This post provides details over the SSL/TLS certificate for the Mailfence blog.
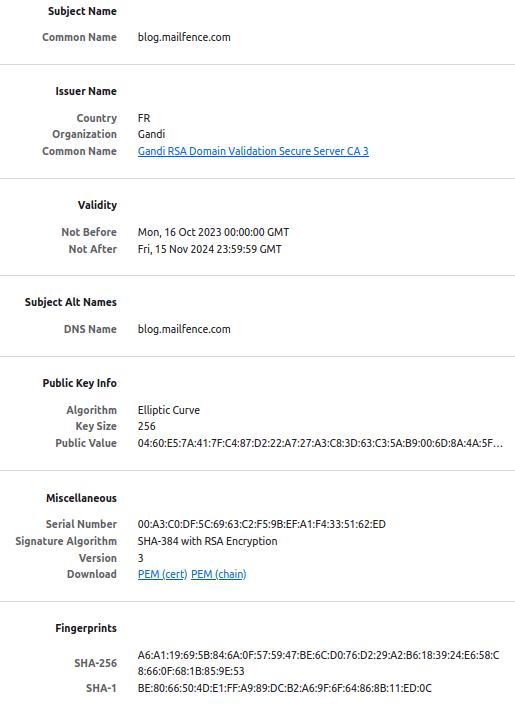
A modern browser should automatically check the validity of the Mailfence blog SSL/TLS certificate and alert you if it detects something untrustworthy. In case an adversary succeeds in spoofing Mailfence blog (using a rogue SSL/TLS certificate), you will still be able to detect such an (AiTM) attack by manually checking Mailfence blog SSL/TLS certificate fingerprints.
The Mailfence blog SSL/TLS certificate fingerprints/thumbprints (valid until 15/November/2024) are:
SHA1 fingerprint:
BE:80:66:50:4D:E1:FF:A9:89:DC:B2:A6:9F:6F:64:86:8B:11:ED:0C
SHA-256 fingerprint:
A6:A1:19:69:5B:84:6A:0F:57:59:47:BE:6C:D0:76:D2:29:A2:B6:18:39:24:E6:58:C8:66:0F:68:1B:85:9E:53
If this matches what you see in your browser, then you know you are communicating with the right Mailfence blog website and using the correct public key to encrypt your sensitive information and only Mailfence blog can decrypt it.
Next update date: November 2024
Guidelines:
- For Chrome:
- Click on the lock button in front of the URL.
- Click on the Certificate.
- In Details tab, show All and verify the Thumbprint matches the one above (SHA1).
- For Firefox:
- Click on the lock button in front of the URL, then Connection secure and click on More Information.
- Go to Security and click on View Certificate.
- In General, verify the Fingerprints (SHA1 & SHA-256) matches the one’s above.
- For Safari:
- Click on the lock button in front of the URL.
- Select Show Certificate, in Details scroll to the bottom of the page.
- Verify the Fingerprints (SHA1 & SHA-256) matches the one’s above.
Note: Make sure, in your browser, you are looking at the leaf certificate (blog.mailfence.com). This certificate does not cover mailfence.com and kb.mailfence.com domain names.
At Mailfence – a secure and private email service, we believe in following good security practices, to contribute in providing you a secure and private email solution.