-to-end encryption and 2FA. Know how to protect your computer and protect your data from hackers. As emails are the perfect gateway for hackers, registering with a secure and private email provider is the first step to regain the security and privacy you deserve.
If you want to learn more about scareware and cyberattacks, make sure to check the following reports and studies: