Vous avez peut-être déjà rencontré le terme « signatures numériques » en ligne. Il se peut même que vous ayez vous-même signé numériquement des courriels ou des documents. Cependant, une signature numérique n’est pas la même chose qu’une signature électronique.
Alors qu’une signature électronique peut être aussi simple qu’un code PIN, une signature numérique utilise des méthodes cryptographiques pour vérifier l’identité de l’auteur et garantir l’intégrité du document
Dans ce guide, nous aborderons tout ce que vous devez savoir sur les signatures numériques, notamment :
- ce qu’est une signature numérique ;
- ce qui la différencie des signatures électroniques ;
- comment envoyer vos premiers courriels signés numériquement ;
… et bien plus encore !
Mailfence - Obtenez votre email gratuit et sécurisé.

4.1 sur base de 177 avis utilisateurs
Mailfence - Obtenez votre email gratuit et sécurisé.

4.1 sur base de 177 avis utilisateurs
Qu’est-ce qu’une Signature Numérique ?
Tout d’abord, définissons ce qu’est une signature numérique.
Une signature numérique est un type de signature électronique qui utilise des techniques cryptographiques pour vérifier l’identité du signataire et garantir l’intégrité du document.
Dans un sens, une signature numérique est une « empreinte digitale virtuelle ». Une fois appliquée, elle peut être intégrée au document ou exister séparément.
Les signatures numériques jouent trois rôles essentiels :
- vérification de l’expéditeur : l’expéditeur est bien celui qu’il prétend être ;
- intégrité : le message n’a pas été modifié pendant le transit ;
- non-répudiation: l’expéditeur ne peut pas nier avoir envoyé le message, selon le type de signature numérique.
Les signatures numériques sont donc plus sûres que les signatures manuscrites. En effet, il n’existe aucun moyen fiable de vérifier une signature manuscrite, et encore moins de savoir si le document n’a pas été falsifié.
Les signatures manuscrites sont propres à chaque personne (style d’écriture, vitesse d’écriture, etc.). Cependant, une fois qu’une signature est couchée sur le papier, elle est facilement falsifiable à l’aide de papier calque.
Les signatures manuscrites posent donc un problème de répudiation. Une personne peut simplement prétendre que quelqu’un a copié sa signature, et il serait difficile de prouver le contraire.
C’est pourquoi nous avons besoin de signatures numériques.
Signature Numérique et Signature Electronique: Quelle Différence ?
Nous avons mentionné précédemment qu’une signature numérique est un type de signature électronique. Il est important de bien faire la différence entre ces deux notions, car toute signature électronique n’est pas automatiquement une signature numérique.
Une signature électronique peut prendre différentes formes, pas seulement une signature proprement dite. Il peut s’agir d’un code PIN, d’un mot de passe ou même d’une simple image de votre signature :
Voici une comparaison rapide entre les signatures électroniques et les signatures numériques :
| Fonctionnalité | Signature électronique | Signature numérique |
| Objectif | Vérification du document | Protéger le document |
| Vérification | Ne peut être vérifié | Peut être vérifié |
| Règlement sur les tiers | Ils peuvent être soumis à des réglementations différentes selon les juridictions (comme eIDAS dans l’UE ou la loi ESIGN aux États-Unis). | La valeur juridique est déterminée, selon la juridiction, par le niveau d’assurance fourni par les techniques et protocoles cryptographiques utilisés (tels que les signatures électroniques qualifiées dans le cadre de l’eIDAS). |
| Cryptographie | N’utilise pas d’algorithmes cryptographiques | Créé à l’aide d’algorithmes cryptographiques |
| Avantage | Convivialité (mais pas de sécurité des données) | Fournir des fonctions de sécurité des données à l’aide de méthodes cryptographiques |
Comment Fonctionnent les Signatures Numériques ?
Nous avons maintenant établi ce qu’est une signature numérique et pourquoi il s’agit d’une forme supérieure de signature électronique.
Voyons maintenant comment elles fonctionnent.
Tout d’abord, une signature numérique exige seulement que l’expéditeur (le signataire) dispose de clés cryptographiques (une clé privée et une clé publique). L’expéditeur signe le message localement sur son appareil (à l’aide de sa propre clé privée). Le destinataire le vérifie ensuite sur son appareil à l’aide de la clé publique de l’expéditeur. Le processus se déroule comme suit :
- Alice (l’expéditeur) génère une paire de clés et partage sa clé publique avec Bob (une condition préalable unique).
- Alice signe le message à l’aide de sa clé privée sur son appareil et l’envoie à Bob.
- Bob reçoit le message signé sur son appareil et vérifie la signature à l’aide de la clé publique d’Alice.
N’oubliez pas de consulter ce guide sur les clés privées et publiques si vous avez besoin d’une remise à niveau. Il existe également des signatures numériques qui peuvent être générées à l’aide d’algorithmes cryptographiques classés comme symétriques.
Signatures numériques au niveau technique
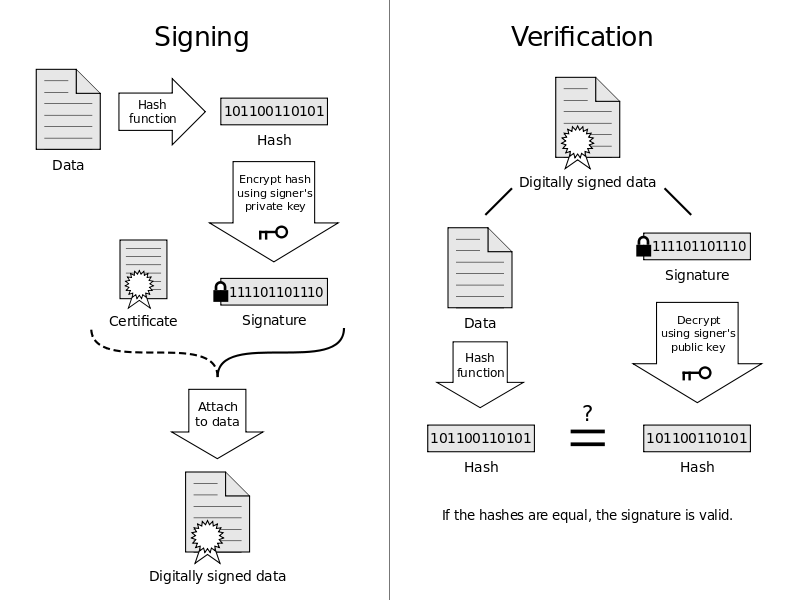
D’un point de vue plus technique, l’envoi d’un courrier électronique signé numériquement suit les étapes suivantes :
- La signature commence par un hachage cryptographique du message original ;
- le hachage est chiffré avec la clé privée de l’expéditeur et envoyé avec le message original ;
- le destinataire reçoit à la fois le message original et son hachage crypté ;
- Le destinataire décrypte ensuite le hachage crypté à l’aide de la clé publique de l’expéditeur et le compare au hachage du message d’origine ;
- si les deux hachages correspondent, la signature numérique est vérifiée.
Pour bien comprendre le fonctionnement des signatures numériques, il faut entrer un peu dans la technique. Plus précisément, nous devons discuter de deux modèles communs différents sur lesquels elles sont basées.
La première est la PKI ou« Public Key Infrastructure » (infrastructure à clé publique). Cela signifie que la clé publique utilisée par Alice pour signer son message à Bob doit être certifiée par une autorité de certification(telle que Verisign).
En d’autres termes, l’autorité de certification se porte garante de la clé, et la clé valide l’expéditeur – ce qui fait de l’autorité de certification une ancre de confiance.
Toutefois, une autorité centralisée (c’est-à-dire une autorité de certification) n’est pas toujours digne de confiance (pour des raisons sociopolitiques, par exemple) ou peut être compromise.
Un autre modèle de confiance est le Web of Trust ou Pretty Good Privacy (PGP).
Dans le modèle du « réseau de confiance », chaque utilisateur dispose d’un ensemble de clés publiques « de confiance » qui vérifient l’identité de l’expéditeur par rapport au destinataire, au lieu que tout le monde se fie à une seule autorité de certification.
Les Signatures Numériques sont-elles Identiques au Chiffrement de Bout en Bout ?
Bien que les concepts soient similaires, ils ne sont pas identiques.
La différence la plus notable est qu’avec le chiffrement de bout en bout, les deux parties ont besoin de leur propre paire de clés privée/publique.
Cependant, vous pouvez envoyer un courriel signé numériquement à quelqu’un qui n’a pas généré de paire de clés.
Voici un bref résumé :
| Cryptage de bout en bout | Signatures numériques |
| Utilisé pour crypter des informations sensibles dans un courriel ou un document. | Utilisé pour vérifier l’authenticité et l’intégrité du document ou du message électronique. |
| La clé publique du destinataire est utilisée pour crypter les données contenues dans le courrier électronique ou le document. | La clé publique de l’expéditeur est utilisée pour vérifier la signature. |
| La clé privée est utilisée par le destinataire pour décrypter les données contenues dans le courrier électronique. | La clé privée est utilisée pour signer le document par l’expéditeur. |
Si vous souhaitez approfondir la question du chiffrement de bout en bout, consultez notre guide complet.
Toutefois, les signatures numériques peuvent être combinées à un chiffrement de bout en bout. Cela permet d’accroître la sécurité, comme nous le verrons dans la section suivante.
Comment Envoyer un Email avec Signature Numérique?
Maintenant que vous savez ce qu’est une signature numérique, comment en envoyer une ? La procédure exacte diffère d’un fournisseur de messagerie à l’autre.
Pour commencer, le plus simple est de créer un compte Mailfence gratuit et de suivre les étapes suivantes.
Tout d’abord, générez votre paire de clés et partagez votre clé publique avec le destinataire. Ensuite, vous pouvez utiliser votre clé publique :
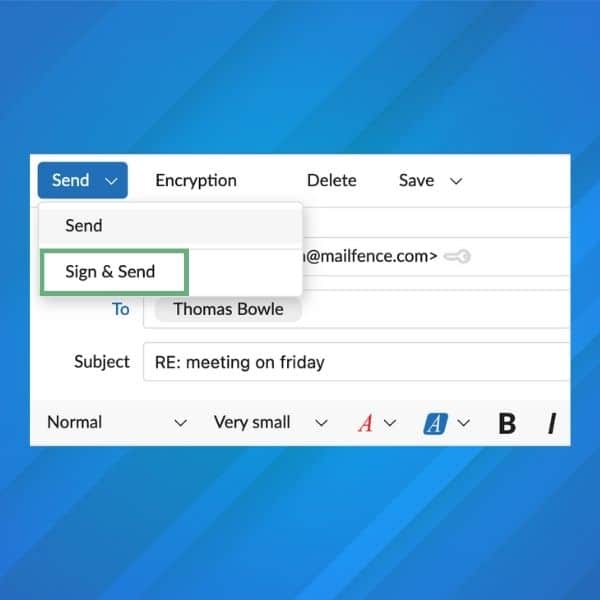
- sur notre interface web, composez votre courriel et saisissez l’adresse électronique du destinataire. Cliquez ensuite sur la flèche déroulante située à côté de « Envoyer » et sélectionnez « Signer et envoyer ». Saisissez votre mot de passe et cliquez sur OK.
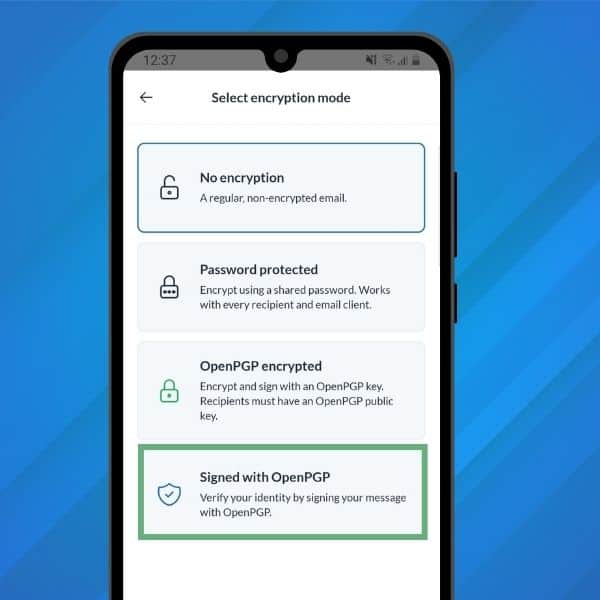
- sur notre application mobile, lorsque vous rédigez un message, appuyez sur l’icône « Verrou » en haut à droite de l’écran. Sélectionnez « Signé avec OpenPGP ».
C’est tout – c’est aussi simple que cela !
D’ailleurs, si vous ne l’avez pas encore fait, n’oubliez pas de télécharger notre application mobile sur l’App Store ou le Google Play store!
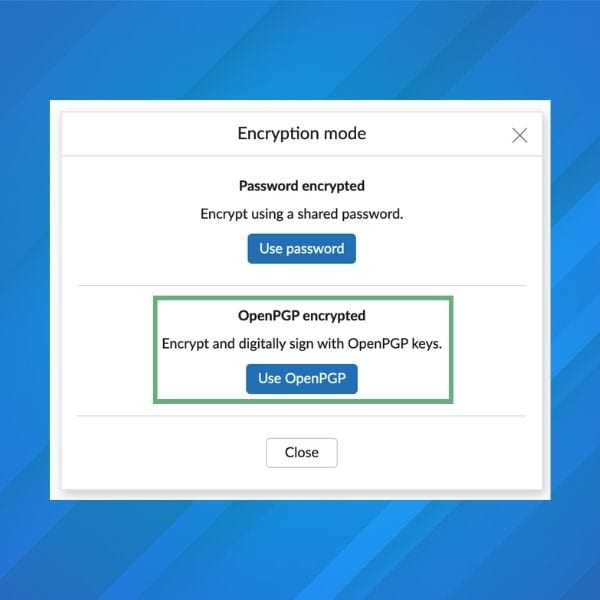
Comme indiqué précédemment, vous pouvez combiner le chiffrement de bout en bout avec des signatures numériques. Cela permet de renforcer la sécurité de vos communications. Avec Mailfence, si vous décidez de chiffrer votre courrier électronique, il sera également signé automatiquement :
Meilleures Pratiques en Matière de Signatures Numériques
Avant de conclure ce guide, passons en revue quelques bonnes pratiques pour l’envoi d’e-mails signés numériquement.
Conseil n° 1 : utilisez des signatures numériques lors de l’envoi de courriels
La signature numérique des courriels et des pièces jointes rassure le destinataire du courriel. En outre, cela garantit que le contenu et la pièce jointe n’ont pas été altérés pendant le transport. La valeur juridique de l’e-mail s’en trouve renforcée.
Conseil n° 2 : utilisez une clé forte pour la signature numérique
Utilisez une clé privée de 4096 bits (ou au moins de 2048 bits) basée sur la longueur pour signer un message numérique. Mailfence génère toujours une clé RSA de 4096 bits par défaut.
Conseil n° 3 : utilisez une sous-clé lors de la signature
Nous avons vu dans ce guide que le chiffrement et la signature sont deux opérations différentes.
Elles nécessitent donc deux approches différentes en matière de gestion des clés. Vous voudrez peut-être qu’une clé de signature soit valide pendant une longue période afin que les gens du monde entier puissent vérifier les signatures du passé. Quant à votre clé de chiffrement, vous voudrez la faire tourner plus tôt et révoquer/expirer facilement l’ancienne.
Par conséquent, une bonne pratique consiste à conserver votre paire de clés à l’extérieur en tant que « paire de clés principale » (par exemple, dans une clé USB) et à utiliser une sous-clé en tant que « clé locale » pour signer les messages.
Cet article fournit une liste d’étapes à suivre pour y parvenir en utilisant GPG. Vous pouvez ensuite importer cette paire de clés locale dans le keystore de votre compte Mailfence pour l’utiliser de manière transparente sur tous vos appareils.
Note : 1) Les paires de clés ne contenant que des sous-clés (pour la signature et le cryptage) et un paquet de clés privées fictives(une extension GNU d’OpenPGP) peuvent ne pas être prises en charge par tous les programmes compatibles avec OpenPGP. 2) Le fait de conserver la clé secrète principale sur un support amovible rend problématique la signature (ou la certification) d’autres clés GPG, car la clé secrète principale doit être chargée pour procéder à la signature. 3) L’utilisation de dates d’expiration pour les sous-clés (recommandée) signifie que les sous-clés doivent être prolongées avant l’expiration ou que de nouvelles sous-clés doivent être émises si elles sont autorisées à expirer. 4) Par ailleurs, les personnes qui utilisent votre clé publique (c’est-à-dire qui vérifient un document que vous avez signé) peuvent recevoir des messages d’erreur indiquant que votre clé a expiré si elles ne mettent pas régulièrement à jour leurs trousseaux de clés GPG auprès des serveurs de clés publiques.
Conseil n° 4 : demandez à vos amis et collègues de signer votre clé publique
L’apposition de signatures de confiance sur votre clé renforcera sa légitimité. Demandez à vos amis/collègues de signer votre clé. Vous devez signer leur clé publique en échange.
Par ailleurs, keybase.io est un modèle opérationnel qui associe votre identité à vos clés publiques, et vice versa.
Conseil n° 5 : signez votre message pour chacun de vos destinataires
Oui, incluez les adresses électroniques de l’expéditeur et du destinataire avec l’horodatage dans votre signature numérique ! (en l’ajoutant au corps du message). Vous pouvez également utiliser un service qui offre une protection suffisante contre les attaques par rejeu (nonce, jetons de session, horodatage, etc.).
Conseil n° 6 : Soyez prudent lorsque vous transférez un message signé numériquement
Prenons le cas d’un message signé numériquement par Alice à Bob et transmis à Carol . Seule l’identité de l’expéditeur original, Alice, est prouvée au destinataire : Alice est prouvée au destinataire. Carole ne peut pas supposer que Bob, qui a transmis le message, est le propriétaire de la signature numérique et/ou l’expéditeur légitime du message. Sauf si le message transmis est signé par Bob lui-même.
Conseil n° 7 : vérifiez à l’avance l’empreinte digitale de la clé de votre expéditeur
Si possible, obtenez à l’avance (de préférence en personne) l’empreinte digitale de la clé de votre expéditeur – ou si votre expéditeur est une personnalité connue, faites une recherche en ligne.
En outre, vérifiez toujours la paire de clés utilisée pour signer un message avec l’empreinte digitale.
La vérification automatique (correspondance entre le hachage décrypté et le hachage du message original) est une chose. Mais elle ne vous protégera pas contre les attaques par usurpation d’identité, où un attaquant peut créer une fausse identité de l’expéditeur et l’utiliser pour tromper les destinataires. Par conséquent, une empreinte digitale devrait toujours être votre seul facteur cryptographique pour vérifier les clés publiques de tous vos expéditeurs.
Conseil n° 8 : assurez-vous que la clé de signature n’a pas été révoquée ou qu’elle n’a pas expiré.
Assurez-vous que la clé utilisée pour signer un message particulier n’est pas révoquée ou expirée ! Il s’agit là d’un point important ! Souvent, les applications ne l’indiquent pas clairement à l’utilisateur. Chez Mailfence, tous les cas de ce type sont affichés à temps et correctement.
Toutefois, si la signature d’un message a eu lieu avant la date d’expiration ou de révocation de la clé de signature, la signature numérique reste valide.
Conseil n° 9 : exporter localement les messages comportant des signatures numériques
Les compromissions de comptes étant de plus en plus fréquentes de nos jours, il est préférable de conserver une copie locale des messages de grande importance ou de grande valeur en les exportant sur votre machine.
En outre, vous pouvez améliorer leur sécurité en les chiffrant localement.
Conseil n° 10 : Valeur juridique des signatures numériques
Une signature numérique peut être utilisée pour tenir quelqu’un responsable en tant qu’auteur d’un certain message. Toutefois, la valeur juridique précise des signatures numériques dépend de l’endroit où la signature a été apposée et des lois locales.
Néanmoins, certaines conditions doivent toujours être acceptées avant d’utiliser les signatures numériques dans un contexte juridique. L’un des problèmes est la possibilité que la clé privée du signataire soit compromise. Que faut-il faire dans ce cas pour vérifier s’il s’agit d’une compromission réelle ou délibérée ?
Remarque : si vous ne souhaitez pas la non-répudiation dans des cas exceptionnels, utilisez des systèmes basés sur l’authentification dénonçable!
Dernier mot sur les signatures numériques
Voilà qui conclut ce guide sur les signatures numériques !
Les signatures numériques OpenPGP sont largement utilisées car elles simplifient le traitement de la clé publique de l’expéditeur, éliminant ainsi la nécessité d’une validation par une autorité de certification centralisée, comme l’exige l’ICP. Chez Mailfence, nous avons simplifié le processus de signature numérique. Si vous utilisez les meilleures pratiques de signature numérique OpenPGP mentionnées ci-dessus, vous tirerez davantage parti de votre utilisation de la signature numérique.