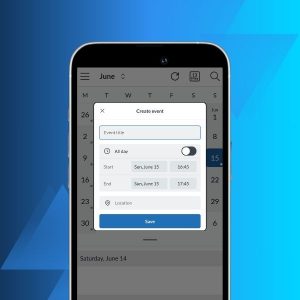
Introducing our Calendar to the Mailfence Mobile App!
We are very happy to announce that “Mailfence Calendar”, is now available inside the Mailfence mobile app! Alongside many other new features and improvements, this

We are very happy to announce that “Mailfence Calendar”, is now available inside the Mailfence mobile app! Alongside many other new features and improvements, this

Whether you’re sharing sensitive documents or archiving personal files, knowing how to encrypt a ZIP file can protect your data from prying eyes. In this

Google Drive is great for storing and sharing files, but can you password-protect a Google Drive folder in 2025? The short answer is: not directly.

Email remains one of the most widely used professional and personal communication tools. Yet, as inboxes grow and conversations evolve, the term “email trail” becomes
Concerns about data collection, surveillance, and lack of transparency have triggered a growing backlash against Big Tech. Companies like Google, Amazon, Meta, and Microsoft dominate

The dark web remains one of the most misunderstood parts of the internet. Often associated with cybercrime and secrecy, it also serves as a critical
Every search you make, every profile you create, and every “I agree” you click contributes to your digital footprint. So, in this guide, we’ll walk

With 2 billion monthly active users as of February 2025, WhatsApp remains the king of messaging apps. However, if you’re like me, you might be

Ransomware attacks can lock you out of your own computer in seconds. What’s worse is that even if you pay the ransom, there’s no guarantee