New vulnerabilities in many OpenPGP and S/MIME enabled email clients were announced on 2019-04-30. These signature spoofing vulnerabilities exploit weaknesses in the way OpenPGP signatures are verified by email clients and how the verification result is presented to the user. As per our analysis, Mailfence is not impacted by the disclosed OpenPGP signature spoofing vulnerabilities.
Why Mailfence is not impacted by OpenPGP signature spoofing

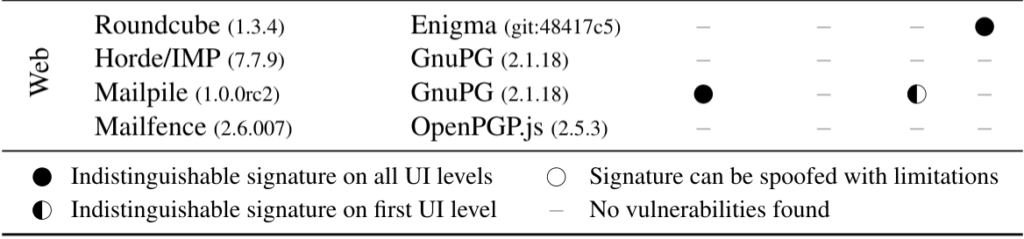
The attacker’s model mentioned in the technical paper is as follows:
- Email ‘From:’ header is spoofed by the attacker using known impersonation techniques.
- Attacker has obtained at least one valid OpenPGP signature by spoofing previous email conversation of the user.
- The victim on the reception side already holds a trusted public key of the spoofed sender.
Here are the attacks demonstrated by the security researchers:
CMS attacks
Mailfence does not treat container format used by S/MIME i.e.., Cryptographic Message Syntax (CMS) and is therefore not impacted by this type of attack.
GPG API specific issue
Mailfence does not use GPG engine and as such is not impacted by GnuPG API specific issues.
MIME attacks
Mailfence signature verification methodology does not regard partially signed and/or embedded signed sub-parts within a multipart message as valid. In most cases, such messages will be regarded as invalid. Moreover, any active content (specific HTML elements and remote content) is always disabled by default. This means, as you opens a signed message, only the valid (correctly recognized) signature verification is performed.
ID attacks
Mailfence does not attempt to bind signature identity with sender address, and only shows the signature verification result. When in doubt, users can always check the the identity of signer by clicking on the signature verification message and match it with the sender address. Concerning displaying the FROM field, Mailfence correctly handles any special characters that might try to manipulate its UI presentation to the user.
UI Attacks
Since Mailfence blocks all active content (specific HTML elements and remote content) by default, any attempt to mimick the signature verification result using e.g., HTML, CSS, or inline images, will not succeed. In such cases, only the valid (i.e., correctly recognized) signature verification message will be displayed.
Recommendations for users using email clients affected by signature spoofing
We would recommend you to take the following mitigation steps, if you are using your Mailfence account with any of the mentioned affected email clients in order to protect yourself against signature spoofing.
- Update your OpenPGP enabled email client and/or plugin
Researchers have reported the findings and suggested improvements to the developers of the affected clients in a process they call coordinated disclosure. This is to ensure that all of the affected clients get fixed before disclosing the issue to the public. - Disable HTML rendering and Remote Content Loading
Prevent your email client from rendering HTML and loading active content. This will make any attempt of spoofing signature verification messages unsuccessful. Please refer to the specific documentation of your email client in this regard. E.g. Thunderbird:
1. On the top-right corner, click on the Menu button.
2. Click on View.
3. Under Message Body As, select Plain Text.
Disable external content:
1. On the top-right corner, click on the Menu button.
2. Click on Options.
2. Under Privacy, select Plain Text.
3. In the Mail content section, uncheck Allow remote content in messages.
- Following good practices and staying cautious is always recommended. With regards to signature verification results, checking the details of the displayed message (to look for any abnormality) is always a good idea.
As one of the most secure and private email suites, we take the security and privacy of user data very seriously and strive to improve our service in every possible way. Contact us in case you have suggestions or queries about OpenPGP signature spoofing.
Learn more about Mailfence on our press page.
Follow us on twitter/reddit and keep yourself posted at all times.
![Email_headers[1] illustration about signature spoofing](https://blog.mailfence.com/wp-content/uploads/elementor/thumbs/Email_headers1-qp612igqvytauigbzhw2dfksp8mcpa2cw29x5ksmfc.png)