Ransomware, Phishing, Trojan horses … We live in a world where cyber threats are becoming more present and more sophisticated. Data theft, reputational damage, extortion, espionage, and data destruction, … We can no longer ignore the risks we face daily. You definitely need to take some steps to protect your computer from hackers. We have gathered some essential tips you should consider learning how to protect your devices and keep them safe. Don’t worry: you don’t need to be a cybersecurity expert to understand what our secure hacks are all about.
How to protect your computer and/or your smartphone or tablet from hackers
First, we’d like to stress the importance of the physical security of your devices. Lock your computer or smartphone when you don’t use it! Needless to say, the first step to protecting your device is to never leave it unattended. Also, disable lock-screen notifications and Bluetooth. Thieves could use them to intrude into your device’s system. Protecting your device against physical theft is equally important as our following tips.
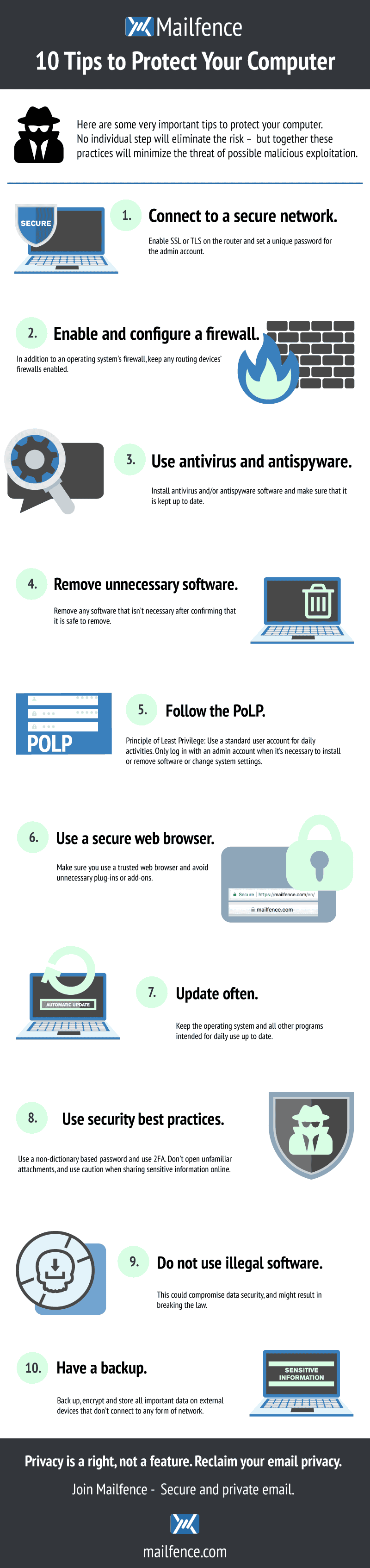
#1 Connect to a Secure Network
Being connected to the Internet could give attackers access to your computer. So make sure to connect to all the websites using SSL/TLS, and harden the devices that come with overly permissive factory-default configurations e.g., IoT devices, routers, etc. – and be sure to secure them.
#2 Enable and Configure a Firewall
A firewall is a device that controls the flow of information between your computer and the Internet, similar to a router. It prevents the disclosure of your personal data by creating a gateway. It will also warn you in case malicious individuals try to break into your computer system.
Most operating systems include a built-in firewall (Windows and macOS have theirs), as do the majority of home routers. This means you shouldn’t have to worry about setting up one, as your device is already protected. But you can strengthen your computer security by creating a strong password that will lock your firewall against any attempt to disable it (Check your Wi-Fi operator guidelines for more information).
#3 Use Antivirus and Antispyware
Installing antivirus and keeping it up to date is a critical step in protecting your computer. Likewise, install an antivirus app on your phone. Be sure to keep them updated.
But antivirus is not a magic tool capable of erasing all threats. In fact, this software is based on a database of already known malware, listed in an internal registry (most often, antivirus updates aim to add new entries – i.e. newly discovered viruses – to this registry).
This means that they are unable to recognize a brand-new malware. So bear in mind, using an antivirus is not a silver bullet. It will not exempt you from applying other preventive measures.
Spyware is a malevolent software designed to monitor your employees’ activities on their computers to gather clues helpful to steal data. The software aims to spy on the company to obtain important secret information such as patents or contracts.
Most big cybersecurity brands’ antivirus tools usually embed anti spyware. If it’s not the case with yours, get one to prevent hackers from stealing information.
#4 Remove Unnecessary Software
Intruders can attack your computer by exploiting software vulnerabilities. Consequently, the less software you have, the less vulnerable your computer will be. Therefore, remove any unnecessary software after confirming that it’s safe to remove. Likewise, disable non-essential services and cancel unnecessary default features to eliminate several opportunities for attack.
#5 Follow the PoLP (Principle of Least Privilege)
In most instances of a malware infection, the malware can operate only under the rights of the logged-in user.
To protect your device and minimize the impact the malware can have if it successfully infects your computer, consider having two kinds of user accounts :
- A standard account with the minimum of features for day-to-day activities;
- An admin one with full operating privileges on the system you’ll log in to when you need to install or remove software or change system settings on your computer.
#6 Use a Secure Web Browser
Web browsers installed on new computers usually don’t have secure default settings. Therefore, securing your browser is a critical step in improving your computer’s security as more and more attacks take advantage of web browsers. Make sure you use a trusted one (why not DuckDuckgo?) and avoid unnecessary plugins/add-ons.
#7 Update often
Most software vendors release updates to patch or fix software vulnerabilities, flaws, and weaknesses (bugs) in their software. And very often, the hacking of the software exposes these flaws. To prevent hacking, it is therefore crucial to download updates as soon as possible.
Vulnerabilities can also be present in the firmware. A firmware is a utility software designed to provide secondary functionalities to your devices (such as allowing your device to connect to any type of printer, or to support a microphone or headphones).
Enable automatic updates whenever possible, so that you won’t have to think about it.
#8 Use Security Best Practices
- Only create strong and unique passwords
The password is the first defence line against intrusions, and is also the least expensive tool to protect your device and the easiest to set up. But this will be effective only if you follow a few basic rules. For more tips on passwords, you can read this article on password best practices. - Beware of phishing and ransomware attacks
Education is the best defence to protect your computer and your phone against phishing or ransomware attacks and to stop hackers on your computer. Read our articles about Social Engineering (phishing, spear phishing, whaling, smishing, and vishing) and learn how to recognize and avoid these techniques. Follow our Email security and privacy awareness course and spread the word! - Use two-factor authentication
Two-factor authentication (or 2FA) works as a second layer of protection after your password. Many websites will offer to use it to secure your account and restrict its access to you. Sure, 2FA adds some delay to your connection, but the benefits are enormous.
#9 Do Not Use Illegal Software
It might compromise your data and your computer security, and even break the law.
#10 Have a Backup
Use backup software to schedule many backups a week, depending on your volume of computing activities. Include all devices and software you use in your backup perimeter, and make at least two copies :
- The first one on an external hard drive (hard disk, USB key, NAS…) ;
- A second one on a cloud storage platform such as Mailfence documents.
Ideally, you could add a third one on another external hard drive to be stored externally to protect your files from any disaster that may affect your home or company.
If it’s too sensitive, avoid keeping it in your device.
Additional tips to protect your computer and other devices
#11 Elaborate your Disaster Recovery Plan
What would you do if your company was hit by a disaster tomorrow morning (consider a fire or ransomware intrusion)? Are you ready for this kind of scenario? Do you accurately know what you would have to do to prevent more damage and restart your business despite the loss of data or destruction of equipment?
If you’re unsure about the answer to this serious question, consider elaborating your own disaster recovery plan. In the middle of the chaos, you’ll be grateful to have a to-do list to contain the risks, remedy the damage, and reactivate what can be restored.
Designing this type of program is not something that can be improvised, and you may need the help of an IT specialist to set it up and test its validity.
#12 Encrypt your data
Encryption scrambles data and messages, usually using a mathematical key. To get back a readable data or message, the user will need to know this key to decipher it. This system makes all data safe because they become unreadable, meaning they remain private. It’s an effective way to prevent interception for espionage purposes and data theft.
You can also encrypt your web traffic using a Virtual private networks (VPN). It will encrypt your data before its transmission so that nobody can read it during its transit. The relevant data will only be deciphered at its destination (the website/software you’re communicating with).
Also, a website using SSL/TLS will encrypt the data you exchange with it, so that malicious individuals cannot intercept it. You can recognize these websites thanks to the padlock they display in your browser’s search bar when you’re connected to them. Ensure to be connected to the secure version of a website by activating the HTTPS Everywhere extension. It will redirect you seamlessly to the SSL-secured version of a website if it exists.
#13 Get a professional secure email
Last but not least, do not forget your email is the favourite gateway for hackers to infect your devices with malware. Mailfence is an encrypted email suite that offers end-to-end encryption, digital signatures and 2FA. It also includes a calendar with polls and groups management, an instant messaging service and a document storage and management tool. All these features are secure, meaning your data are protected.
And you know what? The starter plan is free, meaning you can learn to leverage all our security tips at your own pace without having to pay. So don’t look further: sign up for a free Mailfence account now and start improving the security of your devices today !