
OpenPGP Email Summit hosted by Mailfence- October 20-21, 2018
Mailfence will be hosting the 4th OpenPGP Email Summit We are very happy and honoured to announce that Mailfence will be hosting the 4th OpenPGP

Mailfence will be hosting the 4th OpenPGP Email Summit We are very happy and honoured to announce that Mailfence will be hosting the 4th OpenPGP

New vulnerabilities in many OpenPGP and S/MIME enabled email clients were announced yesterday. These “Efail” vulnerabilities have attracted a lot of attention in the media.

Online privacy threats have become much more diverse and sophisticated than they were 10 or even 5 years ago and cybercriminals are getting more and

Due to the open and decentralized nature of SMTP, email spoofing is a common issue. Every mail server connected to the internet can attempt to
Mailfence is an end-to-end encrypted email solution with digital signatures that gives users full freedom and control over their key management. However, how to encrypt

From SMTP to OpenPGP, S/MIME and Secure Message Escrow Emails have been the epicenter of online communication for decades now. Unfortunately the underlying protocol called

Internet conglomerate and popular email host Yahoo was hacked twice earlier this year, revealing personal, sensitive data of 1.5 billion account holders. Countless other wide-scale
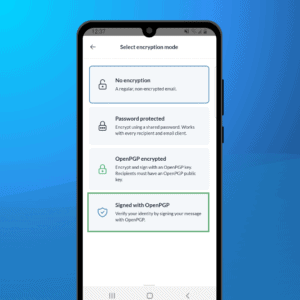
Mailfence secure and private email service comes with an easy to use integrated keystore that supports wide range of functionalities for managing OpenPGP keys. In

Mailfence built a private and secure email solution that is fully interoperable with any other PGP based service in the world. In this blogpost, we