Email spoofing is a cyberattack in which a malicious actor impersonates a legitimate sender. They hide their identity by sending an email from a fake email address. They trick you into believing the email address is genuine. How does it work, and how to spot and prevent email spoofing? Let’s have a look.
What is Email Spoofing?
Email spoofing is a very popular cyberattack tactic that is often used in phishing campaigns and many other social engineering schemes.
The idea is very simple. You are much more likely to open and respond to an email if you think it came from a legitimate and known sender. Therefore, the point is to send a fraudulent email from a seemingly genuine sending address.
It can be a colleague, family member, boss, service, or brand you are using, etc. Basically, anyone you might trust and whose email you’re likely to open and reply to without double-checking.
How does Email Spoofing Work?
Email spoofing is notoriously easy to do as it only requires a common email platform like Gmail or Outlook and an SMTP (Simple Mail Transfer Protocol) server.
The reason why it works is that SMTP has no way to authenticate the sender’s email address, which allows the hacker to forge the email header, specifically the FROM, REPLY-TO and RETURN-PATH fields.
There are three ways that an email can be spoofed:
Via the Display Name
This type of email spoofing is the most common and easiest to do. In it, the hacker first opens a new email account (usually Gmail) with the same name as the person or brand that they want to impersonate.
For instance, you might get an email from Elon Musk that looks like this:
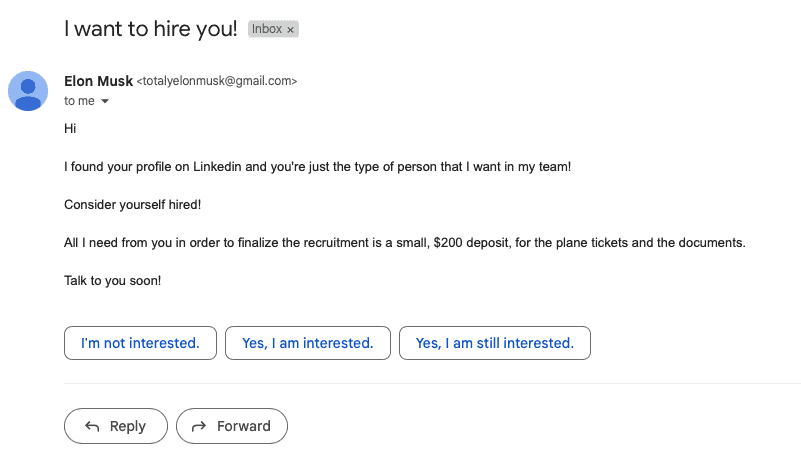
Obviously, if you think that Elon Musk has no better recruitment process than randomly emailing strangers, then you’re extremely naive. But this tactic still works for a number of reasons.
Namely:
- It comes from a legitimate email address. This is just a Gmail account I created in less than a minute and used to send an email as “Elon Musk” to another of my accounts to show how easy it is. As a result, the email didn’t go to the spam folder, but straight to the inbox.
- It exploits the email user interface. Since the user interface will only show the display name and not the actual sender’s email address or metadata, along with the subject line and part of the message, anyone can impersonate someone like Elon Musk this way.
Via Lookalike Domains
Of course, anyone can create a Gmail account, but most businesses use a custom email domain.
For example, let’s say a business uses the domain @business.co.
All an attacker has to do is create a similar domain, like @bvsness.co and by changing just one character, make their email look like it comes from a legitimate brand to an untrained or inattentive eye.
Very often, this type of spoofing is used to trick users into revealing their passwords or to transfer money to the attacker by impersonating a legitimate company.
Via Legitimate Domains
Still, you can easily spot email spoofing via lookalike domains if you just pay a little attention to the domain itself.
However, hackers can also use legitimate domain names to make their emails even more believable.
Again, this is because SMTP has no way to authenticate the sender. The hacker can manually specify the FROM field to look like it comes from someone working in a specific company, whereas they don’t.
Why Would Someone Spoof Emails?
The obvious answer to “why would someone spoof emails?” is because they want to hide their true identity and impersonate someone else, all in order to facilitate illegal or malicious gain.
They have various reasons for doing so:
- Hiding the sender’s real identity
- Impersonating that they are someone the recipient knows
- Pretending that they are a company whose services or products the recipient is using
- Damaging someone else’s reputation
- Avoiding spam filters
Commonly, email spoofing is used in various types of phishing or spam attacks, such as:
- Spear phishing – a type of phishing attack in which the criminal impersonates someone known to the recipient
- BEC (Business Email Compromise) – a phishing attack that uses a hacked, spoofed, or otherwise impersonated business email address
- VEC (Vendor Email Compromise) – a type of BEC attack in which the attacker pretends to be from a business in the company’s supply chain, like a vendor, for instance
- CEO Fraud – another type of BEC attack, in which the attacker impersonates a high-ranking executive in the company (usually C-level)
How to Prevent Email Spoofing?
The good news is that, as easy as email spoofing is to do, it’s also easy to spot and prevent.
Here’s how:
1. Watch out for Red Flags
A spoofed email will have a similar, but still incorrect sender email address, links that point everywhere but the official website, unwanted attachments, grammar errors, unfamiliar file types, use threats to pressure you to respond quickly (give your account info or send money), or be too good to be true (like getting a job from Elon Musk). Basically, errors you can spot in most social engineering attacks.
2. Don’t Click on Weird Links or Unwanted Attachments
Stay away from any weird links or email attachments you didn’t ask for, as these might redirect you to a phishing website or download malware to your computer.
3. Just don’t Respond
Phishing and spoofing emails only work if you respond to them and divulge your personal information. By simply not responding to them, they have zero effect.
4. Inspect the Email Header
To inspect the email header, simply open the email message, right-click and select “View Source”.
Specifically, look at the RECEIVED section and if the domain differs from that in the FROM address, that email is most likely forged.
5. Use Email Security Protocols
While SMTP can’t authenticate the sender’s address, three other frameworks can: SPF, DKIM, and DMARC. These three are a must in your email spoofing defence.
So what does each of them do?
SPF (Sender Policy Framework) – checks if the IP (Internet Protocol) address is authorized to send emails to the recipient’s domain.
DKIM (Domain Keys Identified Mail) – authenticates that the email is sent by an authorized server and not changed in transit.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) – DMARC tells the recipient’s server what should happen with failed checks and sends feedback and reports about it.
6. Digitally Sign Your Emails
Finally, the ultimate protection against email spoofing is to digitally sign your emails.
This provides the following security aspects:
- Authenticating and verifying the sender (proves the sender is who they claim to be)
- Integrity check (proves that the message was not changed in transit)
- Non-repudiation (the sender can’t deny they sent the message)
Conclusion
A good email defence, is to stay alert and avoid common email mistakes. Also, our Email security and privacy course can significantly improve your email awareness, so be sure to go through it as well. Feel free to spread the word! If you want to go even further, securing your email account is the most effective way to secure all your accounts. Why not try our collaborative suite today? We support end-to-end encryption and digital signatures. Wait no more!