L’importance de la sécurité du courrier électronique n’est plus à démontrer. C’est la raison pour laquelle l’Europe a établi des lois sur la confidentialité et la sécurité des données, qui ont abouti au fameux RGPD.
Une étude de 2024 a montré que 94% des organisations interrogées ont été victimes d’une attaque de phishing au cours des 12 derniers mois !
Plus choquant, les attaques de ransomware ont augmenté de 84 % en 2023, avec un montant moyen de rançon de 400 000 USD et des coûts de récupération de 1,8 million USD.
Cependant, comme nous le verrons dans ce guide, la sécurité du courrier électronique n’est pas seulement l’affaire des entreprises. En tant qu’individu, il y a de nombreuses raisons pour lesquelles vous devriez prendre au sérieux la sécurité de vos courriels. Sans plus attendre, plongeons dans le vif du sujet.
Mailfence - Obtenez votre email gratuit et sécurisé.

4.1 sur base de 177 avis utilisateurs
Mailfence - Obtenez votre email gratuit et sécurisé.

4.1 sur base de 177 avis utilisateurs
Qu’est-ce que la Sécurité du Courrier Électronique ?
Rentrons dans le vif du sujet.
La sécurité du courrier électronique consiste à protéger les comptes de courrier électronique et leur contenu contre les accès non autorisés, les fuites ou les compromissions.
La sécurité du courrier électronique peut donc comprendre les éléments suivants :
- des outils tels que des logiciels antivirus, des méthodes de cryptage, etc ;
- des politiques spécifiques et des bonnes pratiques à suivre.
L’objectif ultime de la sécurité du courrier électronique est de garantir (dans la mesure du possible) qu’un compte de courrier électronique et son contenu ne tombent pas entre de mauvaises mains. Pour une entreprise, cela peut s’agir de protéger des secrets commerciaux, des données de l’entreprise telles que les chiffres de vente ainsi que des données internes telles que la rémunération des employés.

Cependant, la sécurité du courrier électronique ne se limite pas aux entreprises. Sur le plan personnel, il y a deux raisons principales pour lesquelles vous devriez protéger vos courriels des regards indiscrets:
- Informations personnelles: votre compte de courrier électronique contient une multitude d’informations privées que vous souhaitez garder confidentielles, telles que votre adresse et votre numéro de téléphone, vos rendez-vous médicaux, vos achats et abonnements en ligne, vos projets de voyage, etc. Entre de mauvaises mains, ces points de données peuvent devenir un outil de rançonnement.
- La publicité. Plus les entreprises en savent sur vous, mieux elles peuvent vous vendre des produits et des services dont vous ne voulez pas ou dont vous n’avez pas besoin. La sécurité des courriels vous protège donc contre la publicité non désirée.
L’évolution de la Sécurité du Courrier Électronique
Pour envoyer des courriers électroniques, un protocole commun a été adopté dans les années 1980, appelé Simple Mail Transfer Protocol (SMTP).
À l’époque, l’Internet n’était utilisé que par un petit nombre d’institutions. La sécurité n’était donc pas une priorité. Le protocole n’a pas été conçu pour protéger le contenu d’un courrier électronique ou pour vérifier l’identité de l’expéditeur.
Avec l’augmentation de l’utilisation du courrier électronique et l’expansion de l’internet, le manque de sécurité du protocole SMTP est devenu un problème important. Dans les années 1990, le spam et la fraude par courrier électronique étaient monnaie courante. La nécessité d’améliorer les protocoles de sécurité pour protéger les communications par courrier électronique s’est clairement imposée.
SSL et TLS
Au milieu des années 1990, deux nouveaux protocoles ont été développés pour améliorer la sécurité des communications sur Internet :
- Secure Sockets Layer (SSL) : ce protocole permet de crypter les données, ce qui rend difficile la lecture du contenu des courriels par des personnes non autorisées.
- Transport Layer Security (TLS) : ce protocole a supplanté le protocole SSL en offrant une meilleure sécurité et est devenu la norme pour le chiffrement des courriels en transit.
Lorsque vous voyez « https:// » dans votre navigateur, cela signifie que SSL/TLS est utilisé pour sécuriser la connexion.
SPF, DKIM et DMARC
Si la protection du courrier électronique en transit est importante, un autre aspect essentiel de la sécurité du courrier électronique n’avait pas encore été examiné.
Lorsque quelqu’un vous envoie un courrier électronique à partir d’une adresse donnée, comment savoir s’il est bien celui qu’il prétend être ?
Si vous recevez un courriel provenant de l’adresse électronique de votre frère, comment pouvez-vous affirmer avec certitude que c’est votre frère qui a envoyé ce courriel ? C’est ce qu’on appelle l’usurpation d’adresse électronique et cela peut constituer une attaque d’ingénierie sociale très grave. À cette fin, des protocoles ont été mis au point pour vérifier l’identité des expéditeurs de courrier électronique. Voici les trois principales en vigueur aujourd’hui :
- SPF: Sender Policy Framework vérifie qu’un courriel est envoyé par un serveur autorisé. Lorsqu’un courriel est reçu, le serveur de réception vérifie l’enregistrement SPF du domaine de l’expéditeur pour s’assurer que le courriel provient d’une source autorisée.
- DKIM: DomainKeys Identified Mail ajoute une signature numérique aux courriels, qui peut être vérifiée par le serveur de réception pour s’assurer que le courriel n’a pas été altéré pendant le transit. Cette signature est propre au domaine de l’expéditeur, ce qui constitue une garantie supplémentaire d’authenticité.
- DMARC: Domain-based Message Authentication, Reporting & Conformance (authentification des messages, rapports et conformité basés sur le domaine) s’appuie sur SPF et DKIM, permettant aux propriétaires de domaines de spécifier comment les courriels qui échouent aux contrôles SPF ou DKIM doivent être traités. Cela permet de se protéger contre les attaques par hameçonnage en fournissant un mécanisme permettant aux destinataires d’emails de rejeter ou de mettre en quarantaine les emails suspects.

Au-delà du SMTP : SMTP STS
Dans l’évolution de la sécurité du courrier électronique, SMTP MTA Strict Transport Security (SMTP STS) a été introduit pour remédier aux vulnérabilités de la transmission du courrier électronique. SMTP STS garantit que les courriers électroniques sont envoyés via des connexions sécurisées et chiffrées, et que ces politiques de sécurité sont rigoureusement appliquées.
SMTP STS permet aux fournisseurs de services de messagerie de publier une politique qui spécifie comment les courriels doivent être transmis en toute sécurité. Lorsqu’un courriel est envoyé, le serveur d’envoi récupère la politique SMTP STS du domaine du destinataire pour s’assurer que la connexion est sécurisée. Si la connexion ne répond pas aux exigences de la politique, le courrier électronique n’est pas envoyé, ce qui constitue une protection solide contre les attaques de type « man-in-the-middle ».
Toutefois, le SMTP STS n’est pas la panacée en matière de sécurité du courrier électronique. En particulier :
- les courriels resteront en texte clair, depuis l’appareil de l’expéditeur jusqu’à ce qu’ils atteignent le serveur SMTP de l’expéditeur concerné (en supposant qu’il n’y ait pas de SSL/TLS en place).
- les courriels resteront en texte clair, du serveur SMTP du destinataire jusqu’à ce qu’ils atteignent l’appareil du destinataire (en supposant qu’il n’y ait pas de SSL/TLS en place).
- le serveur SMTP (tant du côté de l’expéditeur que du côté du destinataire) pourra voir le message en clair.
C’est dans ces lacunes que des hackers pourront exploiter avec succès la confidentialité et l’intégrité des courriels. C’est pourquoi le chiffrement de bout en bout (E2EE) reste la solution idéale (nous y reviendrons plus loin dans ce guide).
Courrier Électronique Sécurisé et Courrier Électronique Ordinaire : Quelle Différence ?
Lorsqu’un courriel est envoyé, il transite par plusieurs serveurs avant d’atteindre le destinataire. Pendant ce transit, toute personne qui intercepte l’email peut en lire le contenu.
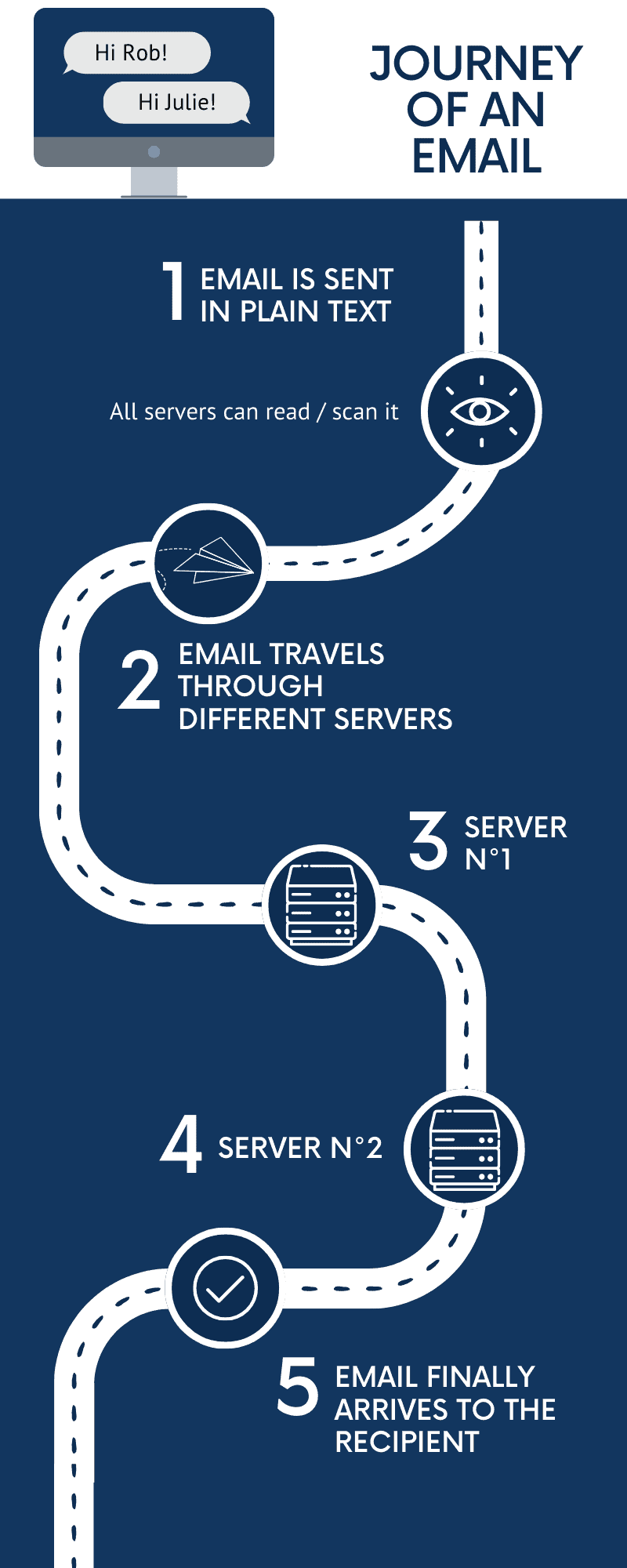
La plupart des services de messagerie électronique tels que Gmail, Yahoo et Outlook, donnent la priorité à l’expérience utilisateur. Les fonctionnalités telles que l’intégration de calendriers, les réponses intelligentes et les modèles basés sur la publicité sont courantes.
Cependant, cela s’accompagne souvent d’un coût pour la sécurité :
- l’exploitation des données: de nombreux services de messagerie électronique gratuits analysent les courriels des utilisateurs afin d’afficher des publicités ciblées. Cela signifie qu’ils lisent, traitent et utilisent vos données afin d’utiliser plus efficacement le marketing personnalisé.
- stockage sur serveurs: les serveurs stockent généralement les courriers électroniques ordinaires en texte clair. Si un intrus compromet un serveur, il peut accéder directement au contenu de votre courrier électronique.
Même si les entreprises affirment qu’elles ne revendent pas vos informations, comment pouvez-vous en être sûr ?
Comme le dit le proverbe : ne faites pas confiance, vérifiez.
Les services de messagerie électronique sécurisée adoptent une approche différente. Ils mettent l’accent sur la sécurité et la protection de la vie privée des utilisateurs. Voici les caractéristiques les plus marquantes :
- Chiffrement de bout en bout (E2EE): Avec E2EE, votre e-mail est chiffré sur votre appareil et n’est déchiffré que sur l’appareil du destinataire. Cela signifie que même si quelqu’un intercepte le courrier électronique pendant son acheminement, il ne peut pas en déchiffrer le contenu sans la clé de déchiffrement.
- OpenPGP (Pretty Good Privacy): Programme de cryptage et de décryptage de données qui assure la confidentialité et l’authentification cryptographiques. De nombreux services de messagerie électronique sécurisée utilisent OpenPGP pour garantir que les courriels sont privés et qu’ils proviennent bien de l’expéditeur indiqué.
- Architecture à connaissance nulle : Certains fournisseurs de courrier électronique sécurisé fonctionnent selon le principe de la connaissance zéro. Cela signifie qu’ils n’ont pas accès aux clés de chiffrement des utilisateurs, ce qui garantit que même le fournisseur de services ne peut pas lire vos courriels.
- Pas d’exploitation des données : Les services de messagerie électronique sécurisée s’abstiennent généralement d’analyser les courriels des utilisateurs à des fins publicitaires. Ils privilégient la confiance des utilisateurs et la protection des données.
En outre, les services de courrier électronique sécurisé fournissent des outils supplémentaires tels que le cryptage symétrique, les signatures numériques, etc. Consultez les liens suivants pour découvrir comment Mailfence offre un service de courrier électronique privé et sécurisé.
9 Conseils pour Sécuriser votre Compte de Messagerie
Le choix d’un fournisseur de messagerie sécurisée tel que Mailfence n’est qu’une première étape. La protection de la vie privée et la sécurité sont un engagement quotidien.
Pour garantir une sécurité maximale de votre courrier électronique, suivez les 11 conseils ci-dessous.
#1 : Mot de passe fort et unique
Notre premier conseil est aussi le plus important. Et cela s’applique à tous les comptes que vous détenez, pas seulement à votre courrier électronique.
Les cybercriminels n’ont pas besoin d’outils élaborés pour pirater votre compte de messagerie, surtout quand on sait que le mot de passe le plus courant en 2024 est 123456. Pour créer des mots de passe forts, vous devez suivre deux grandes lignes directrices :
- n’utilisez pas d’informations permettant de vous identifier, telles que votre nom ou votre date de naissance ;
- utilisez au moins 12 ou 14 caractères. Au plus long, au mieux.
Si vous utilisez un gestionnaire de mots de passe, ce-dernier dispose généralement d’un outil intégré qui peut générer des mots de passe pour vous. Sinon, utilisez des outils pour générer des mots de passe forts si vous n’arrivez pas à en trouver un bon vous-même. N’oubliez pas que c’est la longueur du mot de passe qui doit vous préoccuper le plus.
En cas d’adresses électroniques multiples, veillez à avoir un mot de passe spécifique pour chacune d’entre elles. Par conséquent, si un pirate informatique obtient votre mot de passe, un seul compte sera compromis.
#2 : Ne partagez pas vos mots de passe
Ne communiquez jamais vos mots de passe, ni oralement, ni par écrit. Plus important encore, n’oubliez pas qu’il ne vous sera jamais demandé de partager un mot de passe par courrier électronique. Si quelqu’un prétend en avoir besoin, il peut s’agir d’une escroquerie (voir le point 8 pour plus d’informations).
#3 : Utilisez l’authentification à deux facteurs (2FA)
En utilisant l’authentification à deux facteurs, vous ajoutez une couche de sécurité supplémentaire pour protéger votre compte de messagerie.
Le 2FA fonctionne en 2 étapes. Tout d’abord, vous vous connectez à votre compte de messagerie en utilisant votre nom d’utilisateur et votre mot de passe. Ensuite, en utilisant une application spécifique, un autre code de sécurité sera généré pour permettre l’accès au compte.
Avec le 2FA, même si votre mot de passe est compromis, un pirate a toujours besoin d’un deuxième code pour accéder à votre compte.
En d’autres termes, il sera impossible à quiconque de s’authentifier sur votre compte de messagerie sans le code, même s’il parvient à déchiffrer le mot de passe de votre compte.
Consultez ce guide pour configurer 2FA sur votre compte Mailfence. Vous pouvez utiliser l’application TOTP de votre choix.
#4 : Utiliser le chiffrement de bout en bout (E2EE)
Le chiffrement de bout en bout ajoute une couche de protection supplémentaire.
Lorsque vous envoyez un courrier électronique, vous pouvez choisir de chiffrer les données afin de protéger votre communication. Pour décrypter le contenu de votre courriel, le destinataire aura besoin d’une clé spécifique (ou d’un mot de passe partagé). Ainsi, seul le destinataire prévu pourra le décrypter.
L’E2EE peut être un peu intimidant lorsque vous commencez à vous familiariser avec ce domaine.
C’est pourquoi nous avons élaboré un guide pour les débutants, que vous pouvez consulter ici.
En principe, les utilisateurs disposent de deux clés : une clé publique et une clé privée. L’expéditeur chiffre le message avec la clé publique du destinataire. Seul le destinataire, avec sa clé privée, peut décrypter le message.
Tout comme les mots de passe, vous ne devez jamais partager votre clé privée. Comme son nom l’indique, cette clé est et doit rester privée.
#5 : Ne cliquez pas sur un lien dans un e-mail sans vous informer
Certains pirates informatiques disposent de moyens très sophistiqués pour vous faire croire qu’un lien est sûr alors qu’il ne l’est pas.
Comme un lien peut ne pas être ce qu’il semble être, ne cliquez jamais sur un lien dans un courriel avant d’avoir fait des recherches.
Tout d’abord, en plaçant votre souris sur le lien sans cliquer, vous pourrez voir l’URL du lien. Vérifiez donc s’il correspond au lien tapé dans le message.
Les pirates peuvent se faire passer pour quelqu’un qu’ils ne sont pas et demander des informations sensibles. Même si ce qui semble être votre banque vous demande des données personnelles, il n’y a aucune raison qu’elle vous les demande par courrier électronique. Ce type de demande devrait constituer un avertissement. Pour en savoir plus sur ces types d’attaques d’ingénierie sociale, cliquez ici.
#6 : Évitez de connecter des applications à votre compte de messagerie
Donner à une application tierce l’accès à votre boîte de réception présente un risque car l’application peut être compromise. Un cybercriminel pourrait accéder à votre boîte de réception via l’application. Tout le contenu de votre boîte de réception sera alors accessible.
#7 : N’accédez jamais à vos courriels lorsque vous utilisez un réseau Wi-Fi public
Un autre moyen de protéger votre compte de messagerie est d’éviter les réseaux Wi-Fi publics. Ils peuvent être compromis. Bien que nous utilisions SSL/TLS pour nous protéger contre les attaques MITM, il est toujours préférable d’éviter de se connecter à des réseaux non fiables. Dans la mesure du possible, utilisez les données mobiles, même si cela implique une connexion plus lente.
#8 : Restez au courant des nouvelles techniques des pirates informatiques
Les cybercriminels disposent de techniques avancées pour vous inciter à faire confiance à un courriel que vous ne devriez pas recevoir. Phishing, spear phishing, … Ces techniques au nom amusant peuvent en fait être particulièrement dangereuses si vous n’y prêtez pas suffisamment attention.
L’essentiel est de vous informer. Tenez-vous au courant des nouvelles formes d’attaques en lisant l’actualité.
Avec l’avènement de l’IA, de nouvelles formes de cybermenaces apparaissent constamment. Les attaquants peuvent désormais facilement copier le style d’écriture et le ton d’une personne que vous connaissez, voire sa voix. C’est pourquoi il est essentiel de rester informé.
#9 : Déconnectez-vous toujours
Après une longue journée de travail, déconnectez-vous de tous vos comptes. C’est particulièrement important lorsque vous utilisez un appareil public, car n’importe qui peut accéder à vos informations privées une fois que vous avez terminé.
Néanmoins, la déconnexion est une habitude de principe à conserver, même à partir d’un appareil personnel.
En effet, la déconnexion est le moyen le plus sûr d’obliger toute personne essayant d’accéder à votre compte de messagerie à se connecter. Ainsi, en cas de vol de votre téléphone ou de votre ordinateur, votre compte de messagerie sera toujours protégé par votre mot de passe fort et unique et par le 2FA.
Pour vous faciliter la vie, il existe de nombreux plugins que vous pouvez installer et qui vous déconnectent automatiquement lorsque vous fermez votre navigateur.
Sécurité du Courrier Électronique: Conclusion
Il existe de nombreux fournisseurs de services de messagerie électronique qui prétendent être « privés et sécurisés ». Même Gmail a récemment changé son slogan pour devenir « Private and secure email at no cost » (courrier électronique privé et sécurisé sans frais) !
Mailfence est un service de courrier électronique sécurisé et privé qui offre un chiffrement de bout en bout du courrier électronique à l’aide d’OpenPGP et de fonctions de signature numérique.
Toutes les opérations relatives à vos clés privées et au corps des messages électroniques sont effectuées après que l’utilisateur a déverrouillé la clé privée à l’aide de la phrase d’authentification qu’il est le seul à connaître.
Pour une analyse détaillée du niveau de protection offert par Mailfence, vous pouvez consulter cet article de la base de connaissances.
Aucun fournisseur de messagerie électronique ne peut prétendre être sûr à 100 % – et il y aura toujours des compromis à faire. Nous aimons faire preuve de transparence afin que vous puissiez prendre une décision en toute connaissance de cause. Si vous avez des questions, n’hésitez pas à nous contacter à l’adresse suivante : support@mailfence.com
Pour en savoir plus :
Chiffrement de bout en bout. Qu’est-ce que c’est et comment cela fonctionne-t-il ?
Chiffrement symétrique : Le moyen le plus simple de crypter un courriel
Mesures à prendre en cas de piratage de votre courrier électronique