
Email security and privacy awareness course
Achieving online privacy and security is not an easy feat, so that’s why we created this email security and privacy course to enrich the learning

Achieving online privacy and security is not an easy feat, so that’s why we created this email security and privacy course to enrich the learning

In a recent post, we discussed the OpenPGP encryption best practices. Digital signatures on the other hand are also a vital part of OpenPGP which gets used both
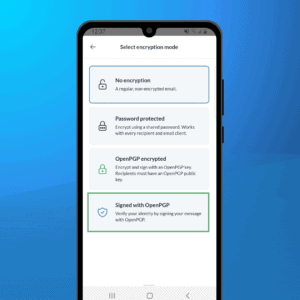
Strong encryption is no longer a privilege of geeks and paranoids but is becoming mainstream. However, true end-to-end encryption is not out-of-the-box and generally requires you

Yahoo recently confirmed a massive breach of over 500 million email accounts, including both credentials and security questions. At Mailfence – a secure and private

Recently a GNU/Linux TCP vulnerability was disclosed (CVE-2016-5696) by security researchers in the US. Upon analysis, this bug did not pose a threat to our users.
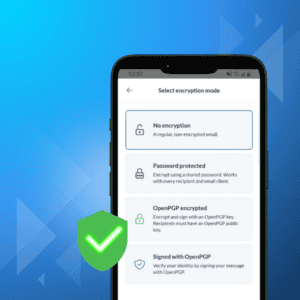
With threats looming constantly in the digital world, using end-to-end encryption and digital signatures has become a necessity to protect your data online. Read this

The underlying 1980s transport protocol used to send emails: Simple Mail Transfer Protocol (SMTP) is ancient and lacks the ability to provide email security. To

When accessing any of the Mailfence services, the transmission of data between your device program and our servers in Brussels-Belgium is always encrypted and protected

Following are several tips on how to avoid social engineering schemes. These steps won’t prevent your account from getting compromised if a service provider falls for