Compromised Passwords? Simple Steps to Protect Your Accounts Today

Compromised passwords are like leaving your front door open, giving unwelcome guests a way into your online life. Even one, single weak password can open doors to your private accounts, exposing personal information to cybercriminals. But safeguarding your information doesn’t require high-level expertise. This guide will explain how passwords fall into the wrong hands, what […]
Want to Create an Email Account Without a Phone Number? Here’s How.

Being able to create an email without a phone number is key to preserving your privacy. However, most email services in 2024 require phone verification to complete your sign-up. That is why we made this guide for you! Together, we are going to explore: So let’s get started! Why Anonymity is Important Let’s get one […]
How to Share a Password Safely and Securely in 2024 (4 Methods)

We’ve all come across a time when we needed to share a password. But more often than not, we don’t really think about how we are sharing it. And if we are doing so securely. If you’re wondering how to share a password safely and securely, then this guide is for you! Together, we’ll look […]
How RISS Uses Mailfence as the Perfect Sharepoint Alternative

In this Customer Success Story, we share the story of RISS, a non-profit organization in the telecommunications sector, who adopted Mailfence as the perfect Sharepoint alternative for document collaboration. In our Customer Success series, we aim to highlight real-life stories of how our customers have tackled challenges and found success with Mailfence. You’ll get a […]
Spam vs Phishing: What’s the Difference?

Spam vs phishing attempts – do you know the difference? Every day, a new data breach or leak is made public. This means that, unfortunately, most of our email addresses are now freely available on the dark net, making them an easy target for spam and phishing attempts. In this guide, we’ll cover everything you […]
Introducing Contacts to the Mailfence Mobile App!
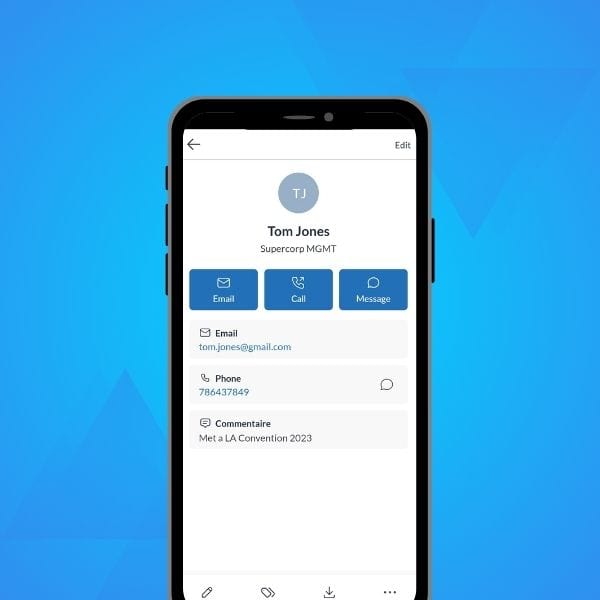
We are thrilled to announce that “Mailfence Contacts”, our contacts management solution, is now available inside the Mailfence mobile app! This new release follows the introduction of Mailfence Documents, our cloud storage solution, to the mobile app last June. If you haven’t yet, make sure to download the latest version from the Google Play Store or the App […]
Email Filtering: 7 Tips When Using Email Filters in 2024

Ah, “inbox zero”—that elusive dream we all chase. It’s almost like reaching the top of Mount Everest, except Everest doesn’t get more emails every 10 minutes. And while actually hitting inbox zero might feel like a fantasy, email filters can get you pretty close. Think of email filtering as your inbox sherpas, helping you clear […]
What Is an Email Alias? 4 Reasons You Should Use One in 2024
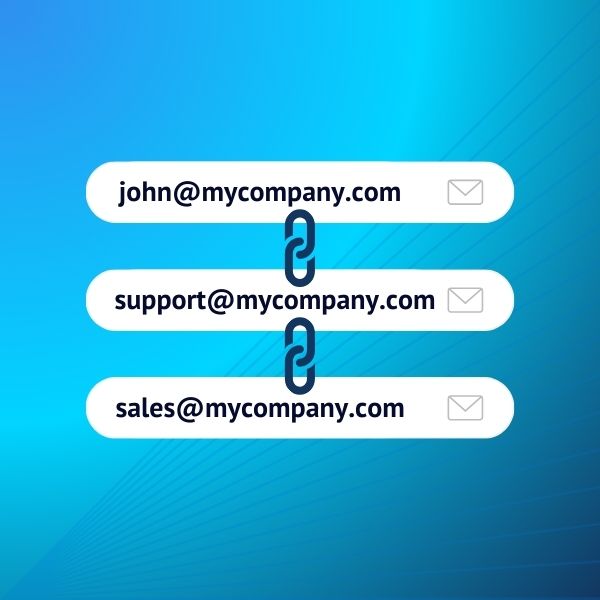
An email alias is one of the best ways to keep your inbox organized, enhance your online privacy, and track spammers. In this guide, we’ll cover everything you need to know about email aliases, the differences with a dedicated mailbox, and how to create your first email aliases. What is an Email Alias? An email […]
How to Whitelist Email Addresses in Gmail, Outlook & more (2024)
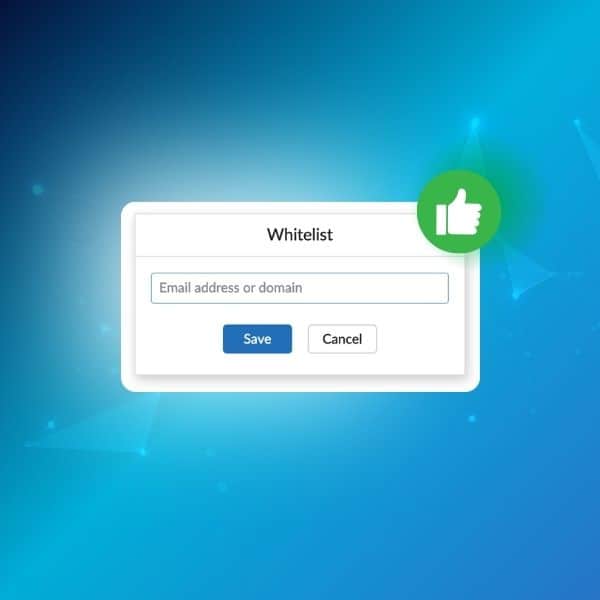
Choosing to whitelist an email address is the best way to make sure you don’t miss vital emails again. Have you ever searched for an important email in your inbox? Only to realize weeks later that it was actually in your spam folder? That’s why whitelisting was created. In this guide, we’ll cover everything you […]
Password Spraying Attacks: How Can You Protect Yourself in 2024?
Password spraying attacks are an increasingly common cybersecurity threat. However, most people are unaware of what they are, and how they work. In this guide, we’ll cover everything you need to know about password spraying. We’ll explain how they work, how to detect if you are being attacked, and how to protect yourself in the […]